This guide illustrates how to install and configure the Fletch SCIM and SAML integration app in Okta.
The Fletch app enables your organization to use SCIM to provision your Okta users in your Fletch workspace and enables your users to use SAML to sign on into Fletch from Okta.
Features
The current features supported by the Okta SCIM and SAML integration for Fletch are:
- Push New Users: Assigning Okta users or groups to the Fletch app will get their access provisioned in your Fletch workspace.
- Push Profile Updates: Updates made to the user's profile through Okta will be synced to your Fletch dataspace.
- Push User Deactivation: Removing a user's access to the Fletch app in Okta will deactivate the user in your Fletch workspace and deprovision their access.
- Reactivate Users: Reactivating a user in Okta will reactivate the user in Fletch.
- Sign in Users: Allowing a user in Okta to sign into your Fletch workspace.
Prerequisites
Ensure that you have the following before you start configuring Okta:
- An Okta account with admin privileges.
- The following configuration information:
- SCIM 2.0 Base Url
- SCIM Username
- SCIM Password
- SAML Single Sign On URL
- SAML Audience URI (SP Entity ID)
Enable and Configure the SCIM integration in Okta
- Log in to Okta and add the Fletch SCIM and SAML application.
- From the application page, click on the 'Provisioning' tab at the top and then click on the 'Configure API integration' button.
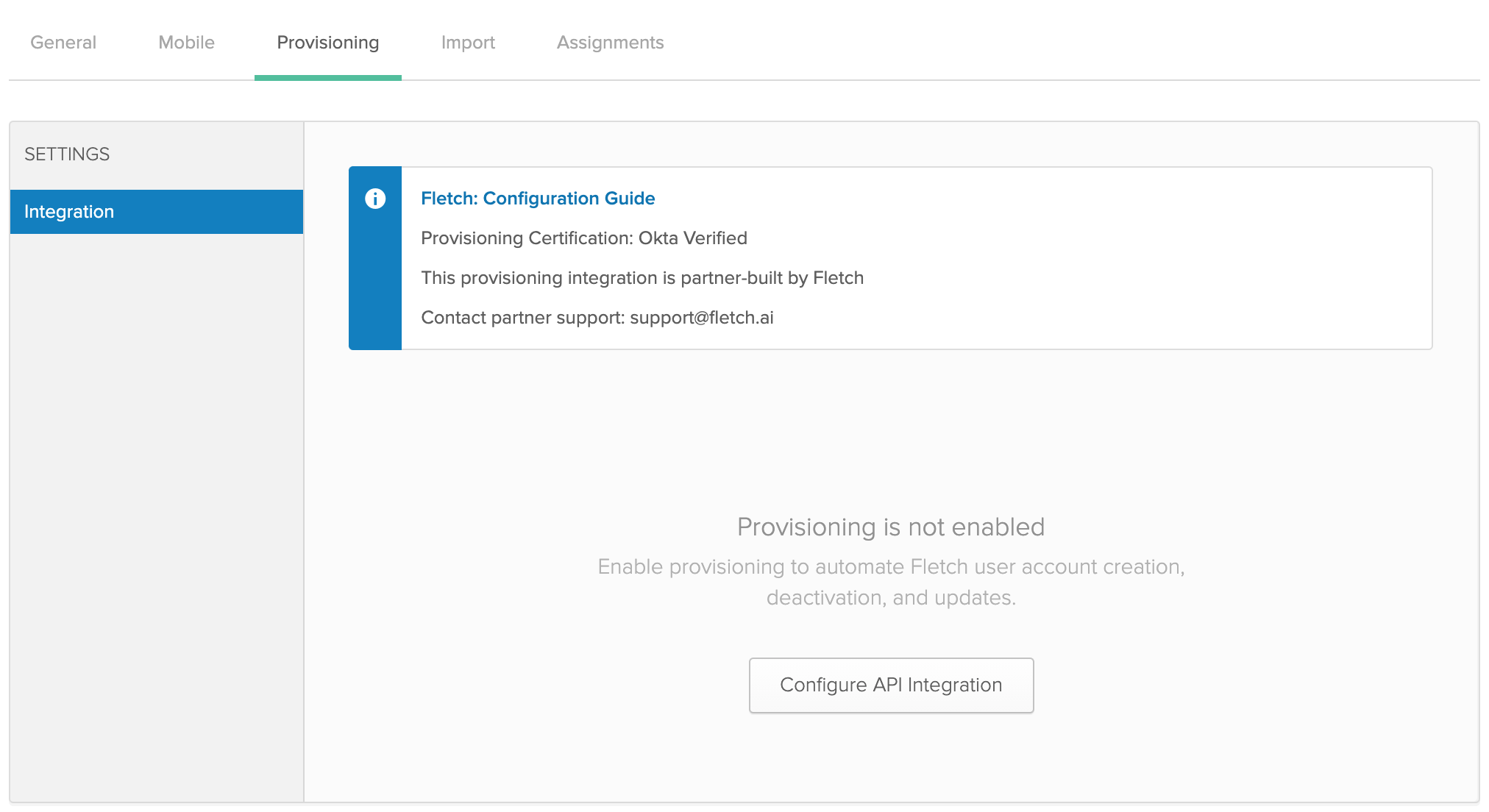
- Select the 'Enable API integration' checkbox.
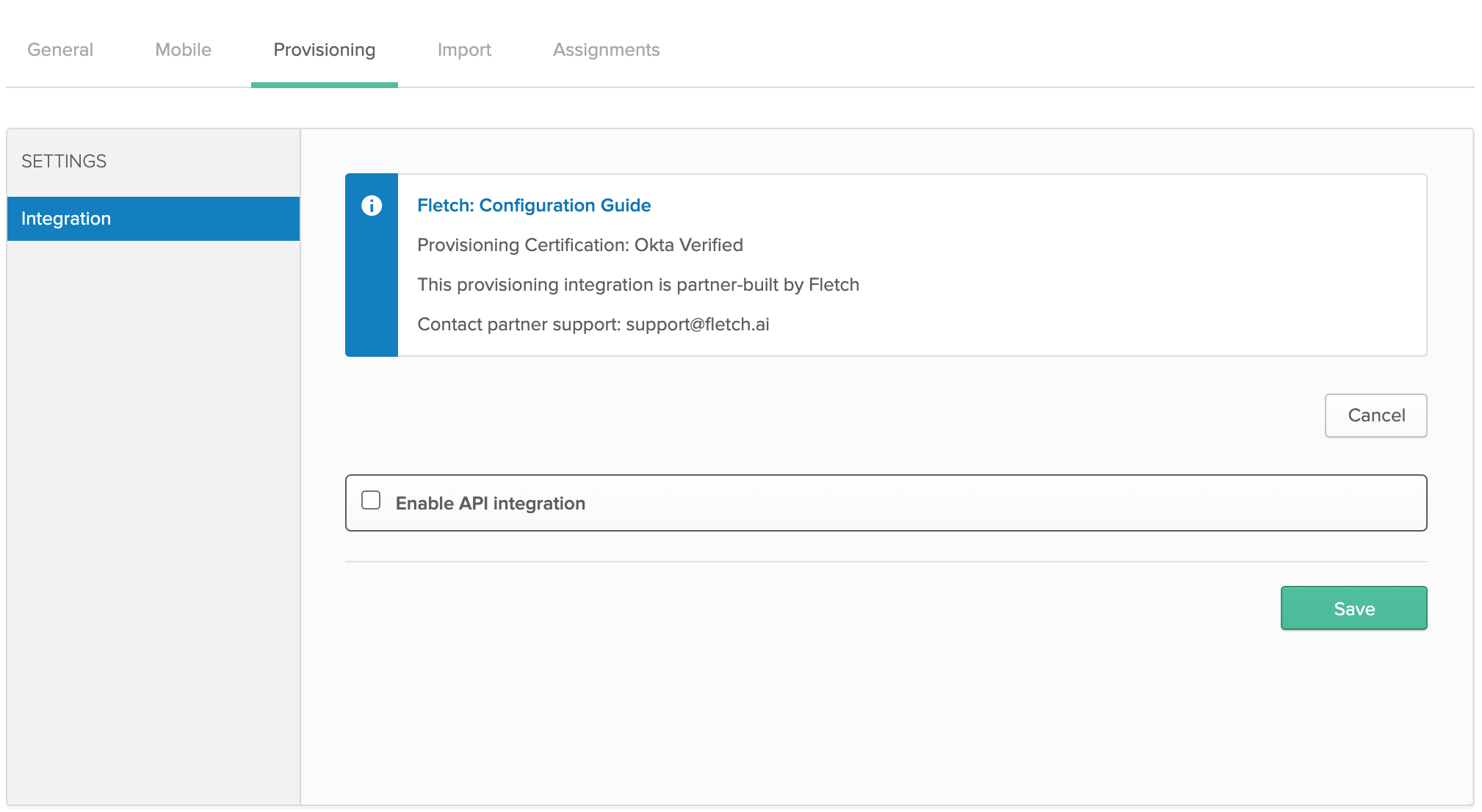
- Enter the 'SCIM 2.0 Base Url', 'SCIM Username', and 'SCIM Password' information for your Fletch workspace you received from your Fletch representative.
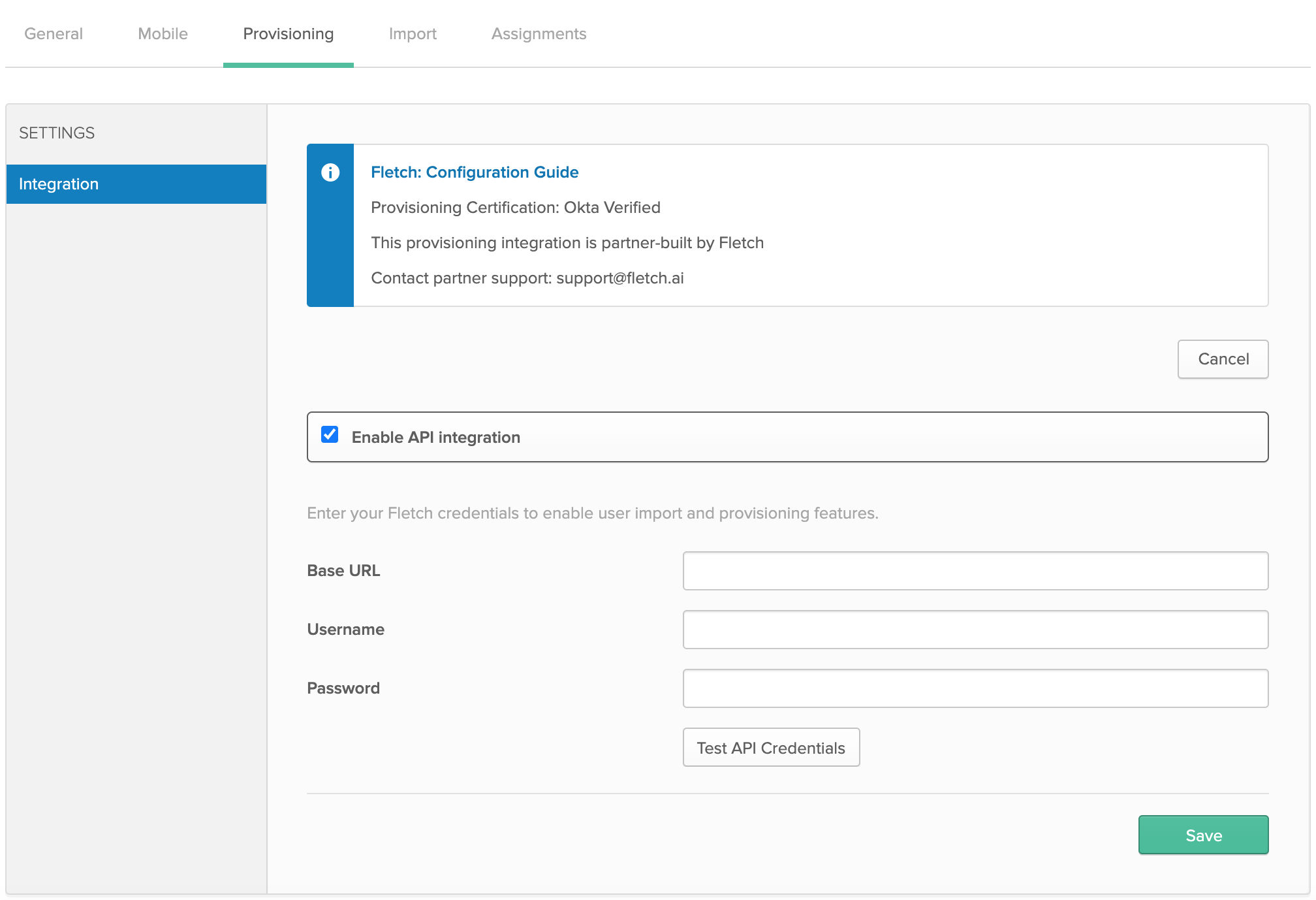
- Click on the 'Test API Credentials' button.
- If the test passes, click on the 'Save' button.
- On the left hand side, cIick on the 'To App' shortcut under 'Settings'.
- Click on 'Edit' and select 'Enable' for these options: Create Users, Update User Attributes, and Deactivate Users.
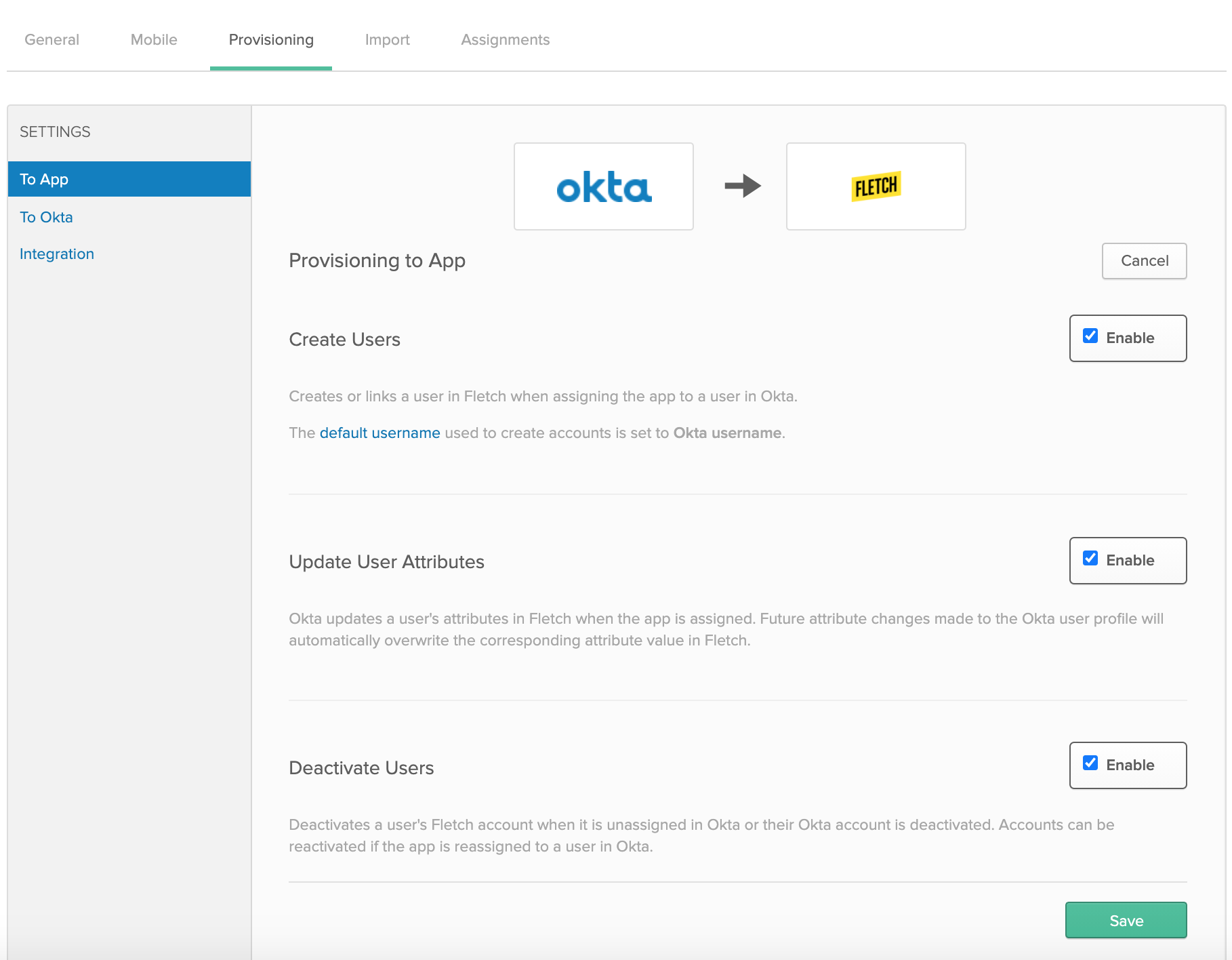
- Click on the 'Save' button to apply the SCIM integration settings.
Configure the SAML integration in Okta
- From the application page, click on the 'Sign On' tab at the top and then click on 'Edit' in the 'Settings' section.
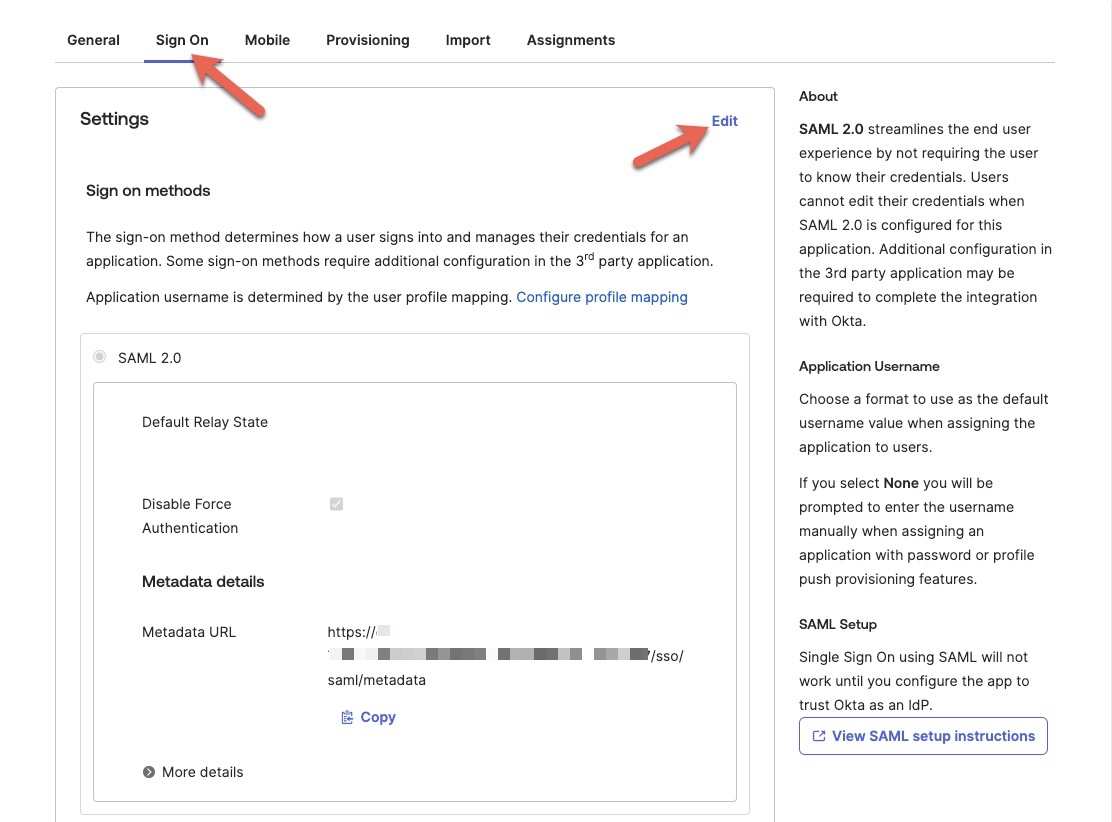
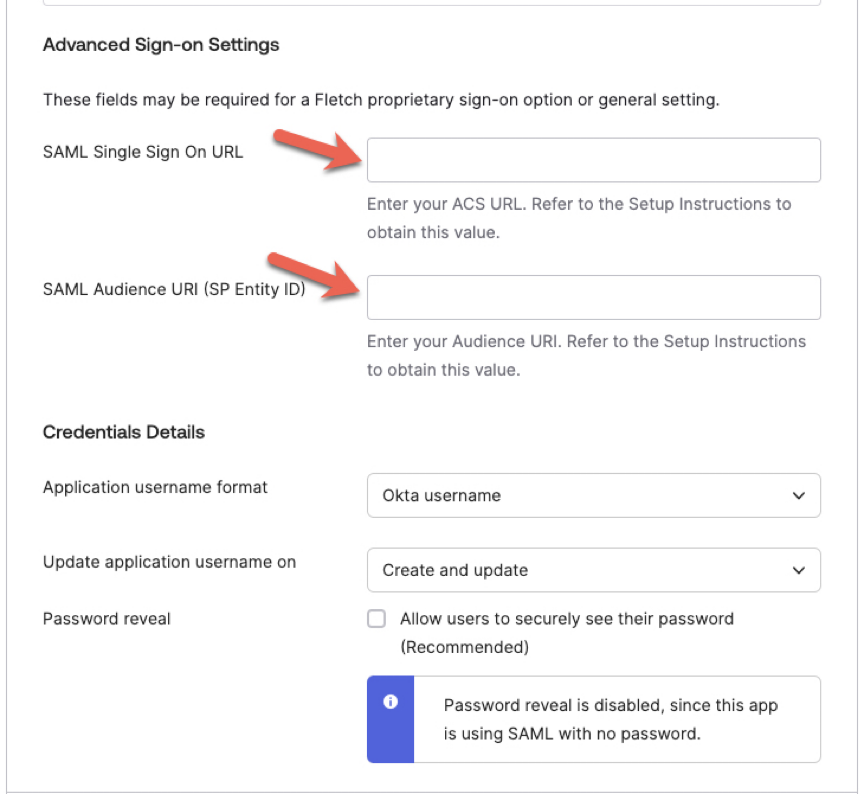
- Scroll down to the 'Advanced Sign-on Settings' section and enter the 'SAML Single sign-on URL' and 'SAML Audience URI (SP Entity ID)' information for your Fletch workspace you received from your Fletch representative.
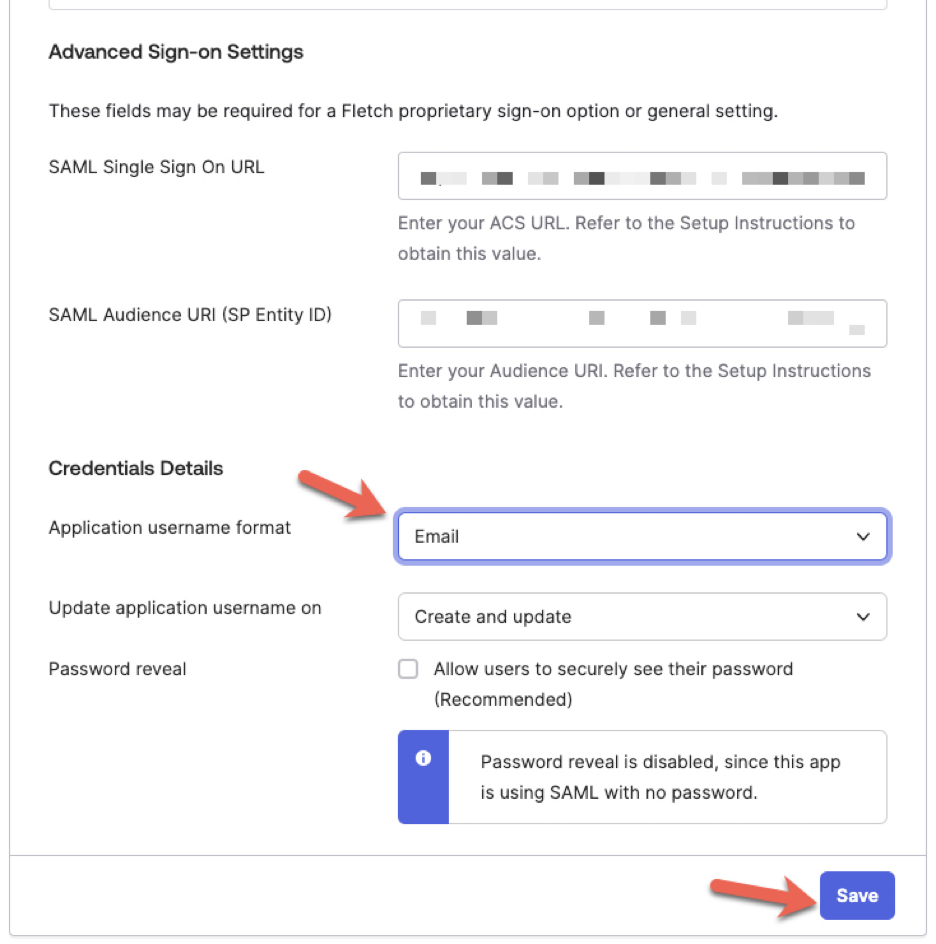
- Scroll down to the 'Credentials Details' section. Select 'Email' as the 'Application username format', then click on the 'Save' button.
Provide the Okta App’s IDP metadata URL to Fletch
With SAML, Fletch is acting as your Service Provider for authentication.
To establish a trust relationship between your Fletch workspace and the Fletch Okta SCIM and SAML app, the 'IDP metadata URL' value of the app needs to be populated in the Fletch workspace.
- From the application page, click on the 'Sign On' tab at the top.
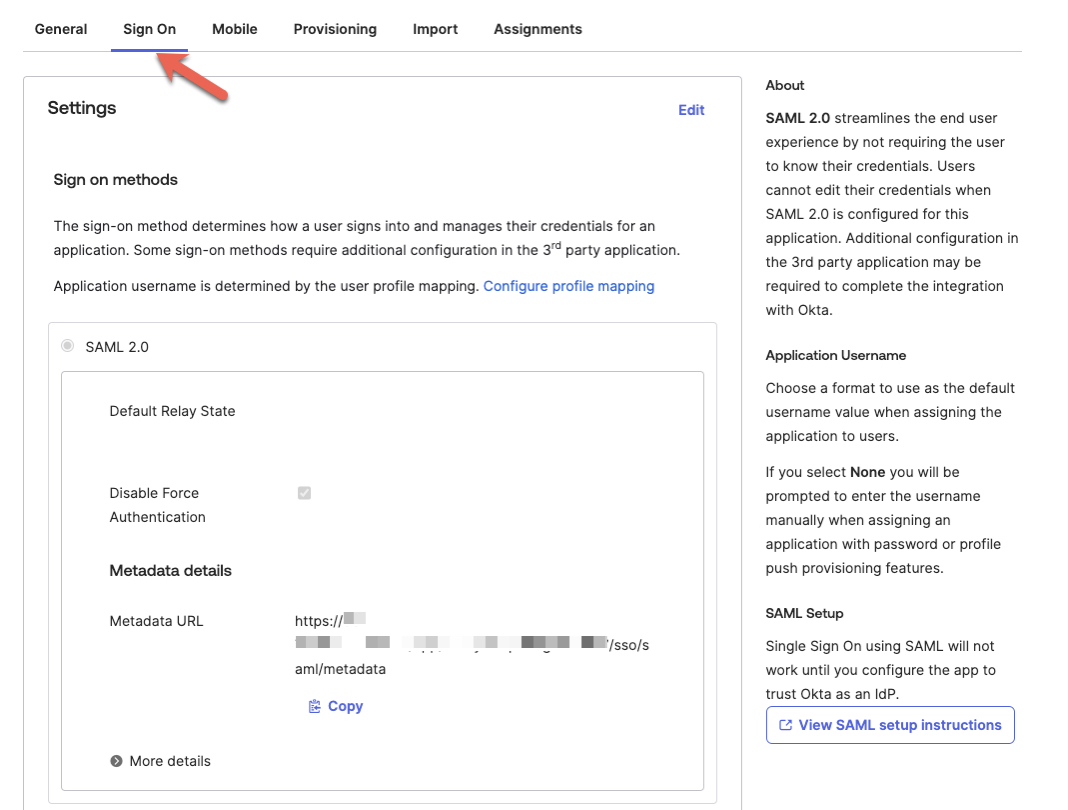
- Click on the 'Copy' button in the SAML 2.0 section to copy the value of your 'IDP Metadata URL'.
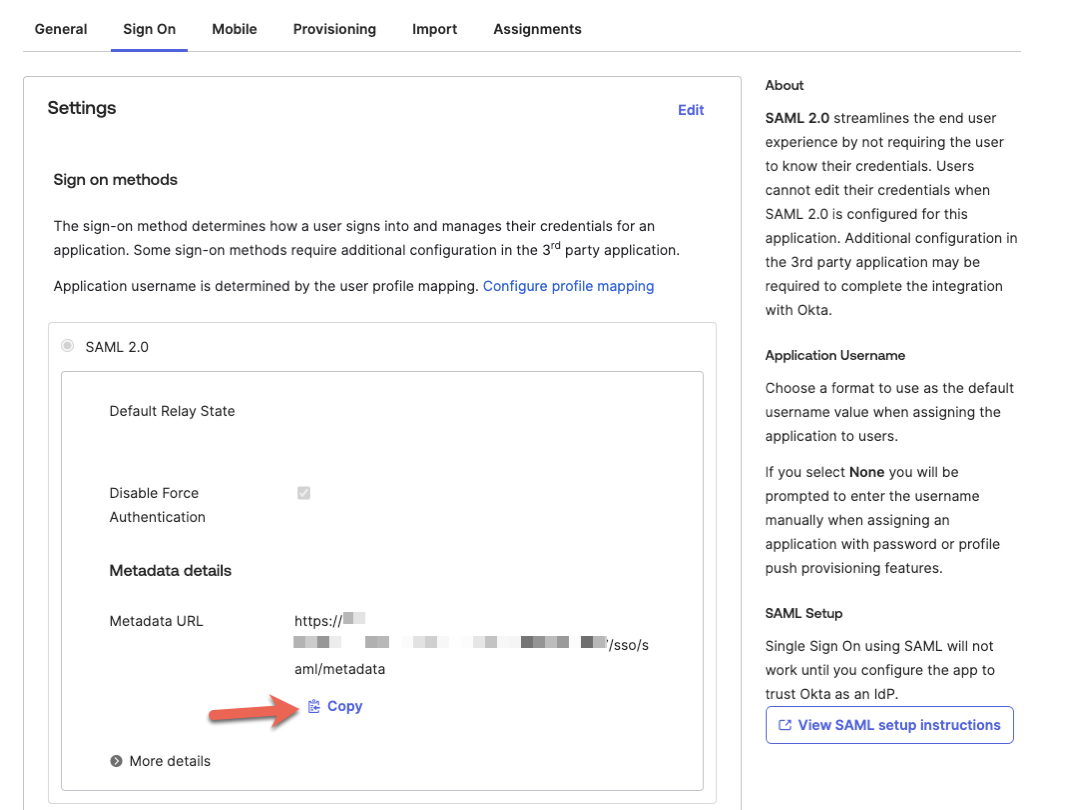
- Send the IDP Metadata URL value securely to your Fletch representative so that Fletch can enable SAML login for your Fletch workspace.
Assign users or Groups to the Fletch application in Okta
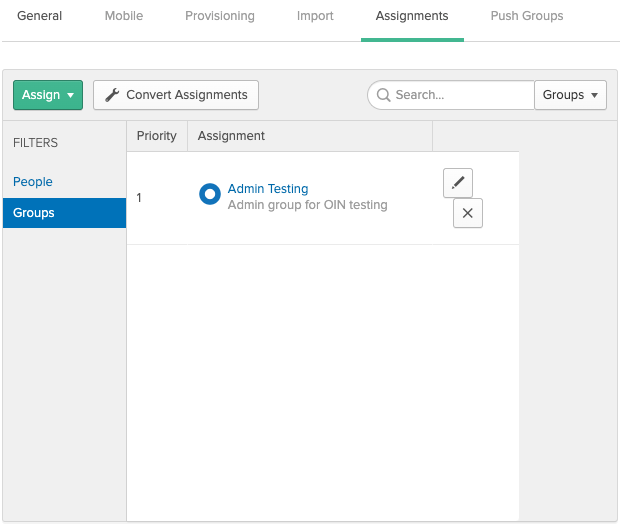
- From the application page, click on the 'Assignments' tab at the top.
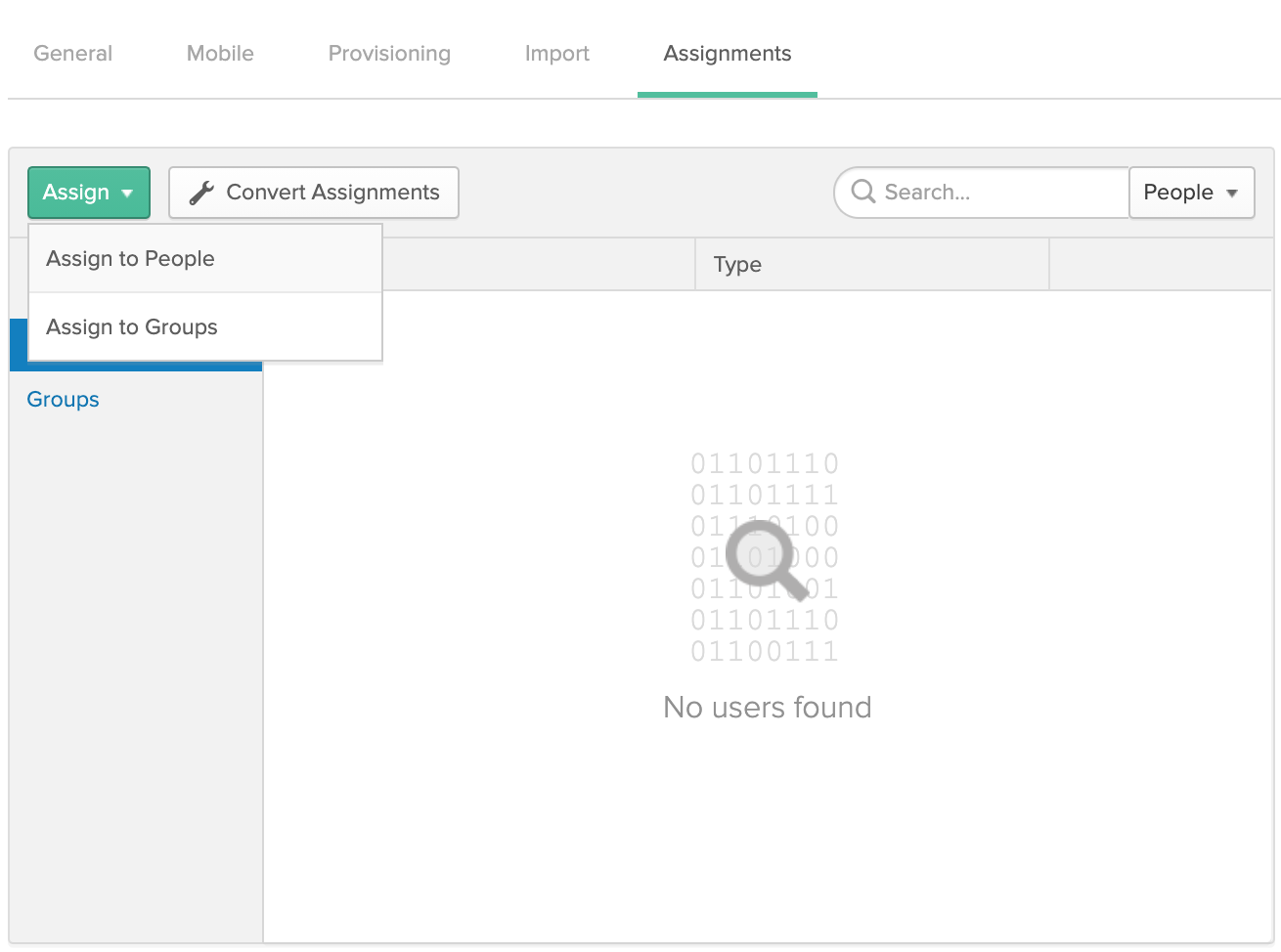
- Click on the 'Assign' drop-down in the top, left hand corner, then choose either 'Assign to People' or 'Assign to Groups'. Select the user or the group you'd like to provision access to Fletch.
In the example below, the group assigned is the 'Admin Testing' group.
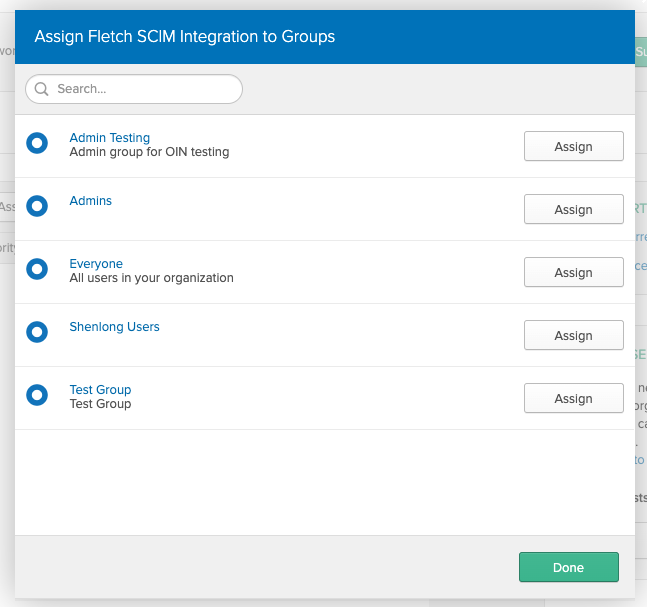
- You'll see the dialog below to assign roles to the users.
Fletch supports the ‘user’ and ‘admin’ roles.
Click on the 'Add Another' button, input the name of the desired role, then click on the 'Save and Go Back' button.
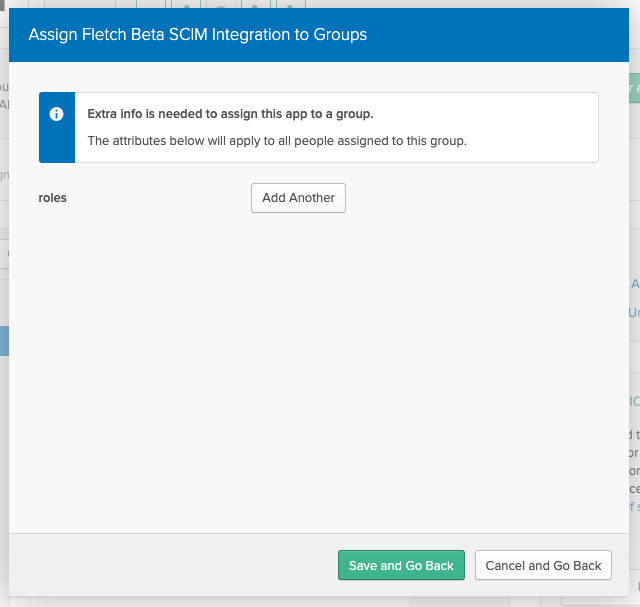
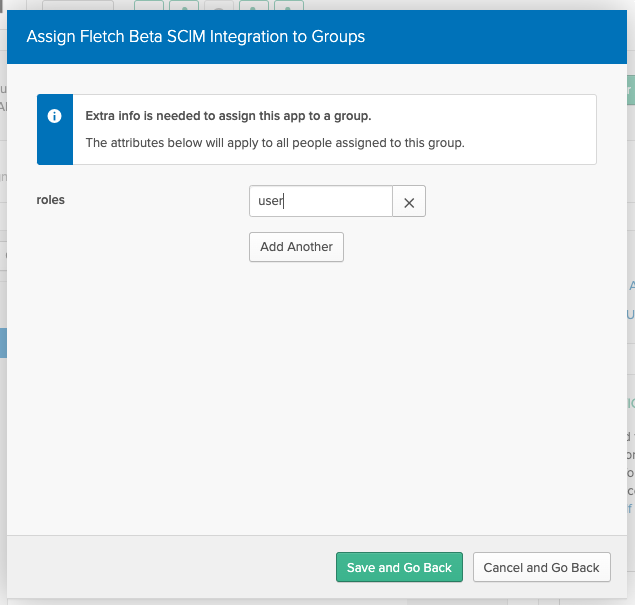
- Click on the 'Done' button: the users in the selected group will be provisioned in the Fletch workspace with the specified role and will have the ability to sign on into the Fletch workspace from Okta.
Known Issues/Troubleshooting
There are no known issues at this time.

