Product

Kenisha Liu
Dec 5, 2023
Vulnerability management is a critical component of cybersecurity to address cybersecurity vulnerabilities in a company’s organization. Let’s dive into what vulnerability management is.
What is vulnerability management
Vulnerability management is the process of continually discovering, evaluating, reporting, and resolving cybersecurity vulnerabilities across endpoints and systems.
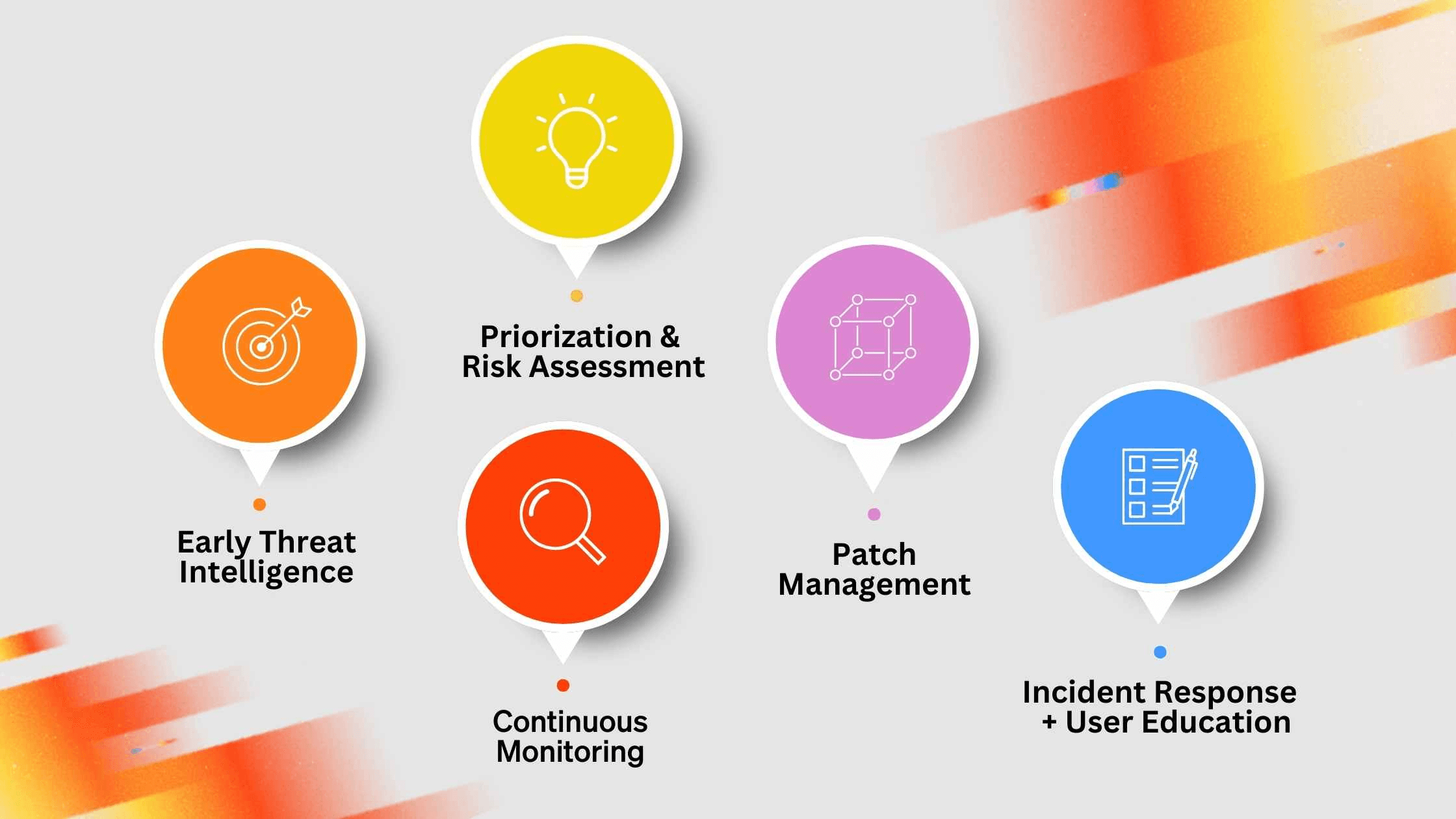
Effective vulnerability management is proactive, contextual, and continuous. Though it may differ at every company, a vulnerability management program should include the following:
Continuous Monitoring: Organizations continuously monitor for vulnerabilities present in their systems. This should involve regular scans via vulnerability scanners at least every 7 days.
Early Threat Intelligence: While continuous vulnerability scanning covers the threats in-house, it’s oftentimes not timely or relevant information. Add early and timely threat intel to get ahead of vulns that are actively being exploited by bad actors even before scanner picks them up.
Prioritization and Risk Assessment: Time is of the essence in cybersecurity. Effective vulnerability management has a heavy emphasis on prioritizing vulnerabilities based on their severity and potential impact so you focus on the most critical threats. This is another benefit of timely and correlative threat intel.
Patch Management: Once vulnerabilities are identified, organizations need to apply security patches and updates to remediate vulnerabilities quickly. Researching what to do takes cycles — advice needs to be contextual, timely, and integrated.
Compliance Requirements: Organizations should be monitoring their compliance status to be aware of their security posture. Effective vulnerability management can complete compliance requirements related to regular assessments and reporting.
Incident Response Planning + User Education: Organizations should have strategies for quickly responding to and educating users to mitigate the impact of security incidents related to vulnerabilities.
Vulnerability management vs vulnerability assessment
A common point of confusion is vulnerability management and vulnerability assessment. Vulnerability management and vulnerability assessment, while related, are different concepts in the realm of cybersecurity.
A vulnerability assessment is one part of vulnerability management. It is the process of identifying, quantifying, and prioritizing cybersecurity vulnerabilities in a system, network, or application.
The primary goal of a vulnerability assessment is to provide an organization with a comprehensive understanding of its security posture. And is often conducted on a regular basis.
Vulnerability management, on the other hand, is a broader, ongoing process that goes beyond the identification of vulnerabilities. It encompasses the entire lifecycle of addressing and mitigating vulnerabilities effectively beyond the initial discovery.
Advancements in vulnerability management
The current way vulnerability management is done is limiting because it is largely dependent on manual work and vulnerability and EDR tools. Vulnerability management should be proactive and contextual, allowing you to live ahead of threats.
With the onset of artificial intelligence this has been made possible in three major ways.
Early threat intelligence with AI: Artificial intelligence and machine learning is paving the way for early threat detection. AI can now scan and index the entire threat landscape to show you the vulnerabilities that are active and exploited in the threat landscape.
Correlation engine with AI: AI can now automate the tricky threat correlation work to personalize the threat landscape to each company. With every cybersecurity vulnerability prioritized based on your susceptibility, security teams can focus on what’s most pressing.
Generative threat mitigation advice and user education: Natural language processing is evolving to be able to offer personalized advice to users on the threats and vulnerabilities they have and how to mitigate and patch them.
Learn more about the AI advancement of vulnerability management here.
Takeaway
Vulnerability management is a pillar of cybersecurity that seeks to address and mitigate vulnerabilities. However, the way vulnerability management systems are done today has largely remained static boxing security teams into a process that revolves around a lot of manual work and confusion. With the help of artificial intelligence, vulnerability management systems can become much more contextual and proactive. Fletch offers security teams the chance to improve and automate their vulnerability management system, namely with prioritized vulnerability and malware tool alerts and early threat detection.
Fletch cuts out the manual work and prioritizes your cybersecurity vulnerability and EDR alerts for you. Sign up now.


