Product

Kenisha Liu
Aug 18, 2023
Everybody has that one cybersecurity buddy at some big tech company who claims they run a tight ship. And yet their company has recently suffered a breach…
How can that be?
Maybe they had employees overseas using public WiFi. Email accounts get compromised. They get “internal” memos with malicious documents. And suddenly there's a breach of important systems.
Or perhaps they saw an old vulnerability from 2010 that they ignored, unaware that it has reemerged as an attack vector for their industry today.
Case in point? Threat exposure is much broader than most people realize. It has to go beyond reactive vulnerabilities and malware triage. So people actually know what’s coming, and have a handle on the threats that are targeting your people. Most companies are shooting in the dark trying to guess what threats are relevant to them.
It’s humanly impossible to get ahead of these threats manually. That’s where Fletch Correlated Threats come in.
What are Correlated Threats?
Correlated Threats take the active threats (known as Major Threats in Fletch) and correlates them with the your data, simplifying the threat landscape to only what matters.
A little skeptical? We don’t blame you. It’s a new way of doing cybersecurity.
Correlated Threats is a culmination of the work Fletch does for you. We’ve spent years perfecting our AI engine to automate the manual labor that bogs down cybersecurity teams and transform cybersecurity so you can live ahead. Let us break it down.
How does it work?
There are two components of Correlated Threats.
Major Threats: The threat landscape consolidated into the active threats over the last 30 days.
We scan the entire threat landscape, processing 10,000+ articles and 100,000+ indicators daily. Then our AI engine analyzes threats based on the collective wisdom of the cybersecurity community to provide you with the few threats that matter at any given moment. You’ll get this intel before any other source.
Learn more about Major Threats.
Your Data: We build you a comprehensive, in-depth profile with data sets you’ve never had easy access to until now.
External Tech: A daily scan of your perimeter. Get a continuous white box pentest to check that compliance box. And stay ahead of the threats customers would otherwise see and judge you on.
Internal Tech: When shadow applications or suspicious software is being used, be on top of the vulnerabilities, and notify less technical colleagues before it’s an issue.
Industry: When threats target your industry with tactics like phishing that sneak past vulnerability scanners and EDR alerts, prepare the company and evade danger.
Geo: When remote workers change location you won’t be surprised by the threats targeting them. Know exactly where everyone is and what threats their location exposes your company to.
Vulnerabilities and Malware: Make the most out of your vulnerability scanners and EDR systems to prioritize alerts and offer mitigation advice and ready-to-go communication.
Learn more about the how Fletch monitors your data for you.
Correlated Threats bring it all together.

The benefits of correlated threats
With Correlated Threats you can:
Get focused in the right direction. You only need to look at the threats that matter. (aka threats in your threat feed right now).
Expand your coverage. We take you beyond vulnerability scanners and EDR tools to get insights into a wider breadth of correlations. You’ll never get surprised again when you have every aspect of your organization covered.
Save time and money (on top of making you more secure). Fletch was built by security people for security people. Cybersecurity is a race against time, our Correlated Threats feed allows you to see what matters quickly.
To get this type of in-depth information, you’d need a huge (expensive) team. We’re talking ~50k/month minimum vs our Fletch PRO plan.
Features
The Daily Threat Report
Every day, you’ll get your Correlated Threats at the top of your inbox in your Daily Threat Report.

You’ll have a short list of focused work every morning. Skip the endless busy work of threat research, identifying CVEs or indicators, correlating your findings, and searching for threat mitigation strategies. Out of site, out of mind with correlated threats.
Correlated Threat Feed
The Correlated Threat feed in Fletch will bring you all the threats that target you whether it's your software supply chain or your people. You can get an easy to understand snapshot of all the threats that matter and decide on what to focus on.
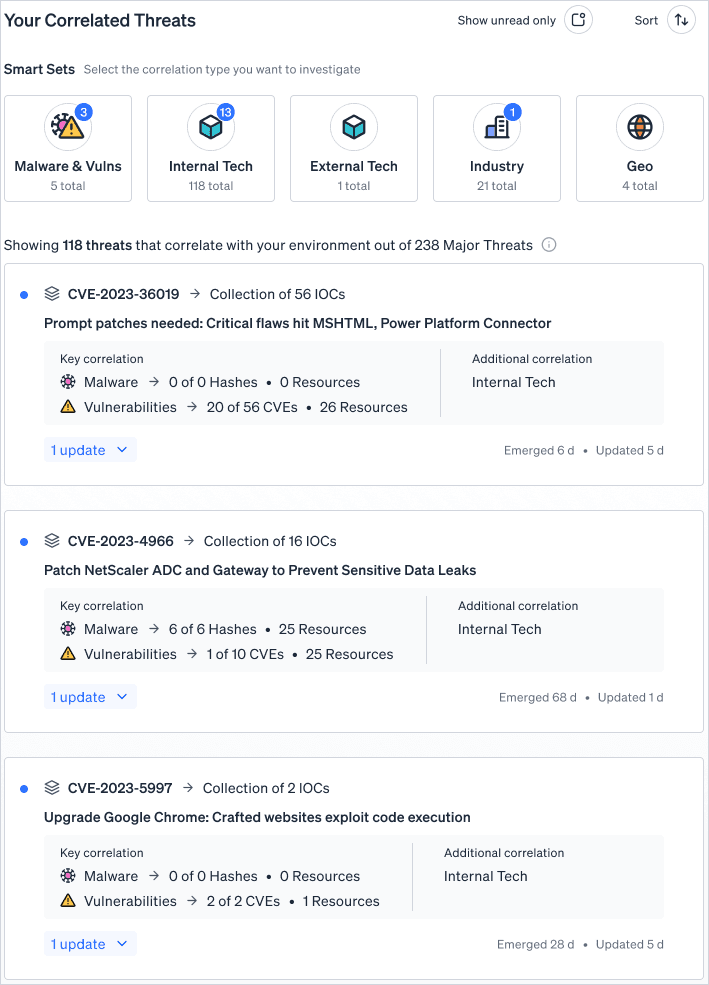
See everything you need to know to prioritize, including:
Threat name or CVE: see what threats are on your horizon.
Naming conventions are based on the following in priority order: (a) the first threat group name (e.g., ransomware group name) associated with the threat (b) the first malware family name associated with the threat (c) first CVE associated with the threat
Data type tags: see exactly why the threat is on your Correlated Threat Feed based on what data it is targettiing.
You’ll see a tags stating either tech exposed, geo targeted, industry targeted, vulnerability detected, or malware detected — or a combination of them
Threat status: see when it is emerging, evolving, or has gone mainstream in real time. Fletch tracks every detail of every threat, so you make better decisions based on the latest evolution of the threat.
Target: see exactly what the threat is targeting below the name. This will include one or more of your geo, industry, or tech.
Notice that threat is targeting Mexico? No worries, you know your coworker isn’t working while abroad. This allows you to quickly prioritize threats so you can make the most out of your time.
When you’re ready to dig into a threat, click into it to open it’s Threat Board. You can see the history of the threat from its inception to now. Get more in-depth about your what's susceptible. Try our beta features. Get expert short-term and long-term advice. And auto generated comms for different audiences so you can quickly educate your people on it.

That way you’re completely covered from the research to the correlation all the way to the mitigation.
Takeaway
Correlated Threats allows you to quickly look at only the threats that matter and determine what to focus on.
You get a full view of the threats targeting like you never had before — bringing 1000’s of threats down to the few to focus on right now. And save a ton of time and money doing it.
Sign up for the Fletch waitlist to start living ahead with your correlated threats.


