Blog
Stories on the latest threats, product updates, and tips and tricks to live ahead of cyber threats.

The 20 most targeted technologies | April
Top List
Jake Trujillo
May 1, 2025

The Task Optimizer Agent is coming soon to public preview to combat alert fatigue in Microsoft Security Copilot
Product
Grant Wernick
Apr 29, 2025

The 20 most targeted technologies | March
Top List
Jake Trujillo
Apr 4, 2025

Overcoming AI's Cold Start Problem with Fletch
Articles
Jake Trujillo
Mar 31, 2025

Introducing Fletch Task Optimizer Agent for Microsoft Security Copilot
Product
Grant Wernick
Mar 25, 2025

The 20 most targeted technologies | February
Top List
Jake Trujillo
Feb 24, 2025

The 20 most targeted technologies | January
Top List
Jake Trujillo
Jan 23, 2025
The 20 most targeted technologies | December
Top List
Jake Trujillo
Dec 18, 2024
The world’s first cyber threat AI, a vertical specific AI for the gnarliest cyber security tasks
Product
Lisa Fong
Dec 12, 2024

Top 10 Cyber Threats to the Computer & Network Security Industry (October 2024)
Top List
Jake Trujillo
Oct 9, 2024

CVE-2024-44204 Threat Guide
Threat Guide
Jake Trujillo
Oct 8, 2024

Automatically prioritize your vuln scanner and EDR alerts
Solutions
Lisa Fong
Oct 7, 2024

Discover risks to your SaaS supply chain
Solutions
Lisa Fong
Oct 6, 2024

Know the threats targeting your industry
Solutions
Lisa Fong
Oct 5, 2024

Is Microsoft Defender good enough? | Fletch Partner
Articles
Jake Trujillo
Oct 3, 2024

Timely compliance controls
Solutions
Lisa Fong
Oct 1, 2024

Cybersecurity education made easy
Solutions
Lisa Fong
Oct 1, 2024
Early threat detection
Solutions
Lisa Fong
Oct 1, 2024
Introducing Fletch’s latest and trending threat lists
Top 10
Jake Trujillo
Oct 1, 2024

CVE-2024-8190 Threat Guide
Threat Guide
Jake Trujillo
Sep 17, 2024

Top 10 Cyber Threats to the Financial Services Industry (August 2024)
Top 10
Jake Trujillo
Aug 26, 2024

Top 10 Cyber Threats to the Computer Software Industry (August 2024)
Top List
Jake Trujillo
Aug 15, 2024

Top 10 Cyber Threats to Healthcare Industry (August 2024)
Top List
Jake Trujillo
Aug 13, 2024

Top 10 Cyber Threats to Government Administrations (August 2024)
Top List
Jake Trujillo
Aug 8, 2024
Understanding AI cybersecurity: How does Fletch’s AI engine work
Articles
Finn Callaghan
Aug 5, 2024

Will cybersecurity be replaced by AI?
Articles
Finn Callaghan
Aug 1, 2024

CVE-2024-36401 Threat Guide
Threat Guide
Finn Callaghan
Jul 31, 2024

FIN7 Threat Guide
Threat Guide
Jake Trujillo
Jul 26, 2024

CrowdStroke Threat Guide
Threat Guide
Jake Trujillo
Jul 22, 2024
APT40 Threat Guide
Threat Guide
Finn Callaghan
Jul 19, 2024

BlastRADIUS Threat Guide
Threat Guide
Finn Callaghan
Jul 12, 2024

FARGO Ransomware Guide
Threat Guide
Finn Callaghan
Jul 10, 2024

CI0p Ransomware Guide
Threat Guide
Finn Callaghan
Jul 5, 2024

RegreSSHion Threat Guide
Threat Guide
Jake Trujillo
Jul 3, 2024
Kinsing Threat Guide
Threat Guide
Finn Callaghan
Jul 1, 2024
UNC5537 Threat Guide
Threat Guide
Jake Trujillo
Jun 26, 2024

TellYouThePass Ransomware Guide
Threat Guide
Jake Trujillo
Jun 17, 2024

Akira Ransomware Guide
Threat Guide
Jake Trujillo
Jun 12, 2024

What is Microsoft Defender | Fletch Partner
Articles
Kenisha Liu
Jun 11, 2024

CVE-2024-24919 Threat Guide
Articles
Jake Trujillo
Jun 3, 2024
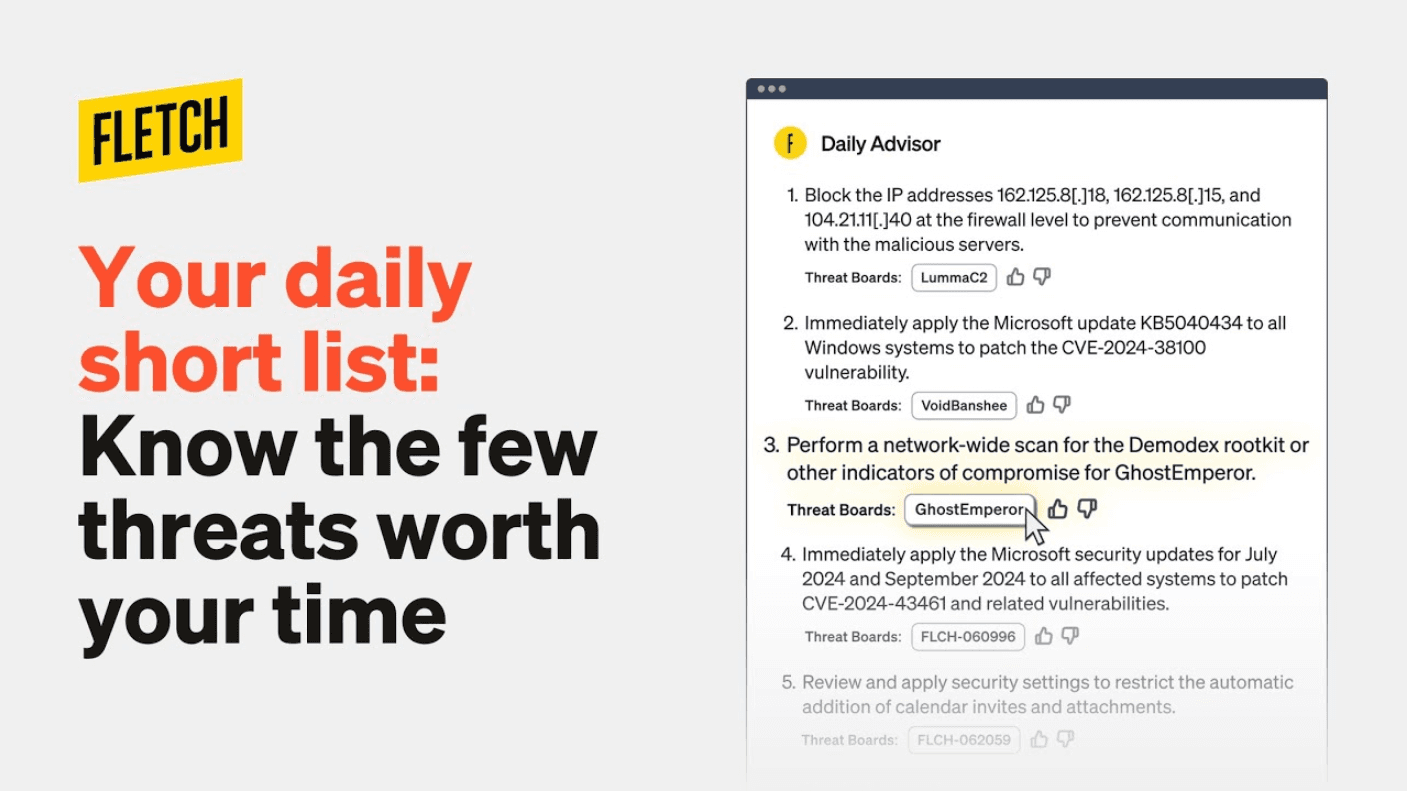
Introducing Daily Advisor
Product
Kenisha Liu
May 30, 2024

Linguistic Lumberjack Threat Guide
Articles
Jake Trujilo
May 29, 2024

Kimsuky Threat Guide
Threat Guide
Jake Trujillo
May 24, 2024

Black Basta Threat Guide
Threat Guide
Jake Trujilo
May 22, 2024

APT28 Threat Guide
Threat Guide
Jake Trujilo
May 16, 2024

ArcaneDoor Threat Guide
Threat Guide
Jake Trujilo
May 7, 2024

Pegasus Threat Guide
Threat Guide
Jake Trujillo
Apr 30, 2024

What is OSINT (Open Source Intelligence)?
Articles
Kenisha Liu
Apr 30, 2024

Sandworm Threat Guide
Threat Guide
Jake Trujilo
Apr 24, 2024

Latrodectus Threat Guide
Threat Guide
Jake Trujillo
Apr 18, 2024

The problem with open source intelligence
Articles
Kenisha Liu
Apr 16, 2024

Cybersecurity platform Fletch issues report on threat trends to be aware of
Articles
Kenisha Liu
Apr 16, 2024

LockBit Threat Guide
Articles
Jake Trujillo
Apr 10, 2024

Revolutionizing OSINT in cybersecurity with Fletch
Articles
Kenisha Liu
Apr 10, 2024

BlackCat Threat Guide
Articles
Kenisha Liu
Mar 23, 2024
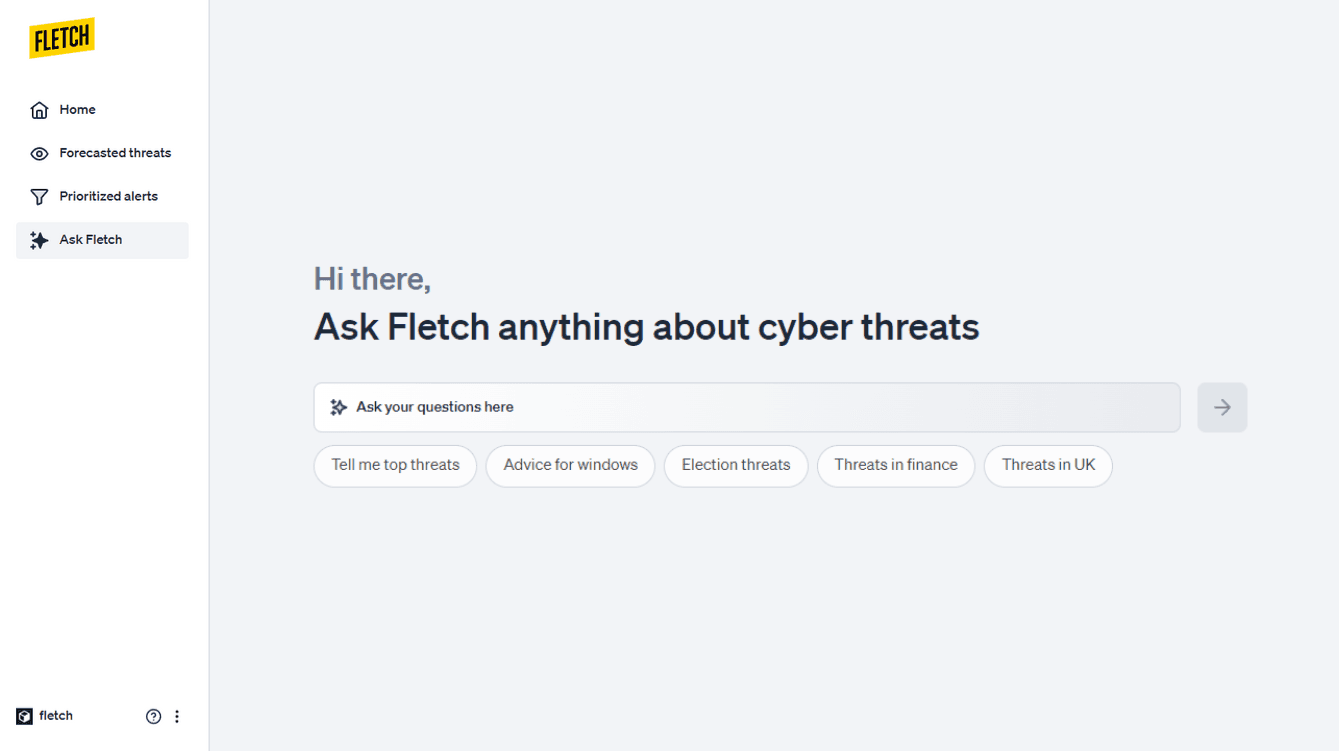
Introducing AskFletch
Product
Kenisha Liu
Mar 11, 2024
XZ vulnerability analysis: year-by-year timeline and impact
Threat Guide
Kenisha Liu
Mar 4, 2024
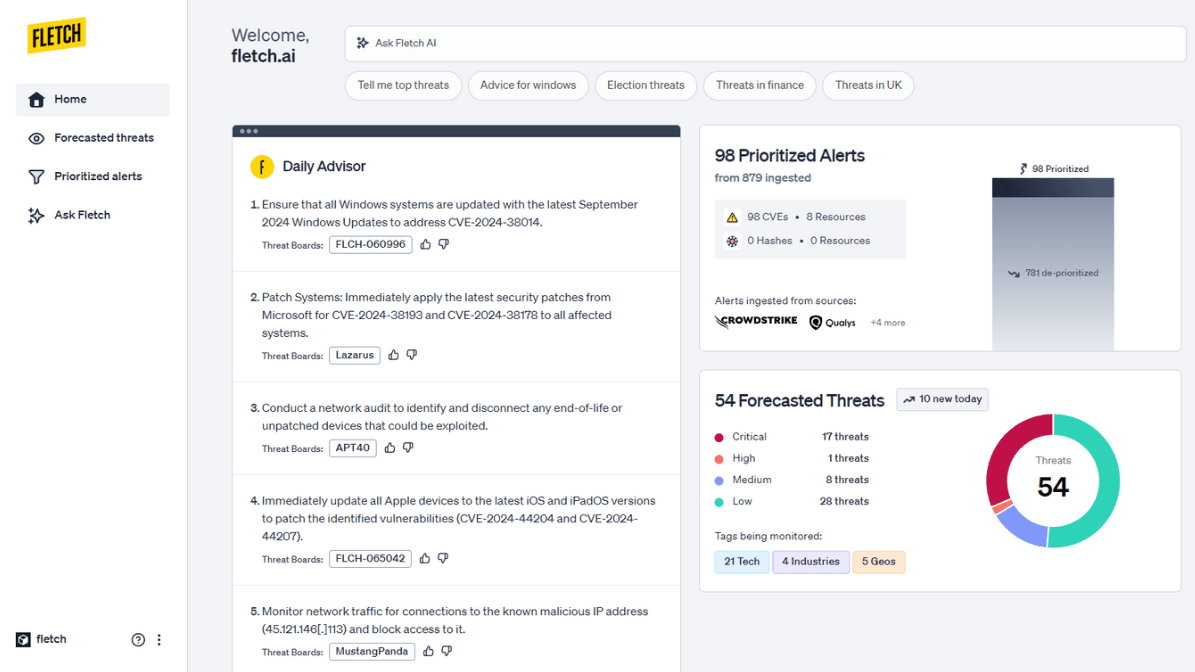
Hours of work now seconds in Fletch | 2024 product updates
Product
Kenisha Liu
Feb 27, 2024

The problem with threat detection
Articles
Kenisha Liu
Feb 7, 2024

What is threat detection
Articles
Kenisha Liu
Jan 31, 2024

The problem with vulnerability management
Product
Kenisha Liu
Jan 9, 2024

Fletch getting started guide
Product
Kenisha Liu
Dec 19, 2023
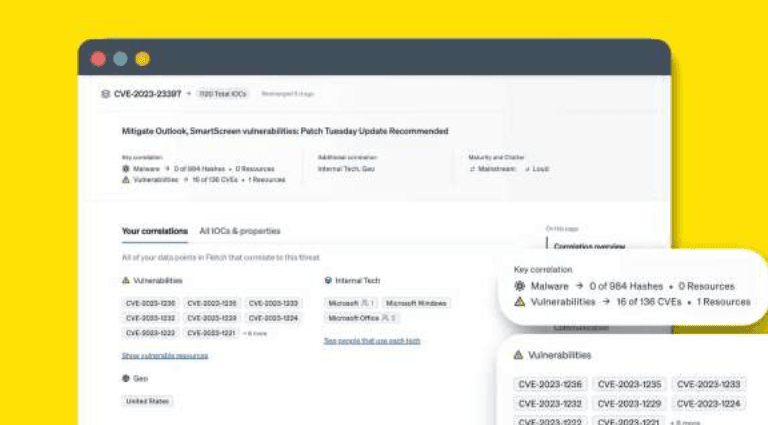
Automate your threat research & correlation work | 2023 Product Updates
Product
Kenisha Liu
Dec 11, 2023

What is vulnerability management
Articles
Kenisha Liu
Dec 5, 2023

Prioritize malware & vulnerability alerts in seconds + discover threats earlier | 2023 Product Updates
Product
Kenisha Liu
Nov 18, 2023

The early warning system for Microsoft
Product
Kenisha Liu
Sep 30, 2023

What is Fletch?
Articles
Kenisha Liu
Sep 11, 2023

Fletch named ‘Top 100 Early Stage Company to Work For in 2023’
News
Kenisha Liu
Sep 7, 2023
Meet the Fletch Experts: How human expertise elevates AI potential
Articles
Kenisha Liu
Aug 24, 2023

What are Correlated Threats?
Product
Kenisha Liu
Aug 18, 2023

Why use Single Sign On (SSO)
Articles
Kenisha Liu
Aug 11, 2023
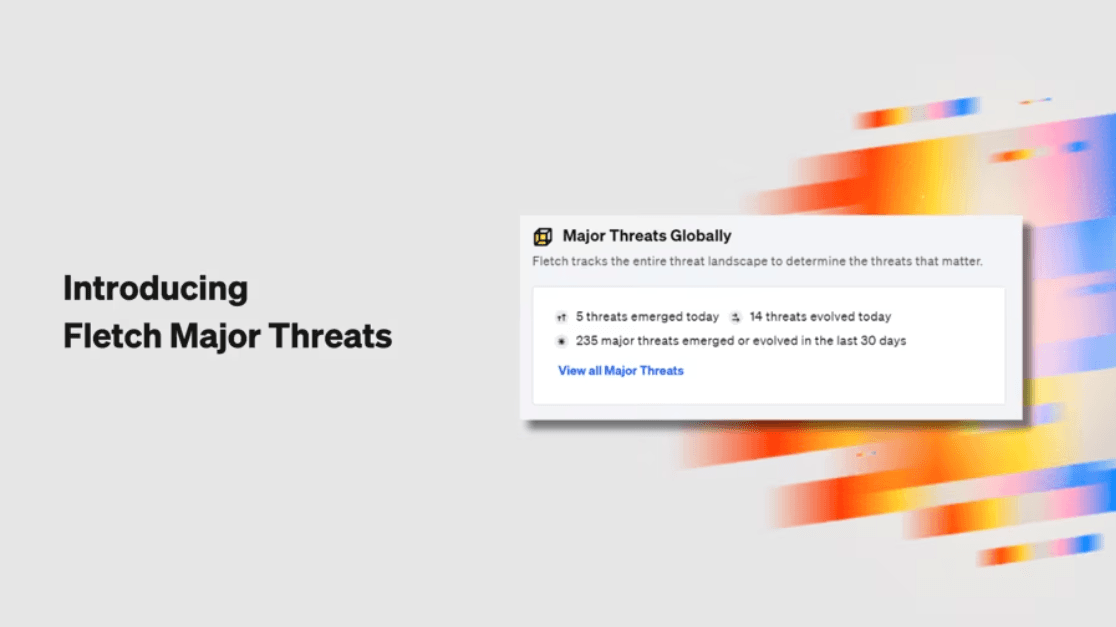
What are Major Threats?
Product
Kenisha Liu
Aug 2, 2023

Correlate your data to the entire threat landscape
Product
Kenisha Liu
Jul 24, 2023

What is Single Sign On? And how does Single Sign On work
Articles
Kenisha Liu
Jul 13, 2023
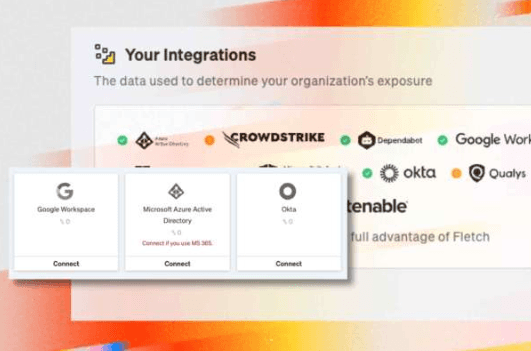
Use SSO Connection with Fletch to secure your organization
Product
Kenisha Liu
Jul 6, 2023

Introducing the new Fletch Threat Board
Product
Kenisha Liu
Jun 20, 2023

Introducing the new Fletch Feed
Product
Lisa Fong
May 2, 2023

