Product

Jake Trujillo
Jun 26, 2024
Latest Headline
The cybercriminal group UNC5537 carried out multiple successful data breaches at Snowflake, a prominent data warehousing service, affecting a range of organizations including the Los Angeles Unified School District (LAUSD), Edgenuity, Ticketmaster, and Advance Auto Parts. These breaches have exploited vulnerabilities in customer security practices, notably the absence of multi-factor authentication (MFA).
Key Points:
First detected in mid-April 2024
Possibly connected with the Scattered Spider group
North American group
0 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out SnowflakeSFA’s Threat Board for any updates or join Fletch to be in the know for every threat.
UNC5537 Summary
UNC5537, possibly connected with the Scattered Spider group, operates mainly out of North America, with one member identified in Turkey. The group's methods involve exploiting weak authentication practices, using stolen credentials to access sensitive data.
Severity: Critical
Maturity: Mainstream
IOCs: 0 Malware hashes and 0 vulnerabilities
Targets: 4 tech targets, 1 industry target, and 9 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.

UNC5537 Victims & Motivations
The organizations impacted by UNC5537 span various industries, such as education, retail, financial services, and government. The motivations behind these breaches are primarily financial, with UNC5537 demanding ransoms and selling stolen data on criminal forums.
High-profile victims include Ticketmaster, which saw personal information of over 560 million users leaked, and Santander Bank, where data from employees and customers were compromised.
UNC5537 Tactics
UNC5537's tactics involve exploiting weak authentication mechanisms and leveraging infostealer malware to gain access to Snowflake instances. UNC5537 has used tools like LummaStealer, VIDAR, RISEPRO, REDLINE, RACOON STEALER, and META to steal credentials and then used the custom utility "rapeflake" for data exfiltration. They employ various tools like FROSTBITE and DBeaver Ultimate for reconnaissance and data exfiltration.
These sophisticated methods allow the attackers to maintain persistence and escalate privileges within compromised systems.
Mitigation Advice
At the time of publication this was the mitigation advice against UNC5537:
Immediately enable Multi-Factor Authentication (MFA) on all Snowflake accounts and any other systems that support it. Reset passwords for all Snowflake accounts, especially if they are suspected to have been compromised or are using single-factor authentication.
At the time of publication these were the right compliance controls to focus on for UNC5537:
Change default usernames and passwords after installation, and avoid reusing passwords between different accounts.
Regularly audit and review user accounts and their permissions to ensure only authorized users have access to privileged accounts.
Create rules to block logins from non-approved devices or locations.
Install and regularly update antivirus software on all company devices.
Regularly review user accounts and remove any that are no longer needed.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
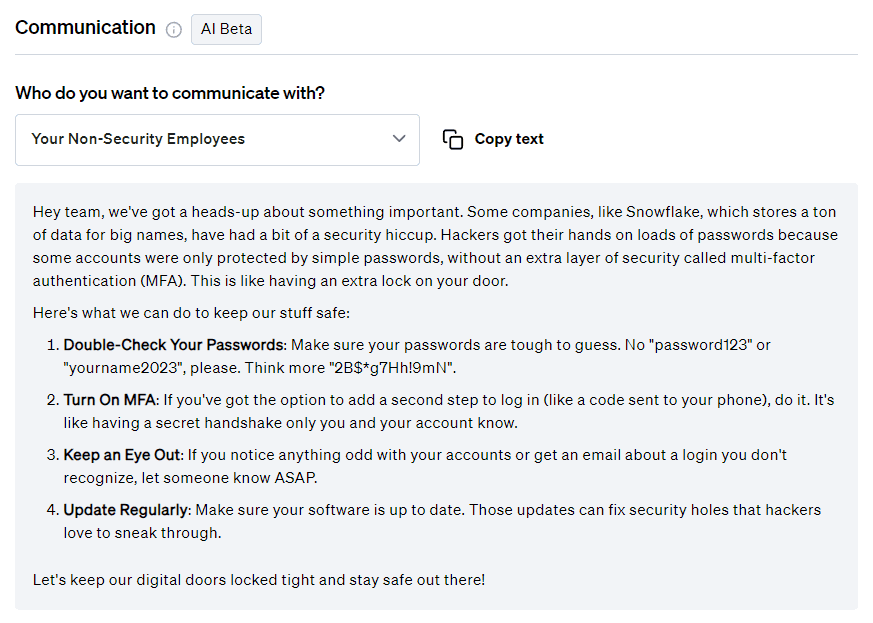
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The UNC5537-Snowflake breaches underscore the critical need for robust security measures, particularly the enforcement of multi-factor authentication (MFA). Organizations using Snowflake must prioritize securing credentials, monitor for unusual activities, and adopt zero-trust models to protect against such sophisticated attacks. These breaches highlight the vulnerability of SaaS platforms to identity-based attacks, emphasizing the necessity for proactive threat hunting and comprehensive incident response plans.
UNC5537 is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.

1. The Register [Over 165 Snowflake Customers Didn’t Use MFA Says Mandiant](https://www.theregister.com/2024/06/10/over_165_snowflake_customers_didnt_use_mfa_says_mandiant/)
2. ITPRO [Snowflake Data Breach Claims Spark War o Words Over Culpability](https://www.itpro.com/2024/06/03/snowflake-data-breach-claims-spark-war-of-words-over-culpability/)
3. SecurityWeek [Snowflake Attacks Mandiant Links Data Breaches to Infostealer Infections](https://www.securityweek.com/2024/06/10/snowflake-attacks-mandiant-links-data-breaches-to-infostealer-infections/)

