Product

Kenisha Liu
Feb 7, 2024
Every company needs threat detection to proactively defend against threats and minimize impact. Unfortunately, threat detection solutions today… leave a lot to be desired. We’ve come to accept that when we think of “proactive threat detection”, that doesn’t mean you're actually getting ahead of your threats. It means you’ll find them once they’re in your org (fingers crossed). And when we think “minimizing impact”, it doesn’t mean you won’t have impact, it means there’s impact, it just won’t be that bad (again, fingers crossed)!
It’s pretty clear that there’s a real problem with threat detection today. Let’s break it down and talk about how to fix it.
Threat detection today
Threat detection today for most typically involves one or more of the following common solutions:
Endpoint detection and response (EDR)
Network detection and response (NDR)
Vulnerability scanner
Threat intelligence platform
Learn more about what threat detection is here.
The problem with today’s threat detection tools
These techniques are helpful tools in the threat detection process, but are not without their flaws. It’s important to be aware of some of these drawbacks when considering how to build your threat detection process. Here are some of the major problems with each:
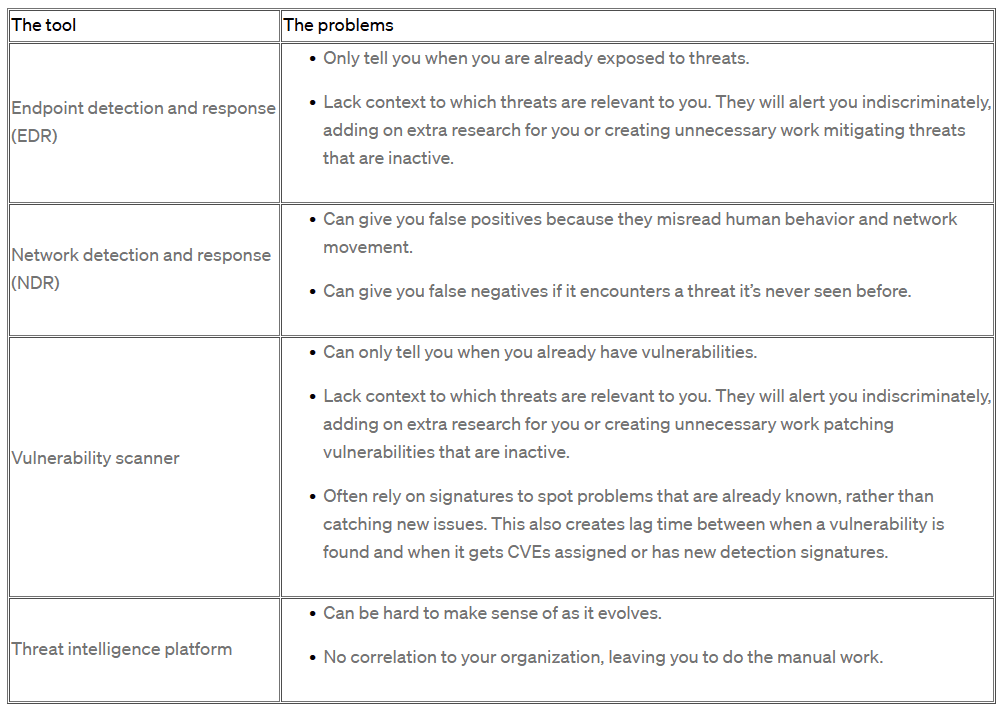
As you can see, the most common solutions often end up creating more work for organizations. However, the biggest problem of all is that these solutions don’t detect threats early or fully mitigate risk. Why invest in a solution that only gets half of the problem done, especially when it still leaves security gaps that could become extremely costly.
A better threat detection solution
This brings us to another solution that wasn’t mentioned above, the pre-vulnerability scanner.

A pre-vulnerability scanner is an early threat detection tool that allows you to truly be proactive in identifying threats. With the use of AI, you can see which threats are targeting you based on your company’s data profile. This includes threats that target your perimeter, tech you use, industry, or location.
Pre-vulnerability scanners also don't have the signature based limitations of traditional tools, which require recognizing patterns of known suspicious activity. This flaw is something that materializes when big companies make headlines for being exposed to zero day attacks and other advanced threats. Effective early threat detection tools instead, are adaptable to the evolving threat landscape because they pull data from the cybersecurity community, meaning you can get threats even before they have IOCs and get alerted at every evolution.
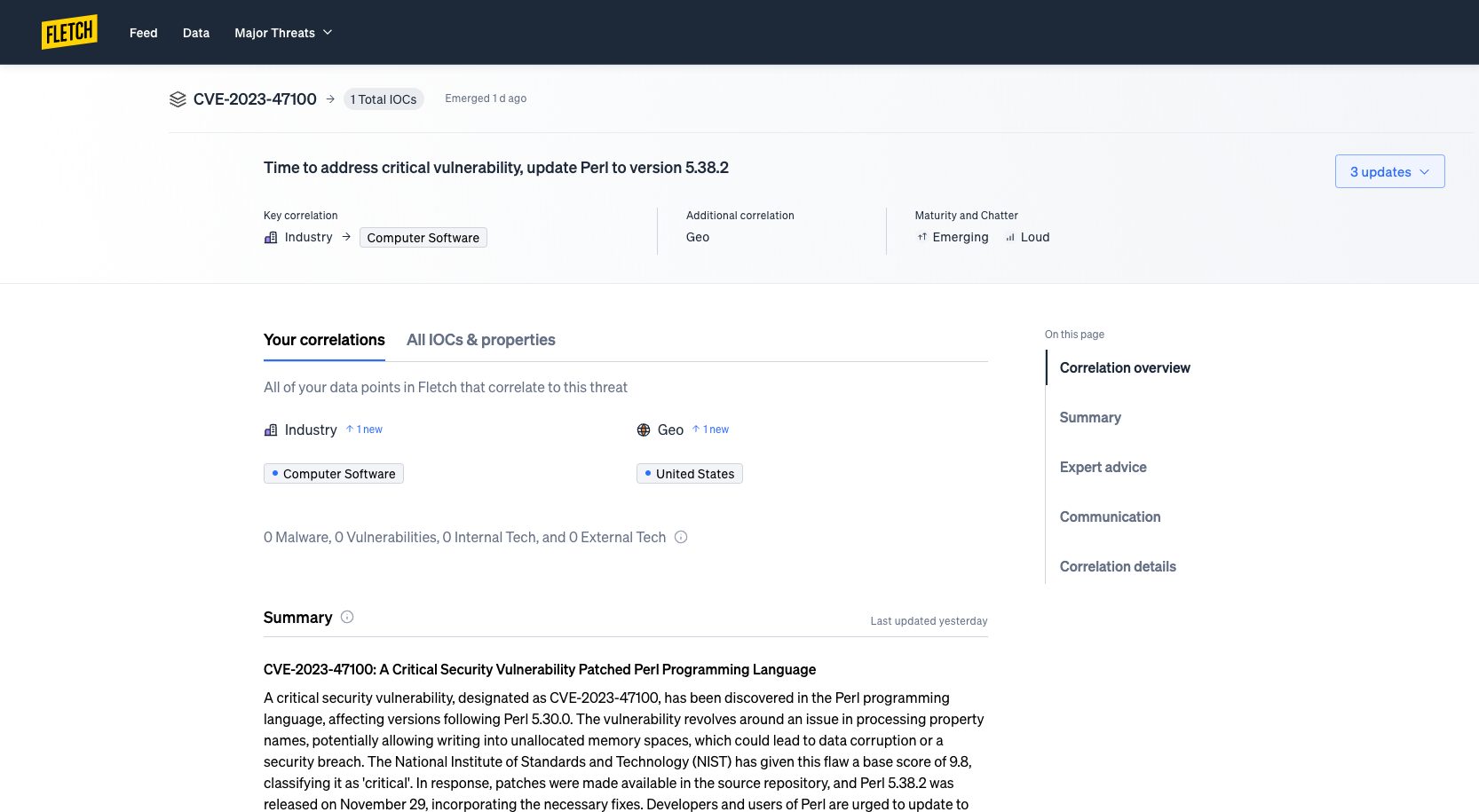
Finally, effective pre-vulnerability scanners provide necessary context. No more indiscriminate alert overloads that require skilled analysts to navigate through them. Fletch detects only the threats that are relevant to you and provides a summary, details on your potential exposure, and even mitigation advice and educational comms tailored for specific audiences.
Takeaway
Traditional threat detection methods have you playing catch-up, reacting to known threats rather than proactively protecting against new ones. Pre vulnerability scanners use early threat detection to address the flaws of the current approaches and offers a way to truly get ahead of threats and minimize unnecessary work. It’s a needed paradigm shift towards a more secure and adaptive way of doing cybersecurity.
Get early threat detection when you join the Fletch waitlist.


