Product

Jake Trujillo
Jun 17, 2024
Latest Headline
The TellYouThePass ransomware gang has been actively exploiting a critical PHP vulnerability, CVE-2024-4577, to attack servers, encrypt files, and demand ransom. This remote code execution (RCE) vulnerability affects all PHP versions on Windows, particularly when PHP is running in CGI mode.
Key Points:
Discovered May 7, 2024
Patched on June 6
9 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out TellYouThePass’s Threat Board for any updates or join Fletch to be in the know for every threat.
TellYouThePass Summary
TellYouThePass, an established ransomware group active since 2019, is known for integrating newly discovered vulnerabilities into their attack strategies rapidly. Although specific attribution remains unclear, their tactics suggest sophisticated threat actor capabilities. The group primarily targets high-exposure servers running PHP on Windows, especially those using XAMPP installations.
Severity: Critical
Maturity: Mainstream
IOCs: 88 Malware hashes and 7 vulnerabilities
Targets: 4 tech targets, 1 industry target, and 9 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.

TellYouThePass Victims & Motivations
The main victims of this TellYouThePass ransomware campaign are PHP servers on Windows, particularly those running XAMPP. While no specific industries have been reported, the general target is high-exposure servers. Significant infections have been reported in China, and it is estimated that over 450,000 PHP servers worldwide could be vulnerable. The primary motivation for these attacks is financial gain through ransomware payments.
TellYouThePass Tactics
TellYouThePass employs several methodologies, including remote code execution via CGI mode, uploading web shells, and using mshta.exe to run remote payloads. The ransomware encrypts files and leaves ransom notes demanding 0.1 BTC. The malware tools associated with these attacks include TellYouThePass ransomware, Gh0st RAT, and Cobalt Strike.
Once executed, the malware sends an HTTP request to a command-and-control server, enumerates directories, stops running processes, generates encryption keys, and starts encrypting files with specific extensions.
Migration Advice
At the time of publication this was the mitigation advice against TellYouThePass:
For XAMPP users, temporarily comment out the `ScriptAlias` directive in the `httpd-xampp.conf` file to disable PHP's CGI mode.
If immediate update is not possible, implement specific rewrite rules in the web server configuration to block attacks targeting the vulnerability for Traditional Chinese, Simplified Chinese, and Japanese locales.
Immediately update PHP to the latest patched versions (PHP 8.3.8, PHP 8.2.20, or PHP 8.1.29) on all systems.
Implement IP blocking or rate limiting for the source IP address 221.122.67[.]75 if it is deemed malicious.
At the time of publication these were the right compliance controls to focus on for TellYouThePass:
Work with your Internet Service Provider (ISP) or a third-party provider to filter out harmful network traffic.
Install a network intrusion prevention system to block suspicious traffic.
Install security applications like Windows Defender Exploit Guard and Enhanced Mitigation Experience Toolkit to protect against software exploits.
Use browser sandboxes and application microsegmentation to isolate applications and reduce the impact of exploitation.
Use separate accounts for daily tasks and administrative tasks.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
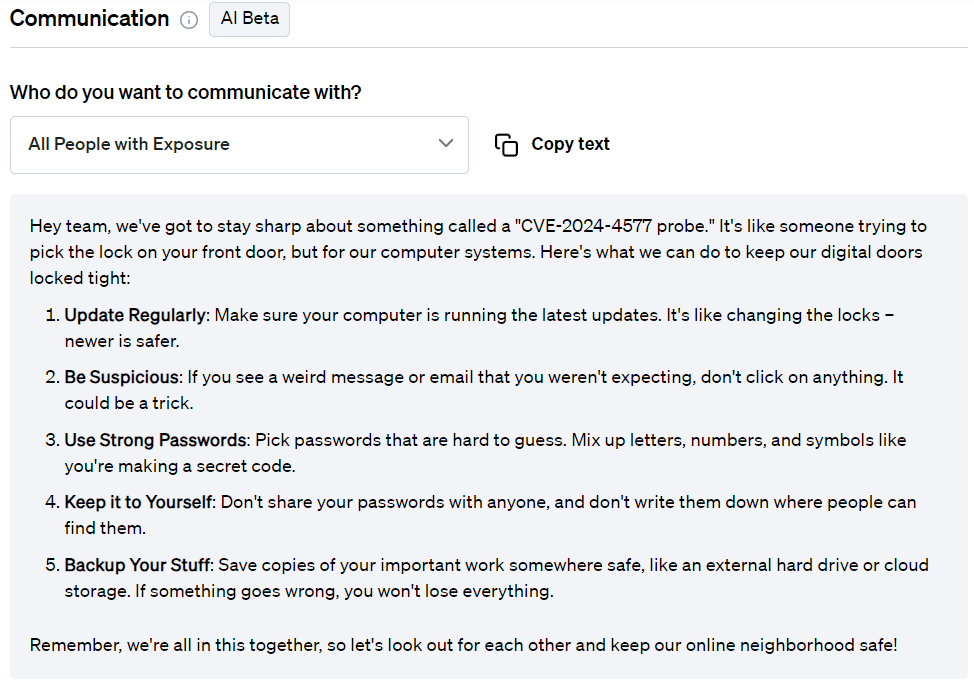
For customers:
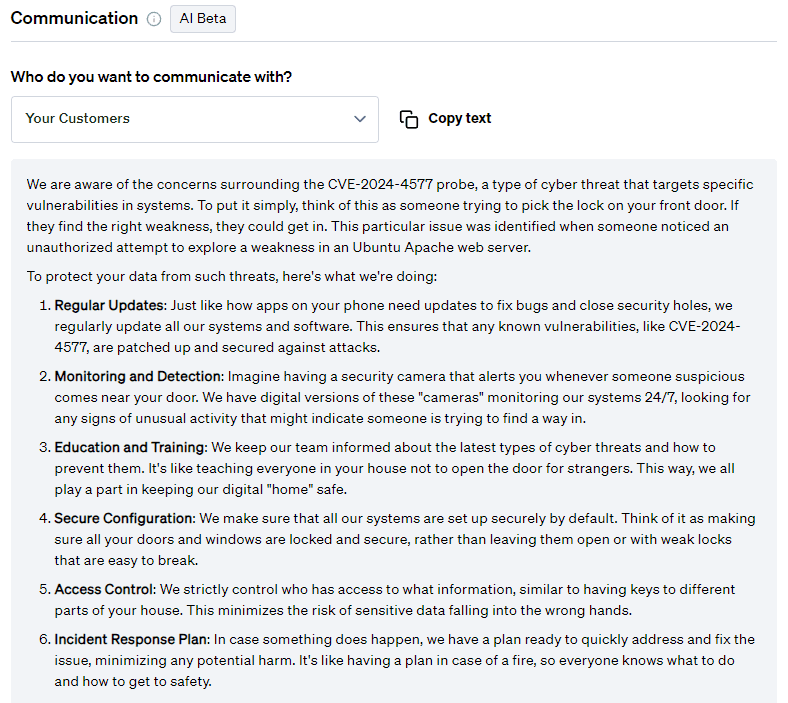
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The exploitation of CVE-2024-4577 by TellYouThePass highlights the critical importance of timely patching and upgrading PHP versions. Immediate patching to the latest versions (8.3.8, 8.2.20, and 8.1.29) is essential to mitigate this threat. Additionally, enhanced security measures such as disabling CGI mode where unnecessary, using web application firewalls, and conducting regular security audits are crucial to preventing exploitation and mitigating risks.
TellYouThePass is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.


