Product

Jake Trujillo
Jul 3, 2024
Latest Headline
On July 1, 2024, a critical vulnerability known as CVE-2024-6387, or "RegreSSHion," was disclosed by the Qualys Threat Research Unit. This vulnerability affects OpenSSH servers running on glibc-based Linux systems, allowing for unauthenticated remote code execution with root privileges.
Key Points:
CVE-2024-6387 is a regression of a previously fixed vulnerability, CVE-2006-5051
Impacts over 14 million OpenSSH server instances worldwide, with approximately 700,000 of these being exposed to the internet
6 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out RegreSSHion’s Threat Board for any updates or join Fletch to be in the know for every threat.
RegreSSHion Summary
‘RegreSSHion', or CVE-2024-6387, is a significant security flaw that has been identified in OpenSSH, a widely regarded secure software implementation, that could potentially put millions of servers at risk. CVE-2024-6387, is a regression of a previously patched issue from 2006 (CVE-2006-5051) that has resurfaced. If exploited, this flaw allows attackers to execute arbitrary code with the highest privileges, leading to complete system takeover, malware installation, creation of backdoors, and other malicious activities.
Emerged: July 2024
Severity: Critical
Maturity: Mainstream
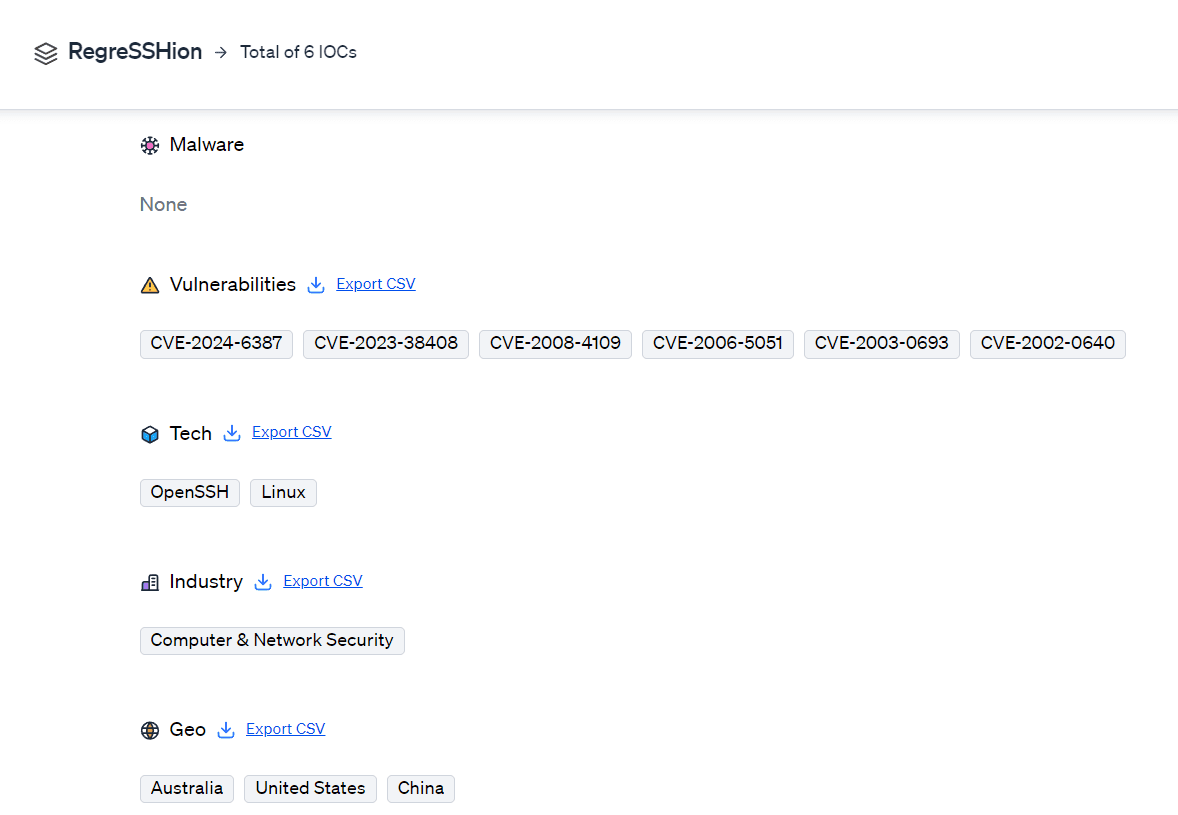
IOCs: 0 malware hashes and 6 vulnerabilities
Targets: 2 tech targets, 1 industry target, and 3 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
RegreSSHion Victims & Motivations
RegreSSHion targets OpenSSH versions from 8.5p1 to 9.8p1, as well as versions earlier than 4.4p1 that have not been patched for CVE-2006-5051. Industries most at risk include those heavily reliant on Linux-based systems, such as finance, healthcare, and cloud services. Geographically, the vulnerability has a global impact, with significant exposure in regions where OpenSSH is widely used.
The primary motivation for exploiting this vulnerability would be to gain full system access, install backdoors, manipulate data, and maintain persistent unauthorized access.
RegreSSHion Tactics
RegreSSHion’s exploitation method involves sending numerous authentication attempts to trigger the race condition in the sshd signal handler, ultimately leading to the execution of the syslog() function in an unsafe manner. Despite the availability of proof-of-concept exploit code, there have been no widespread reports of malicious exploitation in the wild. This suggests that while the vulnerability is severe, its complex exploitation process might limit its use to targeted attacks rather than widespread campaigns.
Mitigation Advice
At the time of publication this was the mitigation advice against RegreSSHion:
Review and apply strict network policies within Kubernetes to control traffic flow and prevent unauthorized access to services running OpenSSH.
Implement seccomp profiles for sshd to restrict the system calls that can be executed, reducing the potential for exploitation.
If immediate update is not possible, change the `LoginGraceTime` parameter to `0` in the OpenSSH configuration file to prevent unauthenticated sessions from being exploited.
Adjust the MaxStartups and LoginGraceTime settings in the SSH configuration to make exploitation less likely.
Set up allowlisting to restrict SSH access to known, trusted IP addresses.
At the time of publication these were the right compliance controls to focus on for RegreSSHion:
Install security applications like Windows Defender Exploit Guard and Enhanced Mitigation Experience Toolkit to protect against software exploits.
Use browser sandboxes and application microsegmentation to isolate applications and reduce the impact of exploitation.
Use a service that specializes in filtering network traffic to block harmful sources, ports, or protocols.
Work with your Internet Service Provider (ISP) or a third-party provider to filter out harmful network traffic.
Install a network intrusion prevention system to block suspicious traffic.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
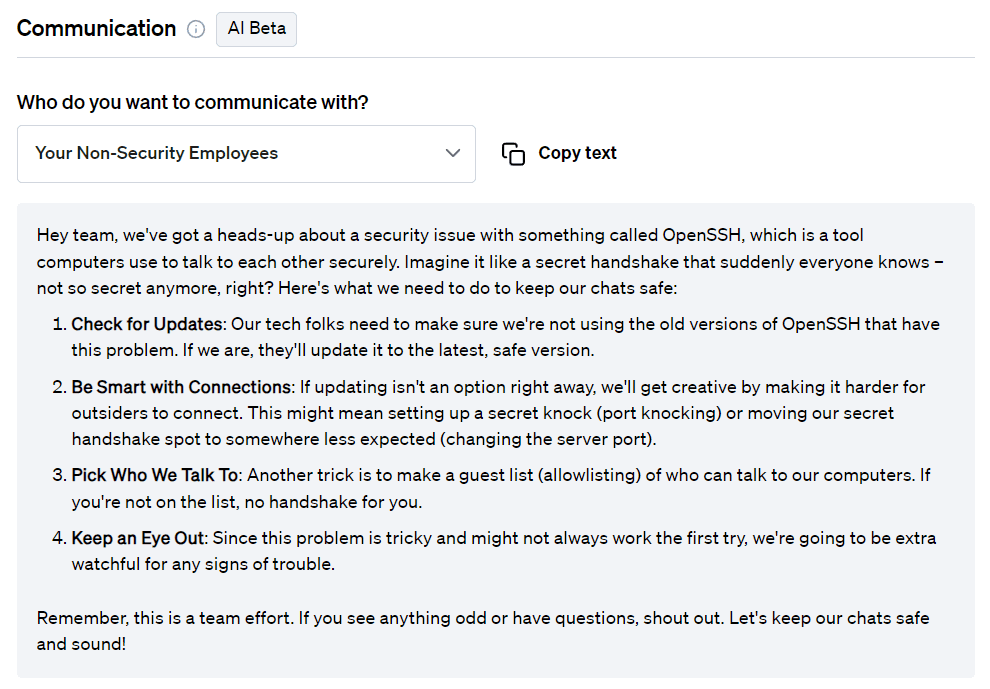
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
For customers:

For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The CVE-2024-6387 vulnerability poses a significant risk to systems running vulnerable versions of OpenSSH. Immediate action is required to patch affected systems to version 9.8p1 or later. Additionally, network-based access controls should be implemented, and sshd configurations should be updated to mitigate the risk. Continuous monitoring of security advisories and applying timely updates are crucial steps in safeguarding systems against such vulnerabilities.
RegreSSHion is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.

1. Tech Radar Pro [Thousands of servers could be at risk due to major OpenSSH security flaw](https://www.techradar.com/pro/security/thousands-of-servers-could-be-at-risk-due-to-major-openssh-security-flaw)
2. Security Boulevard [Latest OpenSSH Vulnerability Might Impact 14M Linux Systems](https://securityboulevard.com/2024/07/latest-openssh-vulnerability-might-impact-14m-linux-systems/)
3. Sploitus [Exploit for CVE-2024-6387](https://sploitus.com/exploit?id=39E70D1A-F5D8-59D5-A0CF-E73D9BAA3118)

