Product

Jake Trujilo
May 29, 2024
Latest Headline
A critical vulnerability identified as CVE-2024-4323, also known as "Linguistic Lumberjack," has been discovered in Fluent Bit versions 2.0.7 through 3.0.3. The flaw could result in denial of service (DoS), information disclosure, or, under specific conditions, remote code execution (RCE). Fixes were committed by May 15, 2024 in Fluent Bit version 3.0.4.
Key Points:
Reported to vendor on April 30
CVSS score of 9.8
Addressed in Fluent Bit version 3.0.4
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Linguistic Lumberjack’s Threat Board for any updates or join Fletch to be in the know for every threat.
Linguistic Lumberjack Summary
The vulnerability, dubbed "Linguistic Lumberjack," was discovered by Tenable Research. It affects multiple cloud service providers and tech companies that use Fluent Bit. Fluent Bit is an open-source telemetry agent heavily utilized in cloud and container environments, including Kubernetes distributions and platforms like AWS, GCP, and Azure.
Severity: Critical
Maturity: Mainstream
IOCs: 0 Malware hashes and 1 vulnerability
Targets: 5 tech targets, 2 industry targets, and 1 geo target
Learn more about Fletch’s metrics in the Fletch Help Center.
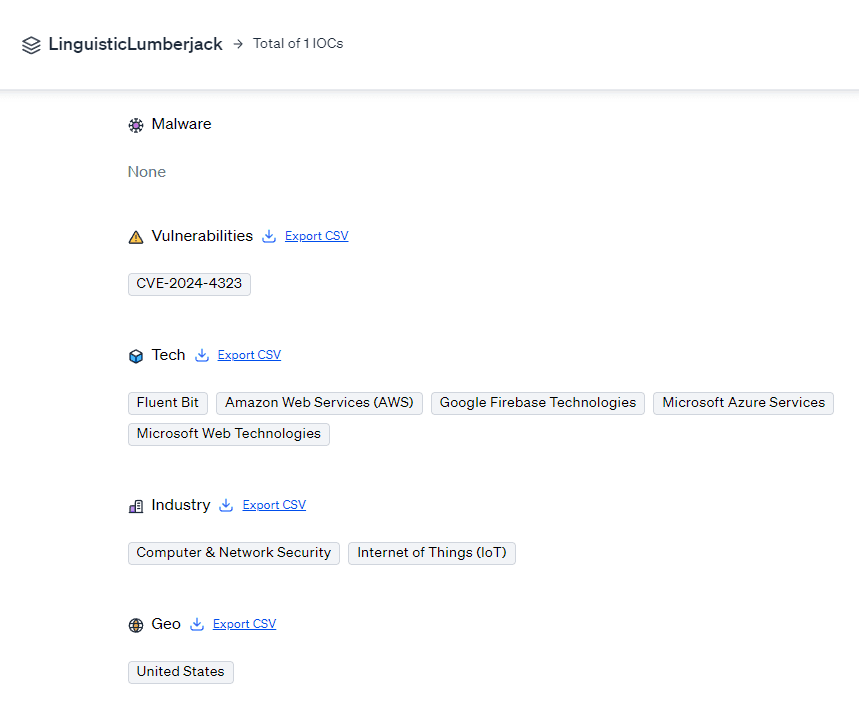
Linguistic Lumberjack Victims & Motivations
Fluent Bit is widely used by major cloud providers and IT companies such as Cisco, LinkedIn, VMware, and Adobe. The vulnerability poses a global impact, potentially affecting organizations worldwide that utilize Fluent Bit for logging and metrics. The primary motivations behind exploiting this vulnerability could include disrupting services, stealing data, and leveraging the access for further attacks.
Linguistic Lumberjack Tactics
The Linguistic Lumberjack vulnerability involves a memory corruption issue in Fluent Bit's built-in HTTP server, specifically through improper validation of inputs in the “traces” API endpoint. This leads to a heap buffer overflow, which can be exploited to cause service crashes (DoS) or to retrieve sensitive information. While creating a reliable remote code execution exploit is complex and time-consuming, the ease of causing DoS and information leaks makes this vulnerability particularly concerning.
Mitigation Advice
At the time of publication this was the mitigation advice against Linguistic Lumberjack:
Ensure that only authorized personnel have access to the Fluent Bit API endpoints, especially /api/v1/traces and /api/v1/trace.
Utilize Qualys or similar vulnerability scanning tools to scan your environment for CVE-2024-4323 and ensure no affected versions remain.
Immediately identify all instances of Fluent Bit versions 2.0.7 through 3.0.3 in your environment. Use asset management tools to create a comprehensive inventory.
Scan all running workloads with Aqua or a similar tool to identify if the vulnerable version of Fluent Bit is in use.
Restrict access to the HTTP endpoint that is vulnerable to minimize the attack surface.
At the time of publication these were the right compliance controls to focus on for Linguistic Lumberjack:
Use a service that specializes in filtering network traffic to block harmful sources, ports, or protocols.
Install security applications like Windows Defender Exploit Guard and Enhanced Mitigation Experience Toolkit to protect against software exploits.
Use browser sandboxes and application microsegmentation to isolate applications and reduce the impact of exploitation.
Implement a data loss prevention strategy to protect sensitive information and prevent unauthorized data sharing.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
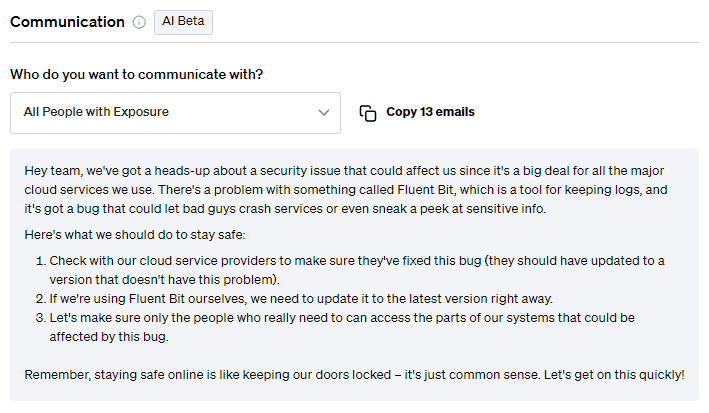
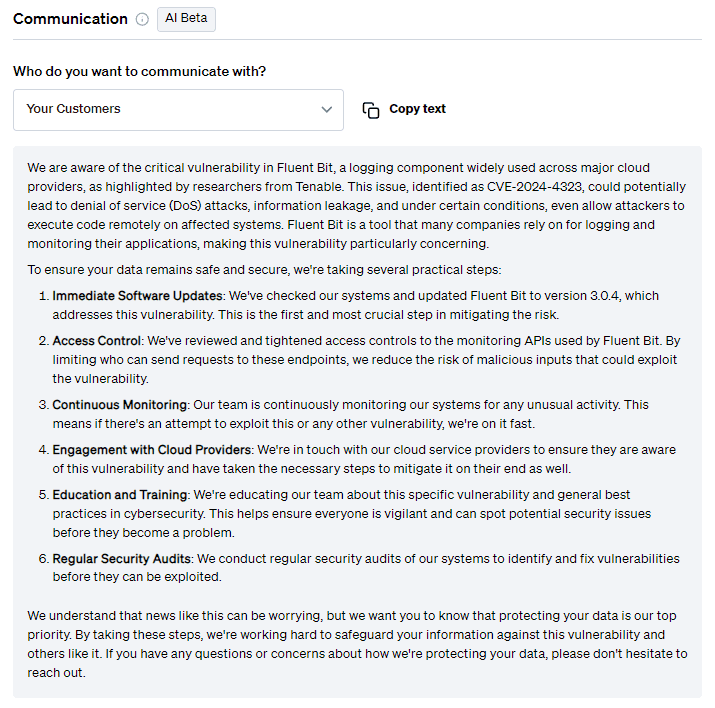
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
For customers:
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
Linguistic Lumberjack is a significant threat to systems using Fluent Bit due to the potential for DoS and information leakage. Immediate patching to version 3.0.4 is essential to mitigate these risks. Additionally, restricting access to the monitoring API can help reduce the attack surface. Given Fluent Bit's extensive deployment in cloud environments, addressing this vulnerability promptly is crucial for maintaining security and operational integrity.
Linguistic Lumberjack is just one example of an ever evolving threat that requires in-depth cyber intelligence to stay on top of. Fletch helps you keep track of, and prioritizes, them all.
As the de facto record on the threat landscape, our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats to your tech and people early, or give you daily advice on what to do.
Join the Fletch waitlist and try it for yourself.

1. Fluent Bit [Statement on CVE-2024-4323 and its fix](https://fluentbit.io/blog/2024/05/21/statement-on-cve-2024-4323-and-its-fix/)
2. Tenable [Linguistic Lumberjack Attacking Cloud Services Via Logging Endpoints](https://www.tenable.com/blog/linguistic-lumberjack-attacking-cloud-services-via-logging-endpoints)
3. Security Week [Vulnerability Found in Fluent Bit UtilityUsed Major Cloud Tech Companies](https://www.securityweek.com/vulnerability-found-fluent-bit-utility-used-major-cloud-tech-companies)
4. Bleeping Computer [Critical Fluent Bit flaw impacts all major cloud providers](https://www.bleepingcomputer.com/news/security/critical-fluent-bit-flaw-impacts-all-major-cloud-providers)

