Product

Jake Trujillo
Apr 18, 2024
Latest headline
New malware named Latrodectus, suspected to have been developed by the same team behind the IcedID loader, is gaining traction among initial access brokers (IABs). IABs are cybercriminals or groups who specialize in gaining unauthorized entry into computer networks or systems. They often sell or provide this access to other malicious actors who intend to carry out various cyber attacks.
It was initially spread by the IAB and known Qbot distributor TA577 in November 2023. Since early 2024, Latrodectus has been predominantly utilized by another IAB, TA578. They employ contact forms to initiate communication with targets under the guise of legal threats for alleged copyright infringement.
Key points:
Initially emerged in late 2023
Major evolutions in early 2024
Utilized by initial access brokers (IABs)
33 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Latrodectus’s Threat Board for any updates or create an account to be in the know for every threat.
Latrodectus malware summary
The Latrodectus malware was first identified in October 2023, emerging during the disruption of QBot. "Operation Duck Hunt," targeted the QBot infrastructure, leading to the uninstallation of the malware from over 700,000 systems worldwide and the seizure of funds held in cryptocurrency by the operators. Latrodectus leveraged some of QBot's communication channels and infrastructure to quickly establish themselves as a viable threat.
Initially distributed by the IAB TA577, known for spreading Qbot, the deployment of Latrodectus has shifted to primarily being distributed by TA578. Research into Latrodectus' string hashing techniques for campaign IDs has linked its operation to the creators of IcedID, suggesting shared backend infrastructure and methodologies.
In addition to its direct impacts, Latrodectus has been observed in conjunction with other threats. In late 2023, eSentire's Threat Response Unit detected the deployment of DanaBot, a sophisticated banking Trojan, which was being used to deliver IcedID and, subsequently, Latrodectus.
Severity: Low, Quiet
Maturity: Mainstream
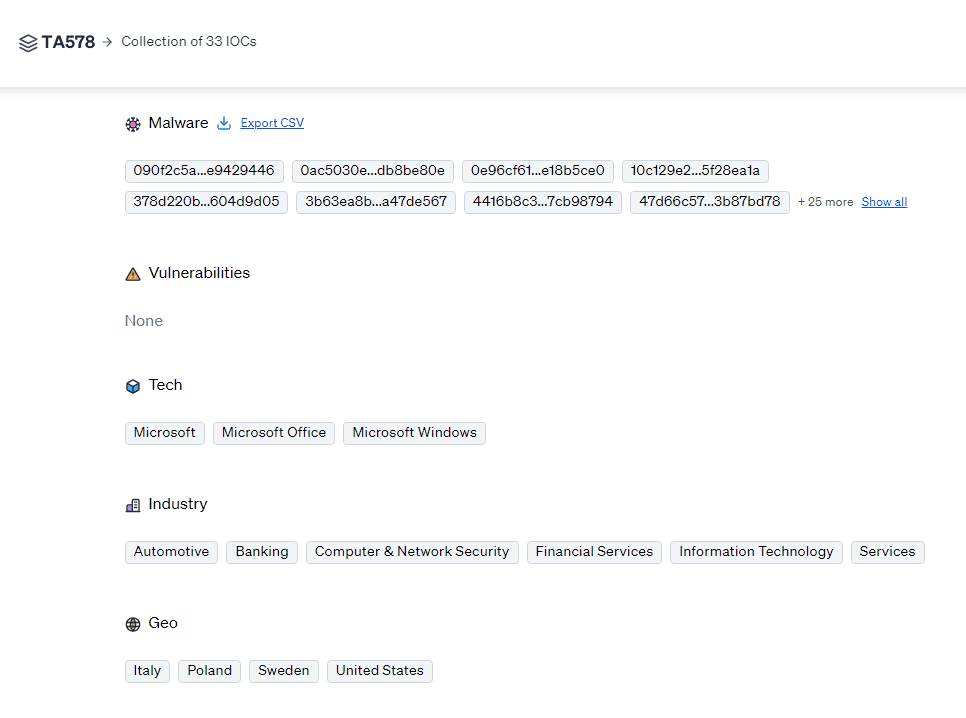
IOCs: 33 Malware hashes
Targets: 3 tech targets, 6 industry targets, and 4 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
Latrodectus malware victims and motivations
TA578’s main goal is financial profit. They aim to achieve this through immediate financial theft, ransom payments, and long-term monetization of stolen data. They often target financial institutions to access financial assets and sensitive customer data. Latrodectus also targets other industries including the healthcare sector for valuable personal and medical info, and manufacturing and industrial firms to disrupt operations and obtain proprietary information.
The consequences of an infection can be severe, and potentially lead to data exfiltration, espionage, system compromise, and financial loss.
Latrodectus malware tactics
Latrodectus is a potent backdoor Trojan that operates as a sophisticated tool for cyber exploitation. It enables unauthorized remote access to infected systems, allowing attackers to execute various commands and control the systems remotely.
Latrodectus also exhibits the ability to download and execute a range of malicious files, adding to its destructive capabilities. It can retrieve additional payloads from a command-and-control (C2) server and has advanced evasion techniques, such as verifying the number of processes and MAC addresses.
The rise of Latrodectus coincides with increased usage by IABs in email threat campaigns, particularly by the groups TA577 and TA578. After being known for deploying IcedID, TA577 has almost exclusively shifted to using Latrodectus since mid-January 2024. TA578 has been leveraging Latrodectus in phishing lures, which employs contact forms to initiate communication with their targets under the guise of legal threats for alleged copyright infringement.
Mitigation advice
At the time of publication this was the mitigation advice against Lactrodectus:
Short-Term:
Detect and remove Latrodectus: Common detection names include Trojan:Win32/Latrodectus and Backdoor.Latrodectus.
To remove: isolate the infected system, use Safe Mode, terminate suspicious processes, delete malicious files, clean up registry entries, and use trusted antivirus software for thorough scanning.
Enable Sandbox Solutions: Deploy or enhance sandboxing solutions that can analyze attachments and URLs in a safe environment, despite Latrodectus's evasion techniques.
Implement Email Filtering: Utilize advanced email filtering solutions that can detect and block phishing attempts, which are the primary distribution method for Latrodectus.
Long-Term:
Make sure to connect your security data to your Fletch workspace, so that Fletch is able to correlate and prioritize threats like this effectively in the future.
Limit the use of Msiexec.exe to only those who absolutely need it.
Limit access to vulnerable programs to only necessary users.
Limit the use of PowerShell to only administrators and restrict what commands can be executed.
Limit the ability to schedule priority processes to only the Administrators group.
You can check out the most recent mitigation measures by creating an account.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:

For customers:

For more templates for your different stakeholders, create an account.
Takeaway
Latrodectus is essentially an evolved form of the IcedID loader. The malware's infrastructure is designed for flexibility and longevity in campaigns, with new C2 servers often set up at the end of the week before attacks. Experts are concerned about the potential further spread of Latrodectus among cybercriminals due to its sophisticated capabilities.
Its stealth tactics signal a trend where malware authors are increasingly focusing on evading detection, necessitating a recalibration of cybersecurity strategies to counteract these evolving threats effectively.
Latrodectus is just one example of an ever evolving threat that requires in-depth cyber intelligence to stay on top of. Fletch helps you keep track of, and prioritizes, them all.
As the de facto record on the threat landscape, our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, detect threats to your tech and people early, or simply to become an instant expert on any threat at any time.
Learn more about Fletch’s threat intelligence or creating an account and try it yourself.

1. eSentire [DanaBot's Latest Move: Deploying Latrodectus](https://www.esentire.com/blog/danabots-latest-move-deploying-icedid)
2. rivITMedia [Latrodectus Malware: A Comprehensive Guide to Detection and Removal](https://www.rivitmedia.com/cyberthreats/malware/latrodectus/)
3. DarkReading [Malicious Latrodectus Downloader Picks Up Where QBot Left Off](https://www.darkreading.com/threat-intelligence/new-loader-takes-over-where-qbot-left-off)
4. Hackread [New Latrodectus Downloader Malware Linked to IcedID and Qbot Creators](https://www.hackread.com/latrodectus-downloader-malware-icedid-qbot/#google_vignette)
5. CISO2CISO [Malicious Latrodectus Downloader Picks Up Where QBot Left Off](https://ciso2ciso.com/malicious-latrodectus-downloader-picks-up-where-qbot-left-off-source-www-darkreading-com/)
6. FBI [FBI, Partners Dismantle Qakbot Infrastructure in Multinational Cyber Takedown](https://www.fbi.gov/news/stories/fbi-partners-dismantle-qakbot-infrastructure-in-multinational-cyber-takedown)
7. Red Canary [Global coalition of law enforcement agencies take down Qbot](https://redcanary.com/blog/qbot-takedown/)

