Product

Finn Callaghan
Jul 1, 2024
Latest Headline
Kinsing malware has significantly escalated its attacks on Apache Tomcat servers, exploiting multiple vulnerabilities. Known for targeting Linux-based cloud infrastructure, this malware installs backdoors and cryptominers, primarily using the XMRig software to mine Monero cryptocurrency. The malware is challenging to detect as it conceals itself within overlooked system directories.
Key Points:
Active since at least January 2020
Targets Apache Tomcat servers since mid-2023
1767 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Kinsing’s Threat Board for any updates or join Fletch to be in the know for every threat.
Kinsing Group Summary
Kinsing, also known as H2Miner, has been reported by various cybersecurity firms, including Tenable Research and AquaSec. While it is not specifically attributed to any country, its activities have been observed globally. Kinsing is part of a larger group involved in cryptojacking campaigns, targeting a wide range of open-source applications and cloud services.
Severity: Low
Maturity: Mainstream
IOCs: 1767 Malware hashes and 5 vulnerabilities
Targets: 14 tech targets, 1 industry targets, and 8 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
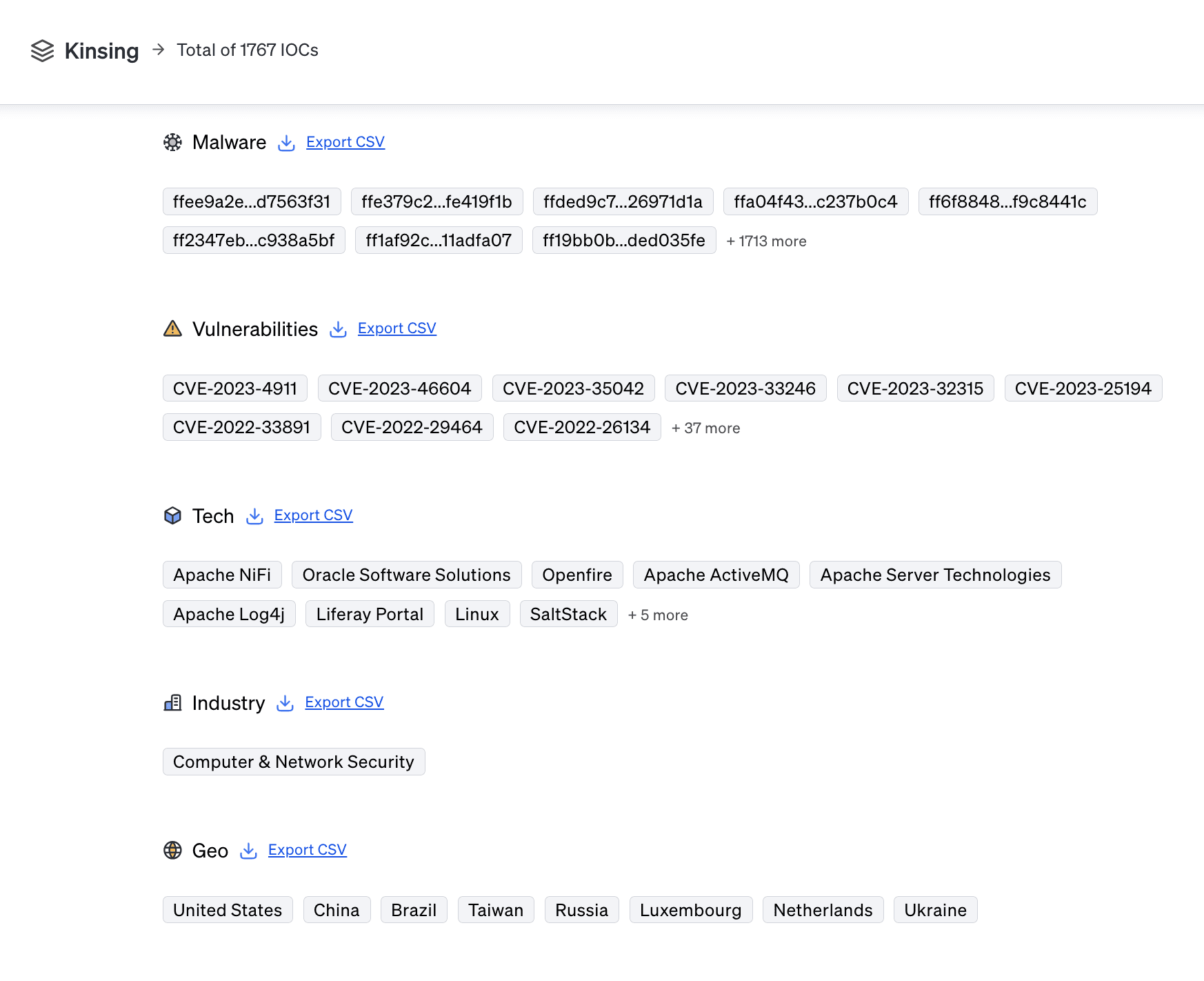
Kinsing Victims & Motivations
The technologies targeted by Kinsing include Linux cloud servers, Apache Tomcat, Docker, PostgreSQL, and Redis. The industries affected are broad, encompassing enterprises that utilize open-source software and cloud services. The malware's initial detection was in China, but its attacks have been widespread across various regions. The primary motivation behind Kinsing's activities is financial gain through unauthorized crypto mining.
Kinsing Tactics
Kinsing employs various methodologies to gain unauthorized access, such as exploiting vulnerabilities and installing backdoors. Once inside a system, it deploys cryptominers to use the system's resources for mining Monero. The malware hides within legitimate system directories to avoid detection, making it blend in with non-suspicious files. This stealthy approach allows the malware to persist on compromised systems for extended periods.
Mitigation Advice
At the time of publication this was the mitigation advice against Kinsing:
Disable or securely configure Docker API and Kubernetes to prevent unauthorized access.
Update Apache Tomcat servers to the latest version to patch any critical vulnerabilities that could be exploited by the malware.
Update all Apache ActiveMQ servers to the latest patched version to address the CVE-2023-46604 vulnerability.
Ensure all Linux systems are patched against the Looney Tunables vulnerability (CVE-2023-4911)
Update all instances of Openfire to the latest version to patch the vulnerability (CVE-2023-32315).
At the time of publication these were the right compliance controls to focus on for Kinsing:
Set proper permissions for files and directories to prevent unauthorized access.
Limit the use of PowerShell to only administrators and restrict what commands can be executed.
Ensure all employees have the correct permissions for their job roles.
Install and regularly update antivirus software on all company devices.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
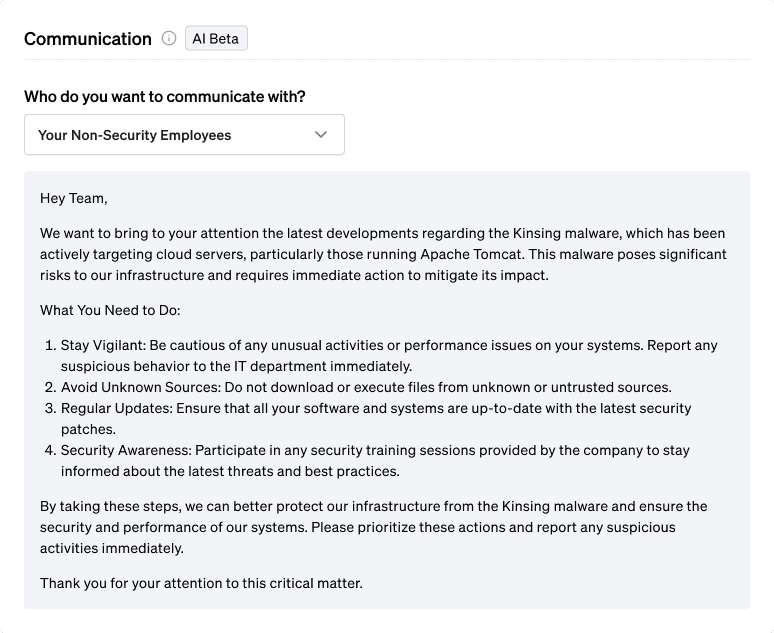
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
Kinsing represents a persistent and evolving threat to Linux-based cloud infrastructure. Its ability to exploit vulnerabilities and hide within overlooked system directories makes it particularly challenging to detect and mitigate. Organizations must ensure rigorous monitoring, timely patching of vulnerabilities, and the implementation of comprehensive security measures to defend against such sophisticated threats. The continuous evolution of Kinsing underscores the need for adaptive and proactive cybersecurity strategies.
Kinsing is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.

1. [Tenable](https://www.tenable.com/blog/kinsing-malware-hides-itself-as-a-manual-page-and-targets-cloud-servers)
2. [GBHackers](https://www.gbhackers.com/kinsing-malware-attacking-apache-tomcat-server-with-vulnerabilities)
3. [SecurityOnline](https://securityonline.info/the-hidden-threat-in-man-pages-kinsing-malware-targets-apache-tomcat-servers)
4. [JSPlaces](https://www.jsplaces.com/gbhackers/20/05/2024/kinsing-malware-attacking-apache-tomcat-servers-to-deploy-cryptominers)

