Product

Jake Trujillo
May 24, 2024
Latest Headline
Kimsuky, a North Korean hacking group, is utilizing a new Linux malware called Gomir to target South Korean government and commercial organizations. It checks for administrative privileges on Linux systems, maintains persistence, and communicates with its command-and-control server to receive instructions for various operations.
Key Points:
Active since at least 2012
North Korean threat group
1320 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Kimsuky’s Threat Board for any updates or join Fletch to be in the know for every threat.
Kimsuky Summary
Kimsuky, also known as Springtail, Thallium, and Velvet Chollima, is closely linked to North Korea’s military intelligence agency, the Reconnaissance General Bureau (RGB). The group has been active since at least 2012, focusing on cyber espionage and intelligence gathering.
Kimsuky primarily targets South Korean government and commercial sectors, but has also shown interest in entities within the United States, Europe, and Russia. Kimsuky’s arsenal includes tools like Troll Stealer and Gomir, a Linux variant of the GoBear backdoor.
Severity: Medium
Maturity: Mainstream
IOCs: 1315 Malware hashes and 5 vulnerabilities
Targets: 15 tech targets, 3 industry targets, and 26 geo target.
Learn more about Fletch’s metrics in the Fletch Help Center.

Kimsuky Victims & Motivations
The primary targets of Kimsuky include Linux and Windows systems used by government and commercial sectors in South Korea. The group's motivations are centered on espionage and intelligence gathering, particularly on political and military matters. In 2023, their focus included nuclear agendas related to the China-North Korea relationship and the Russia-Ukraine conflict.
Their sophisticated approach often involves exploiting supply chain vulnerabilities, highlighting the critical need for organizations to rigorously vet their software sources and updates.
Kimsuky Tactics
Kimsuky’s methods include spear phishing, social engineering, and the use of trojanized software installers. The new malware Gomir supports 17 operations, including executing arbitrary shell commands, probing network endpoints, and exfiltrating files from the system. These capabilities make it a potent tool for cyber espionage.
Gomir is a Linux variant of the previously known Windows Trojan GoBear, and retains similar functionalities, including command-and-control (C2) server communication, persistence, and command execution capabilities. Gomir gains persistence by copying itself to the `/var/log/syslogd` directory and creating a systemd service named "syslogd".
Mitigation Advice
At the time of publication this was the mitigation advice against Kimsuky:
Short-Term:
Implement strict access controls and use multi-factor authentication (MFA) for accessing sensitive systems and data.
Disable the execution of PowerShell scripts for regular users if not required for their tasks.
Block the known malicious URLs and IP addresses associated with the malware at the firewall level.
Conduct a scan of all systems for the presence of the identified indicators of compromise (IOCs) and remove any detected malware.
Update antivirus and anti-malware software to the latest versions that can detect the "Dropper/CHM.Generic" malware.
Long-Term:
Limit access to important files and folders to only select privileged users.
Limit the number of users with administrator privileges and monitor their activities.
Limit access to system files and folders to only a few trusted employees.
Regularly update all software on company devices; make sure all auto-update mechanisms are enabled and working correctly.
Limit the ability to schedule priority processes to only the Administrators group.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
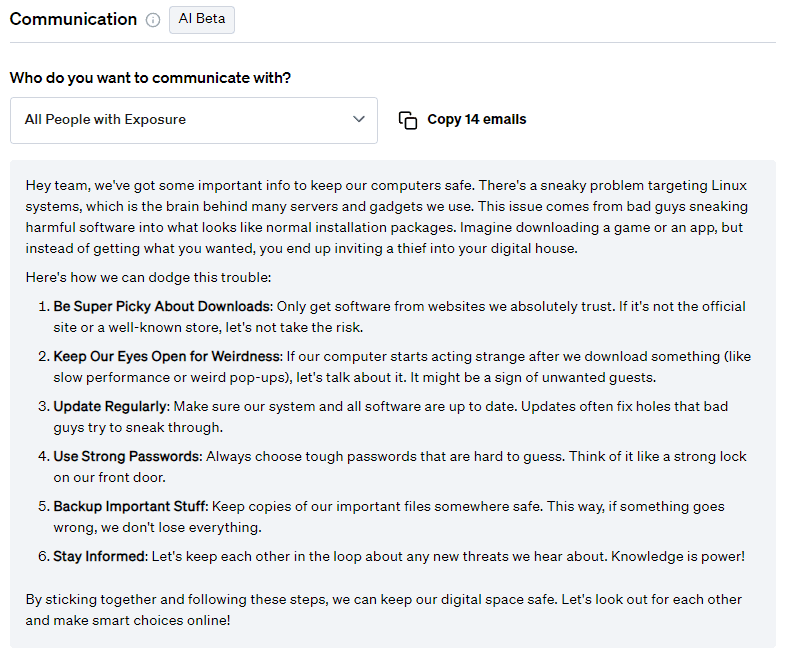
For Customers:

For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The discovery of Gomir underscores Kimsuky’s ongoing evolution and the sophistication of their tactics. Their focus on using trojanized software packages and supply chain attacks to infiltrate systems emphasizes the importance of enhanced security measures. Organizations, particularly in South Korea, should be vigilant in their software sourcing and updates to mitigate the risk of such sophisticated cyber threats.
Kimsuky is just one example of an ever evolving threat that requires in-depth cyber intelligence to stay on top of. Fletch helps you keep track of, and prioritizes, them all.
As the de facto record on the threat landscape, our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, detect threats to your tech and people early, or simply to become an instant expert on any threat at any time.
Join Fletch and try it for yourself.

1. CISO2CISO [North Korea-linked Kimsuky used a new Linux backdoor in recent attacks](https://ciso2ciso.com/north-korea-linked-kimsuky-used-a-new-linux-backdoor-in-recent-attacks-source-securityaffairs-com/)
2. SC Media [Feds warn of new Kimsuky phishing attack techniques](https://www.scmagazine.com/brief/feds-warn-of-new-kimsuky-phishing-attack-techniques)
3. Rewterz [North Korean APT Kimsuky Aka Black Banshee – Active IOCs](https://www.rewterz.com/rewterz-news/rewterz-threat-alert-north-korean-apt-kimsuky-aka-black-banshee-active-iocs-22)
4. SecurityWeek [Suspected N. Korean Hackers Target S. Korea-US Drills](https://www.securityweek.com/suspected-n-korean-hackers-target-s-korea-us-drills/?web_view=true)

