Product

Kenisha Liu
Dec 19, 2023
The Fletch platform allows you to live ahead of cyberthreats by discovering and prioritizing your threats sooner than traditional platforms ever could. Leave all of your hours of threat research and correlation to the AI so you can get back to important decision making and strategizing. When you get back to check Fletch, you’ll be greeted by a short list of the threats that actually matter to you, organized by severity. Let’s break down how to get started with Fletch.
Fletch Overview
Prioritize your vulnerability and malware alerts
Discover threats targeting your software supply chain early
Discover threats targeting your people early
Fletch Overview
Fletch uses artificial intelligence (AI) backed by human expertise to index the threat landscape and community and correlate it all to your data.
Fletch works with four main data sources: your public domain, SSO metadata, vulnerability scanners, and EDR tools.*
Without connecting any data, Fletch can show you the threats targeting your domain and industry. However, the more data you connect, the more data our AI engine can correlate to the threat landscape, the richer your profile will be.
Not seeing something? Give Fletch 24 hours to populate after connecting your tools.
Your Correlated Threats feed
When you login to Fletch, you’ll be brought to your Fletch Correlated Threats feed where things are already simplified for you.
Your threats will be prioritized for you into smart sets prioritized from left to right by key correlation; malware and vulnerabilities, internal tech, external tech, industry, and geo. The sets will not have overlapping threats, and threats will only appear in the prioritized key correlation
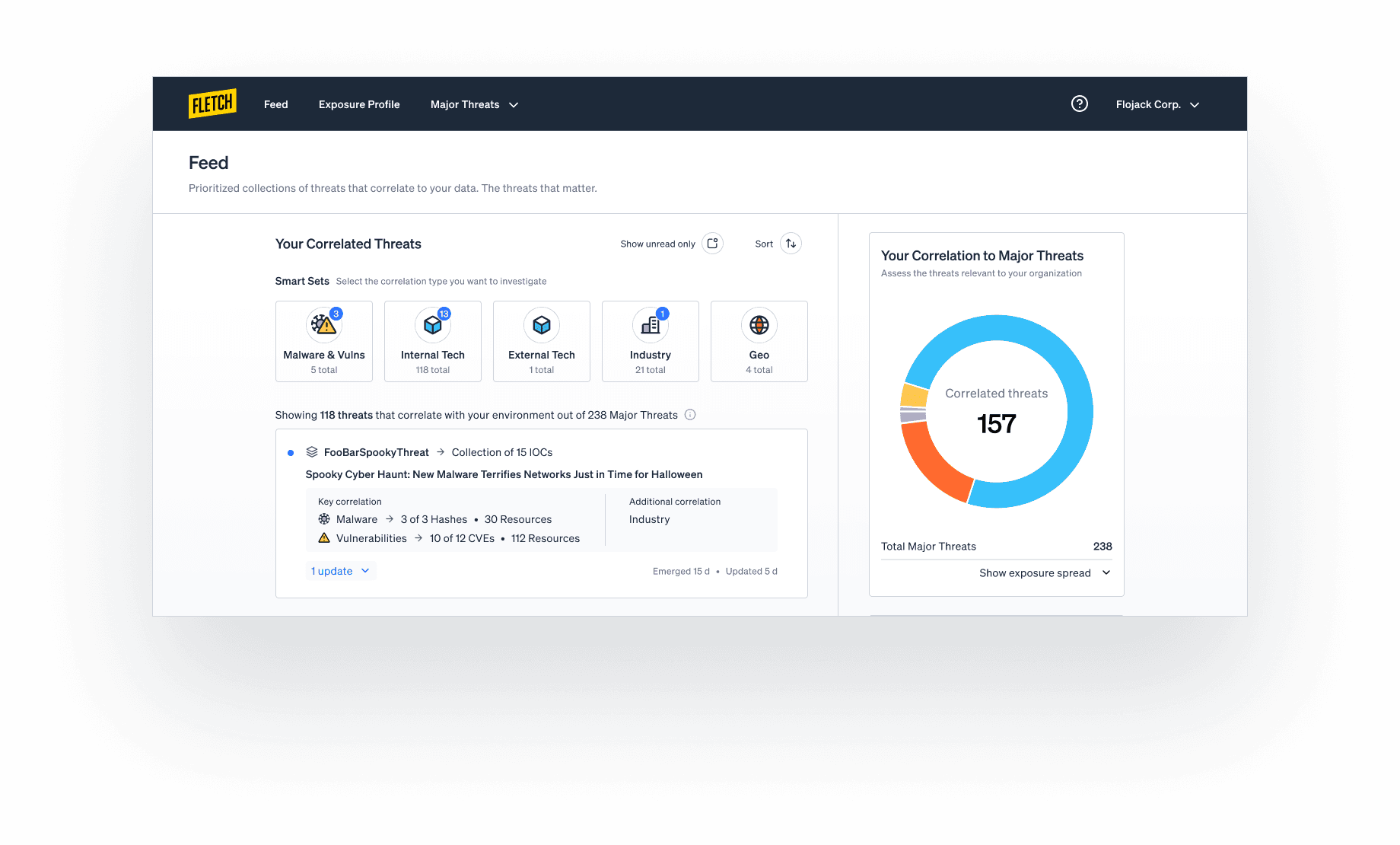
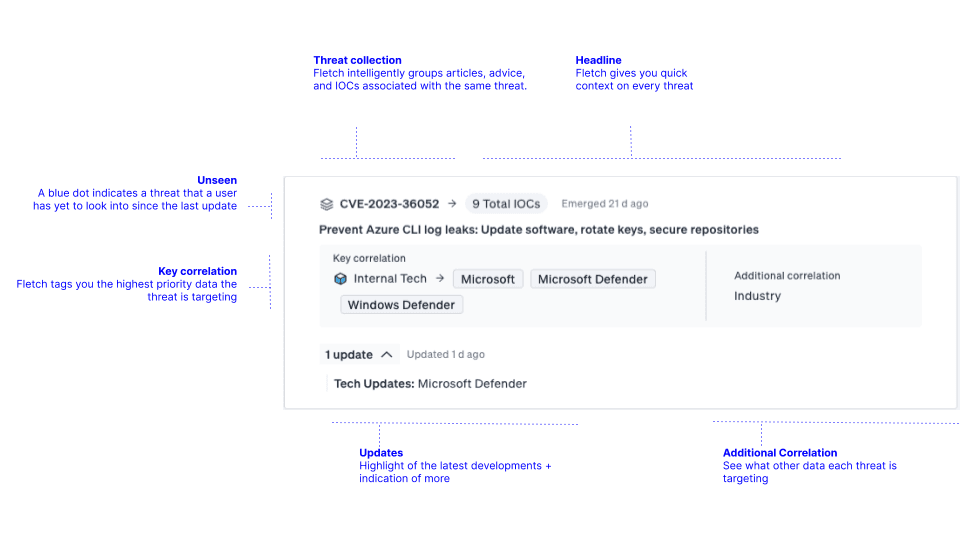
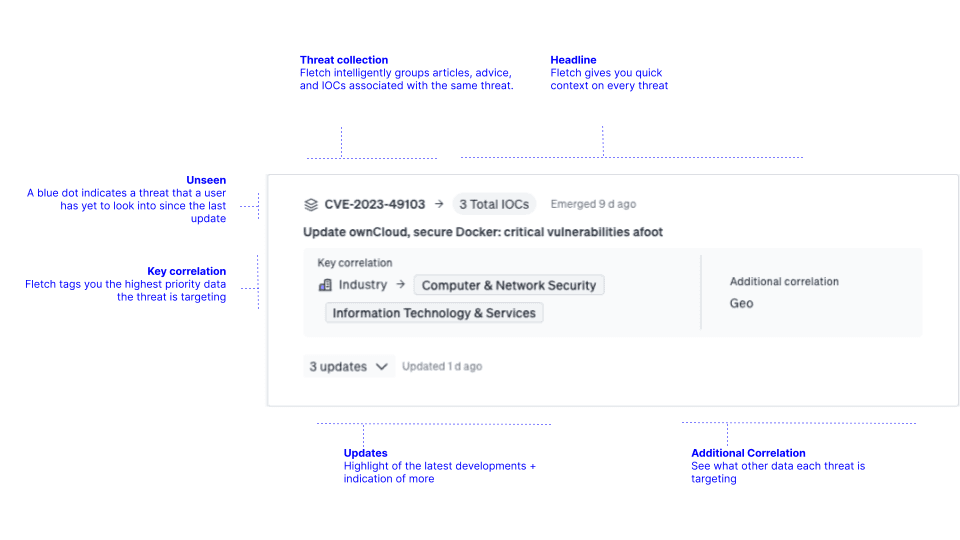
And to streamline the threat landscape, threats are intelligently grouped into Threat Collections. These encompass all the articles, advice, and IOCs associated with the same threat as it evolves. The name associated with the Threat Collection will be based on either the first CVE associated with the threat, the first malware family name associated with the threat, or the first threat group name exploiting the threat.
You can also sort by unread threats, threat severity, or last updated threat.
Remember, your Correlated Threat feed is the threat landscape in the context of your world. For information on what’s trending in the threat landscape in general, navigate to the Major Threats tab at the top and click ‘All Major Threats’. Then filter and sort the threat landscape however you like.
Now that we’re through the basics, here are some common ways that cybersecurity teams use Fletch:
Prioritizing your vulnerability and malware alerts
Discovering threats targeting your software supply chain early
Discovering threats targeting your people early
Let’s dive into the basics of using Fletch for each of these.
Quick Fletch setup by use case
Prioritize your vulnerability & malware alerts with Fletch
Fletch enhances your existing tools to screen, group, and prioritize all your vulnerability scanner and EDR alerts, transforming thousands of alerts to dozens. Now you can skip ahead in your day to get through the short list of threats that matter.
To get started on prioritizing your alerts in Fletch, be sure to take 10 minutes to connect your vulnerability scanner and EDR first.
Navigating your vulnerability and malware alerts
It’ll take about 24 hours for the data to propagate. Once you’re connected, your Correlated Threats feed will default to your set of threats with vulnerability and malware.
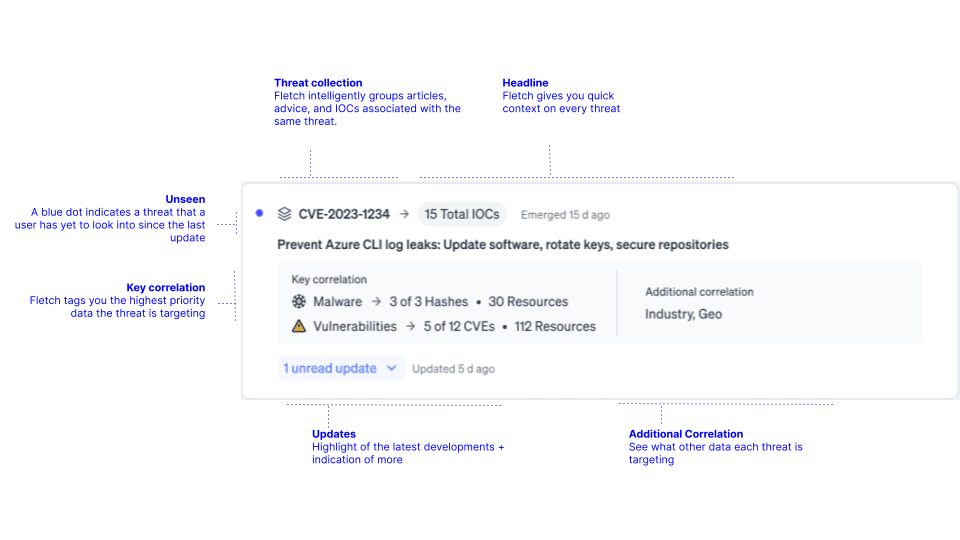
You’ll find a manageable list of threats that are organized into threat collections and prioritized by the number of resources compromised as well as the severity deemed by community sentiment. Use each of the threat cards in your threat feed to give you quick information to decide what to tackle first. You can see how many CVEs, malware hashes, or resources are affected. Or you can dig into new updates or any additional correlations.
Mitigating your vulnerability and malware alerts
When you need more information, click on the threat card to open its Threat Board. You’ll see a comprehensive knowledge base where you can find details on how the threat affects you including IOCs and properties correlated, threat severity, community chatter, or a complete history of the threat.
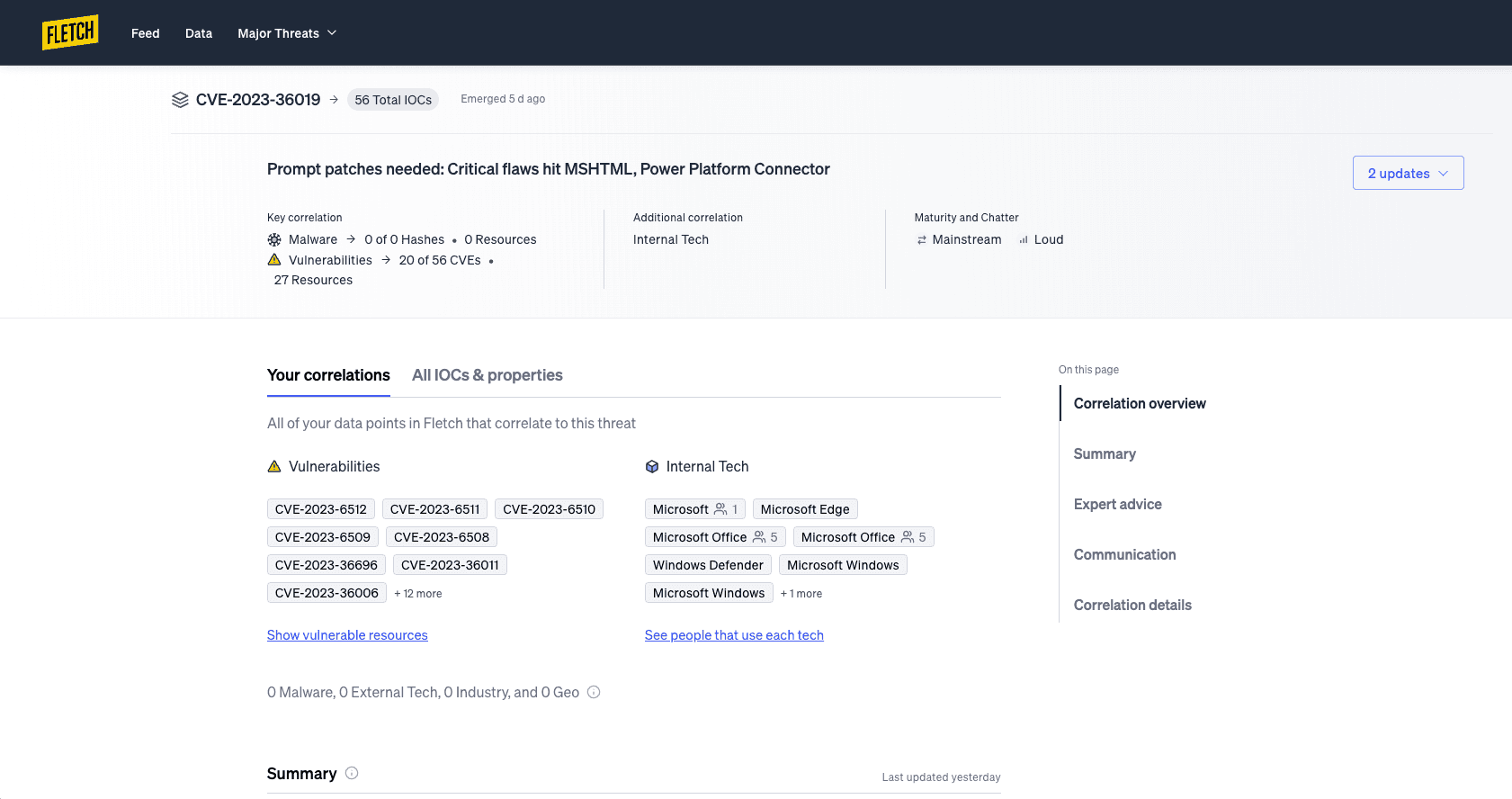
When you’re ready to take action, click on ‘Correlation Details’ on the right rail to see all the vulnerabilities and malware you have. Try out Fletch’s beta features that offer mitigation advice to fix your threat. Then when you’re ready to share with stakeholders, check out the ready-to-go comms on the right hand side. Select the audience you would like to inform and generate tailored communications for technical or non-technical employees alike.
Additional Tips
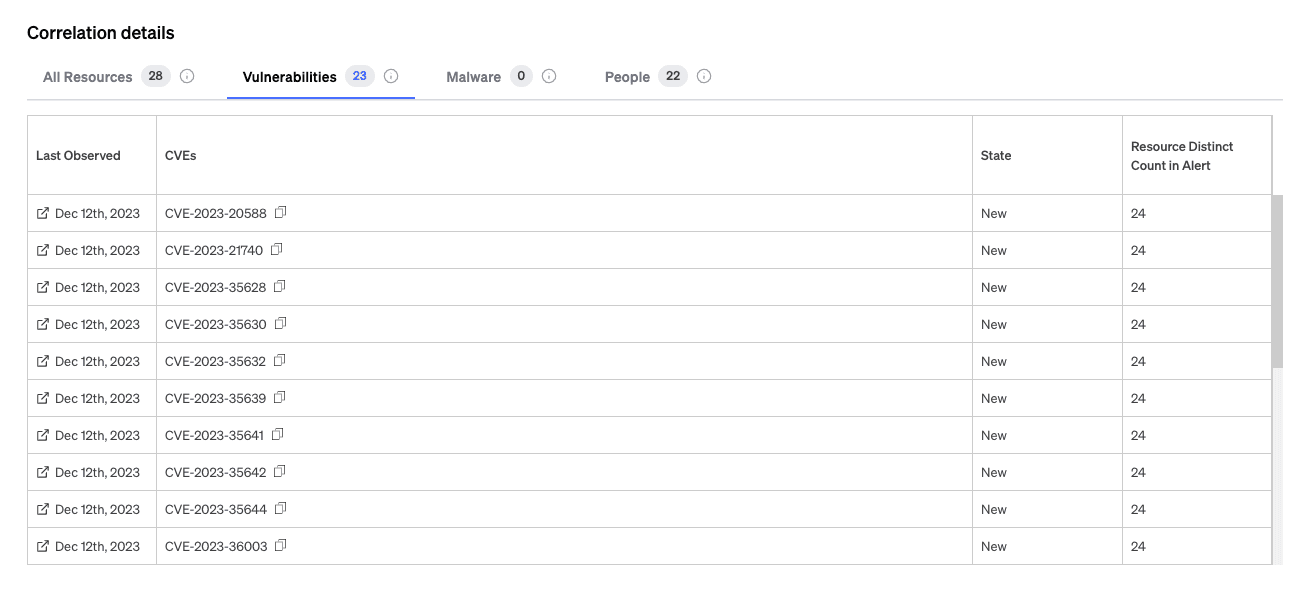
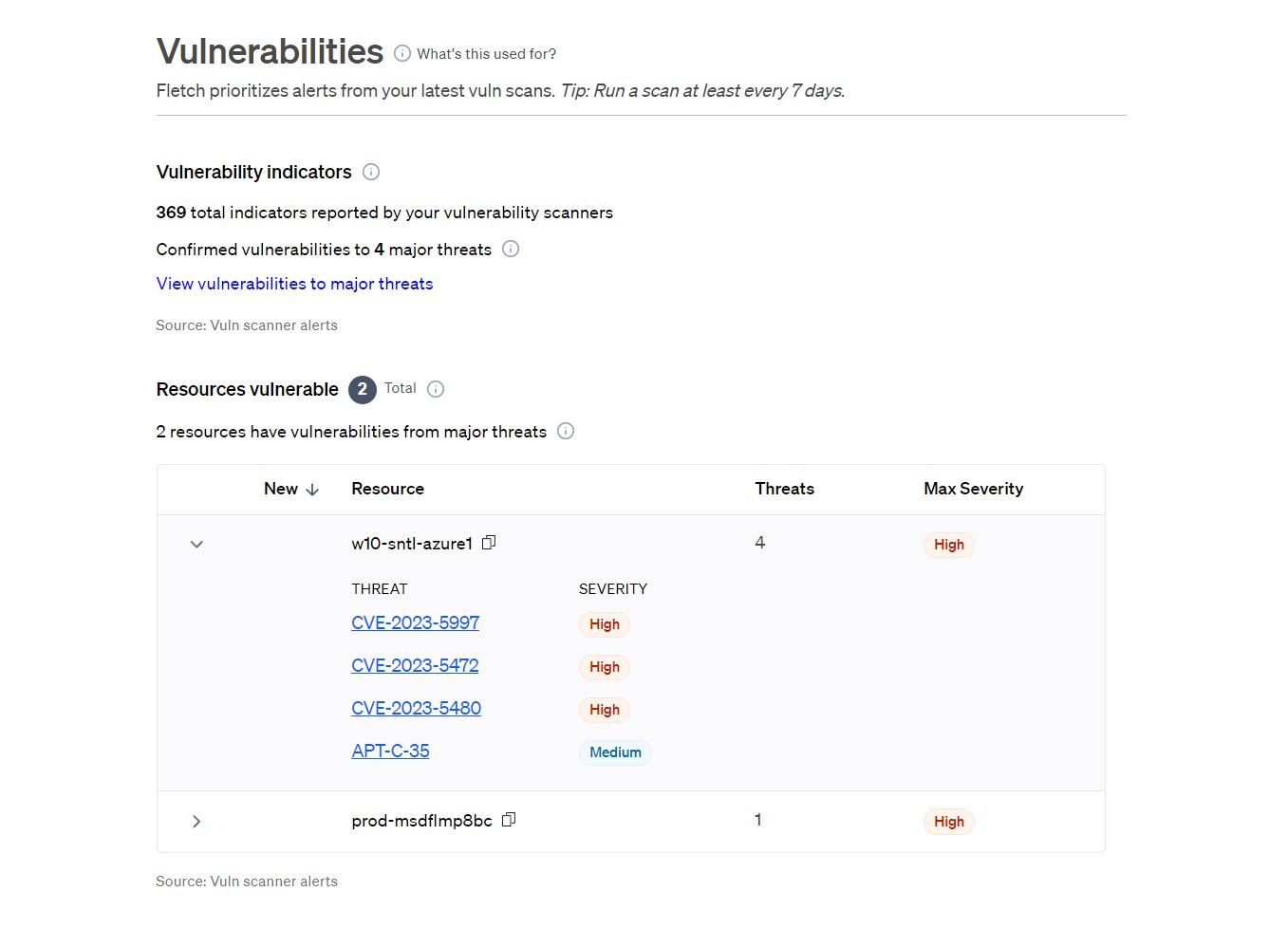
For an overview of your vulnerabilities and malware that actually matter, go to ‘Data’ on the top navigation bar, then ‘Vulnerabilities’ or ‘Malware’ to see a complete list of your resources with alerts associated with Major Threats. You can see the amount of threats associated with each vulnerability, the CVEs, and a severity score. You can see how many Major Threats each resource is vulnerable to or compromised by and the threat severity deemed by the cybersecurity community.
Open each resource to see the list of all Major Threats. Keep in mind, each resource might have multiple CVEs or hashes for each threat. Go to the Threat Board to find the full list for each resource.
Discover threats targeting your software supply chain early with Fletch
Fletch detects all the threats targeting your tech, from the software on your endpoints to the cloud applications used in your day-to-day. Now you can cut out all the manual threat research, correlation work, and threat feeds out of your life.
For early detection of your software supply chain threats with Fletch, be sure to take 10 minutes to connect your SSO first.
Fletch only uses your SSO metadata and doesn’t have access to any of your sensitive data.
Navigating your software supply chain threats
When your data is connected and you’ve given Fletch 24 hours to propagate the data, navigate to the “Internal Tech” tab in your Correlated Threats feed.
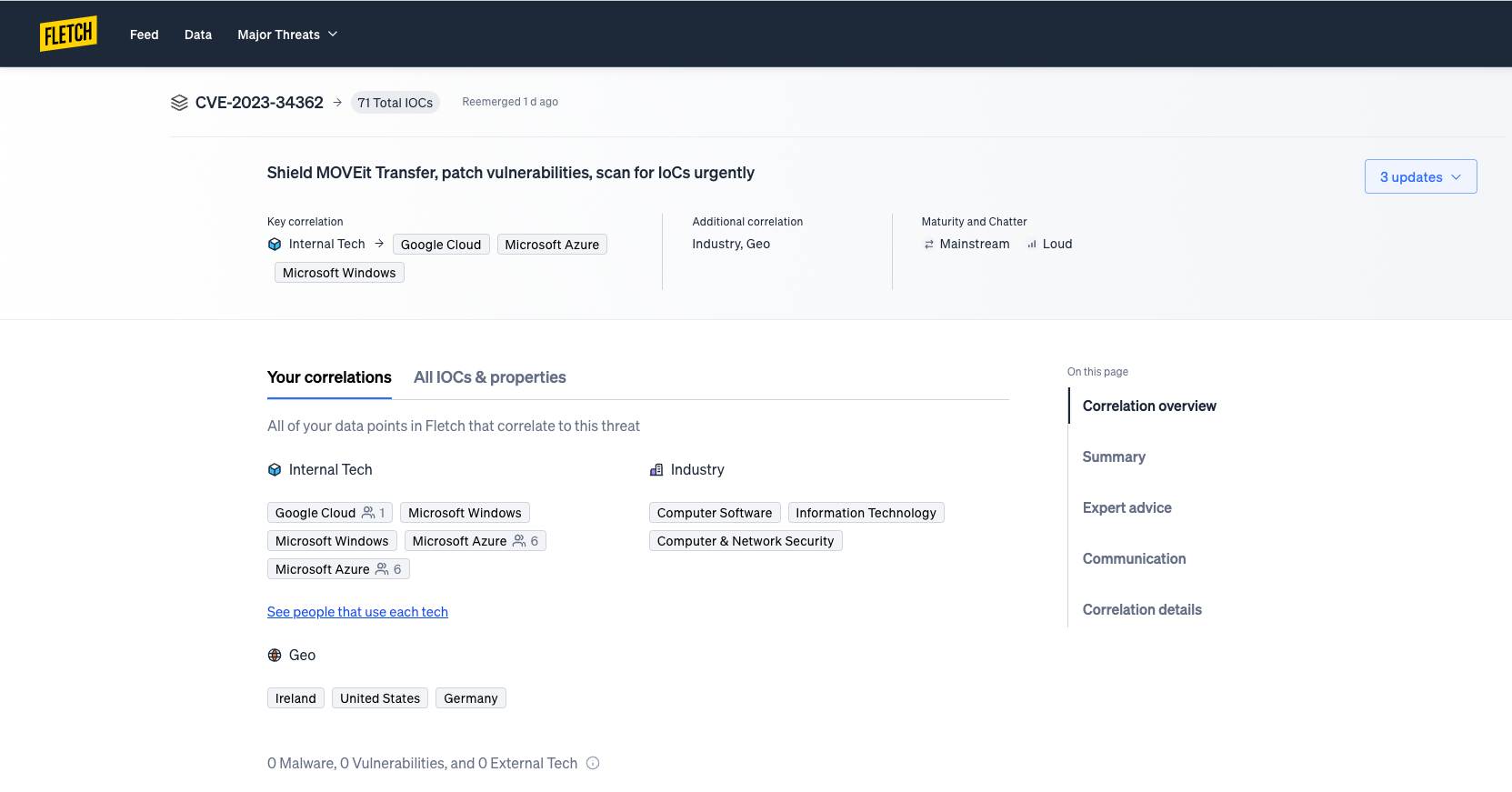
Here you’ll find the threats targeting all your SaaS technologies as a key correlation. These will be prioritized by the number of resources compromised as well as the severity deemed by community sentiment. Your threat card can show you how long ago it emerged and how recent any updates to threat occurred so you’re always ahead of the cusp. And it will show you what technologies are at risk, so you can move fast.
Mitigating your software supply chain threats
Once you’ve decided what to dig into, click into a threat card to open its Threat Board. All the context you need lives in a threat’s Threat Board. Get information on how the threat pertains to you, such as what’s affected or properties correlated. Or see details on the threat itself such as severity, community chatter, or a complete summary of the threat.
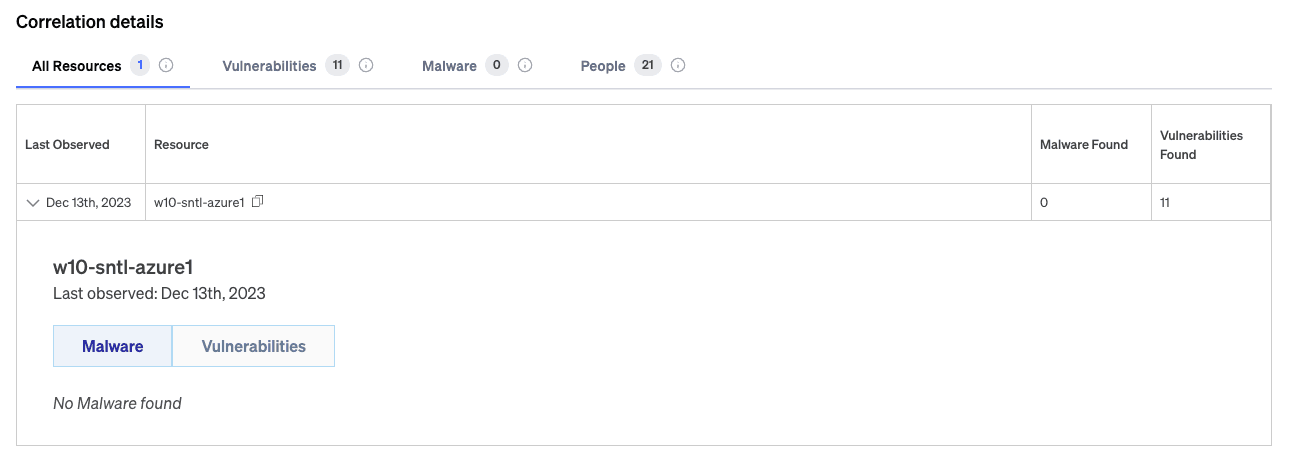
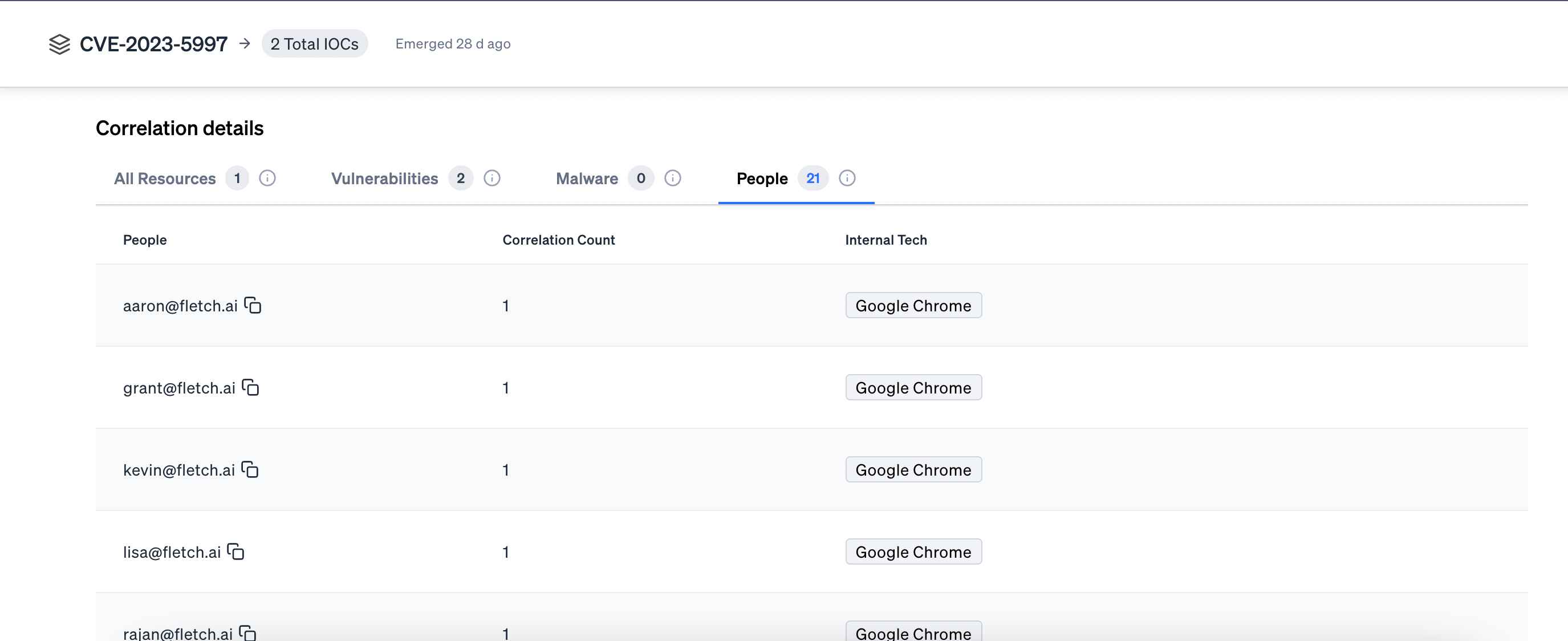
Then when it’s time to take action, click on ‘Correlation Details’ on the right rail. We’ll have compiled all your resources at risk and people using those resources. Test out our beta features. We provide advice that updates to every new threat evolution so you can preemptively protect yourself. Or use the audience specific communications to share the details to your stakeholders.
Additional Tips
For an overview of your software supply chain most at risk, you can navigate to ‘Data’ in the global navigation bar, then ‘Internal Technology’ to see a complete list of all your technologies, the number of threats targeting them, and a severity score. You might find Shadow IT that you didn’t know about before (since when were we using Dropbox?).
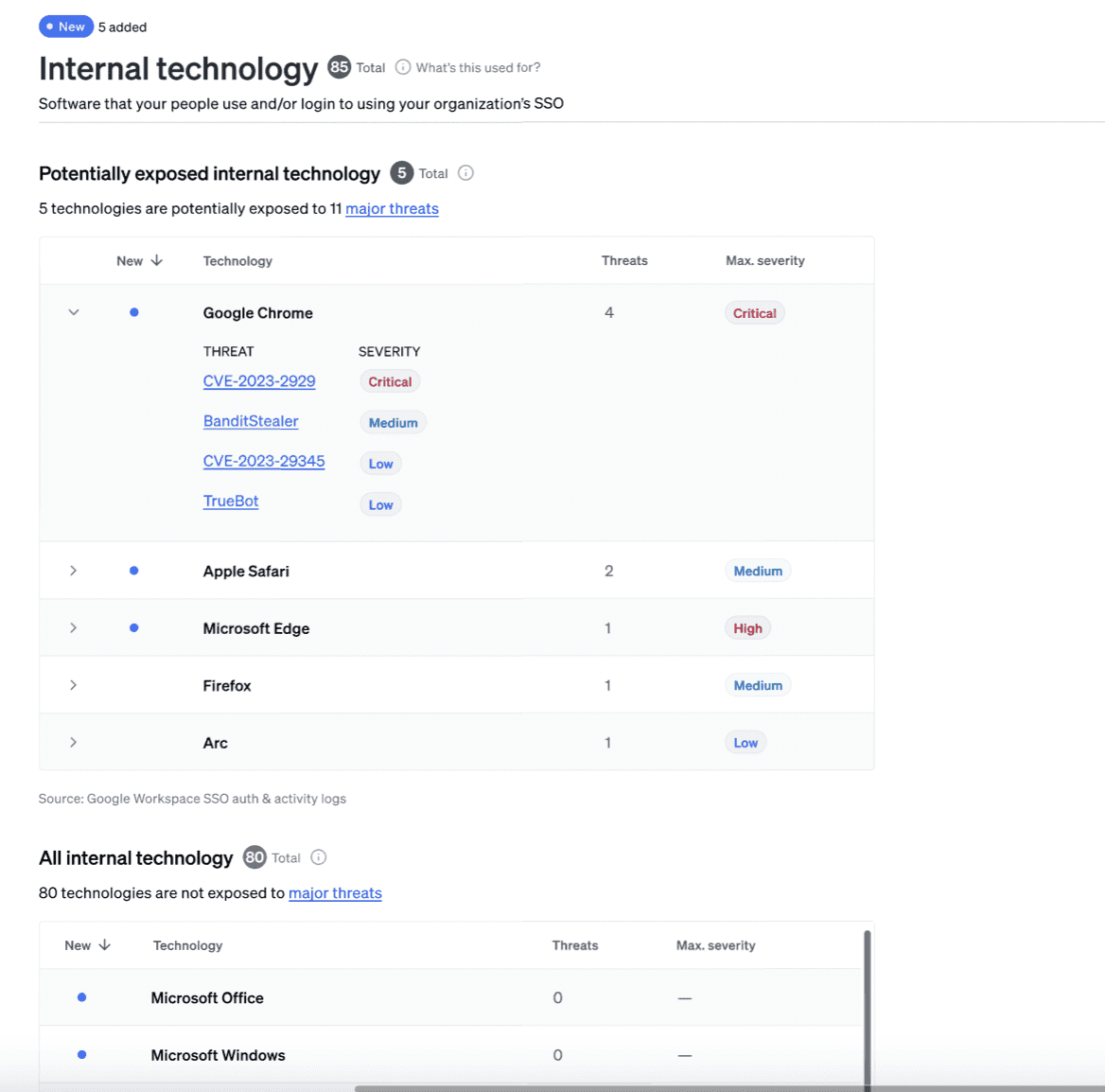
Note: Fletch prioritizes your threats for you based on what types of data correlate. You will not see all the threats targeting your SaaS software if the key correlation is a malware or vulnerability. It will appear under that set in your Correlated Threats feed.
To see all the threats targeting your SaaS software, navigate to the ‘All Major Threats’ tab in the global navigation bar and filter by ‘Internal Tech’.
Discover threats targeting your people early with Fletch
Fletch can show you the threats that target your people based on location or industry. No more stressing over your people’s activity, now you can protect and educate as it's relevant.
Seeing what threats target your industry requires no data connection. However to get ahead of the threats targeting your people’s location, be sure to take 10 minutes to connect your SSO first. It will take 24 hours for Fletch to propagate your data before you can see your geo threats.
Fletch only uses your SSO metadata and doesn’t have access to any of your sensitive data.
Navigating your people threats
Go to the ‘Industry’ or ‘Geo’ tab of your Correlated Threats feed.
Now you can see all the threats that are going after your people early. These will be prioritized by the number of resources compromised as well as the severity deemed by community sentiment. Each threat card gives you a quick snapshot on what's targeted and new updates to the threat so you can make quick judgment calls on what to focus on first.
Mitigating your people threats
When you know what’s most pressing, click the threat card to open its Threat Board. Each Threat Board gives you everything you need to know on that specific threat. This includes details on your correlation and what it’s targeting. As well as information on the threat itself, such as it’s severity, community chatter, and a complete summary of the threat from emergence to now.
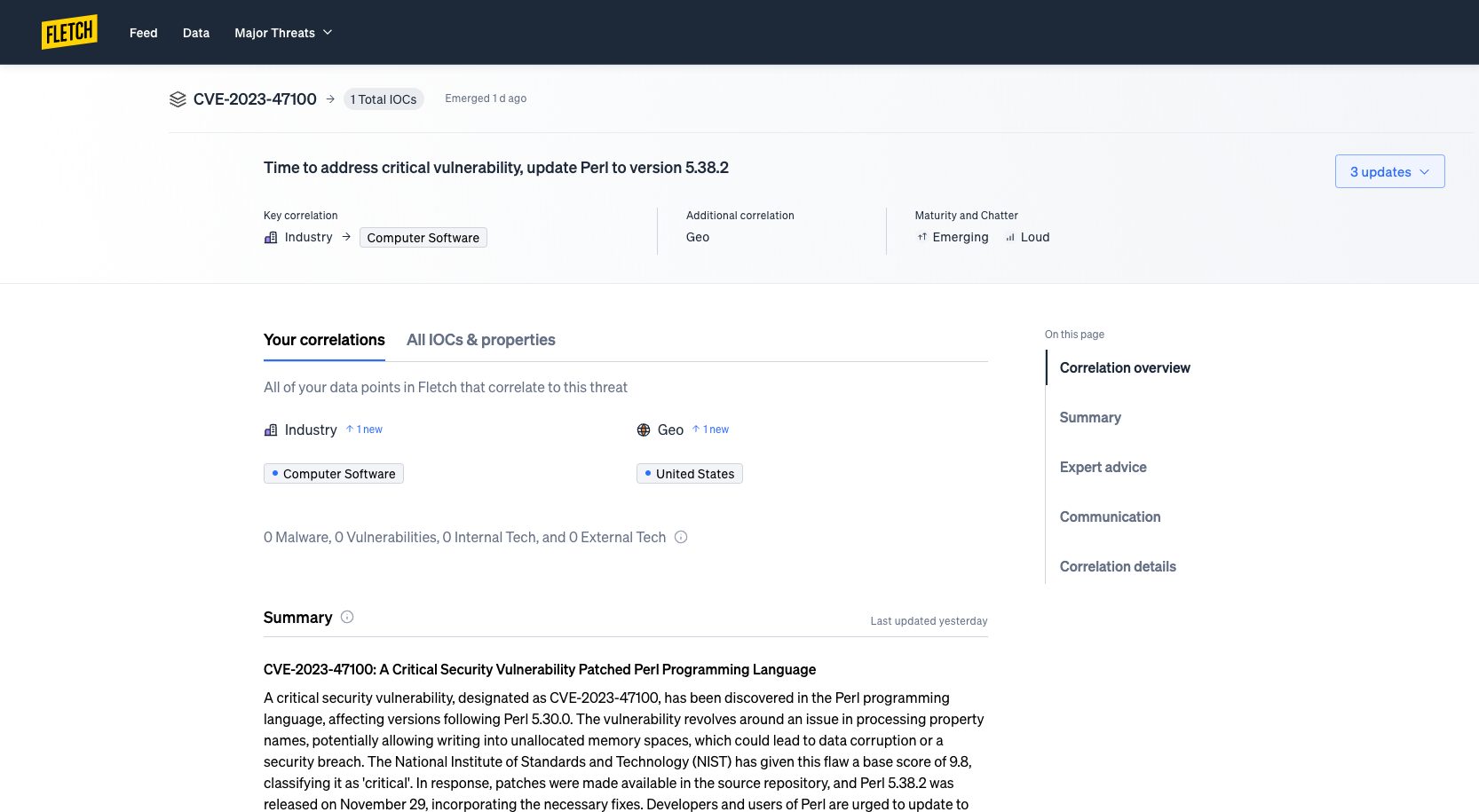
When you want to get ahead of your people threats, Fletch has got you covered.
For geo threats, click on ‘Correlation Details’ on the right rail to see specifically who is susceptible. Then you can use our beta communications feature to send them a tailored message, educating them on the threat and what to do.
For industry threats, try our beta advice for short term and long term mitigation strategies to start securing your company from the threat targeting you.
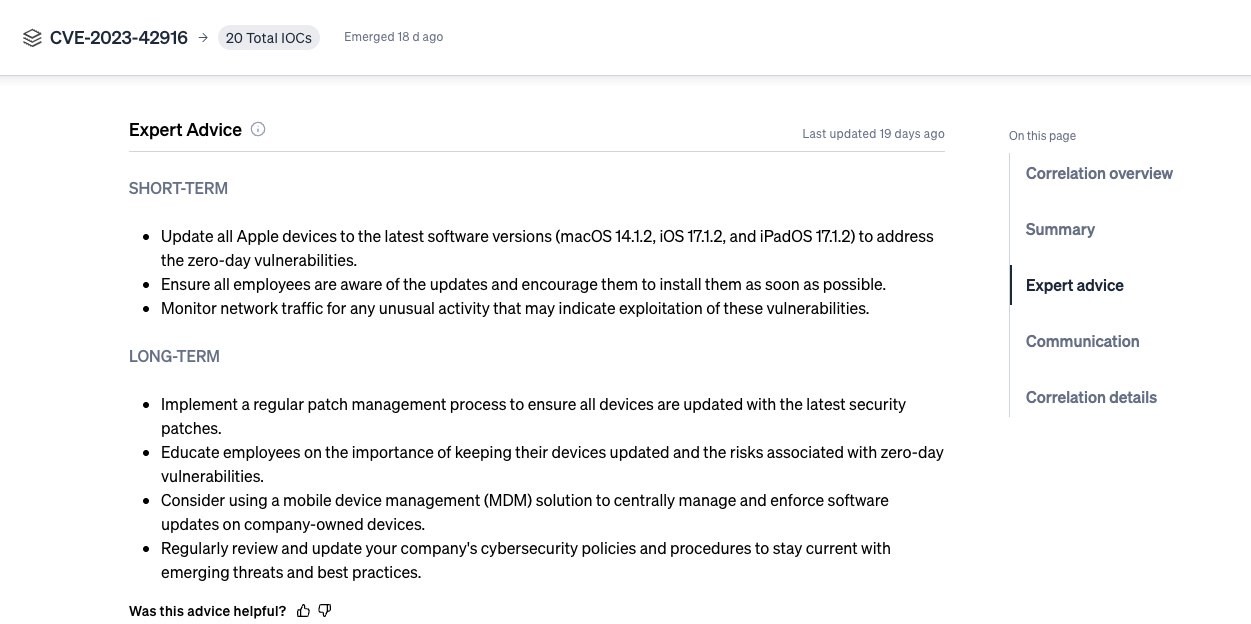
Additional tips
Last but not least, for a higher level idea of what’s most at risk, go to ‘Data’ in the top navigation bar and click either ‘Geography’ or ‘Industry’ for an overview of what is most correlated to threats in the threat landscape. You might even find information on your company you didn’t even know (Greg from IT is working from Spain?).
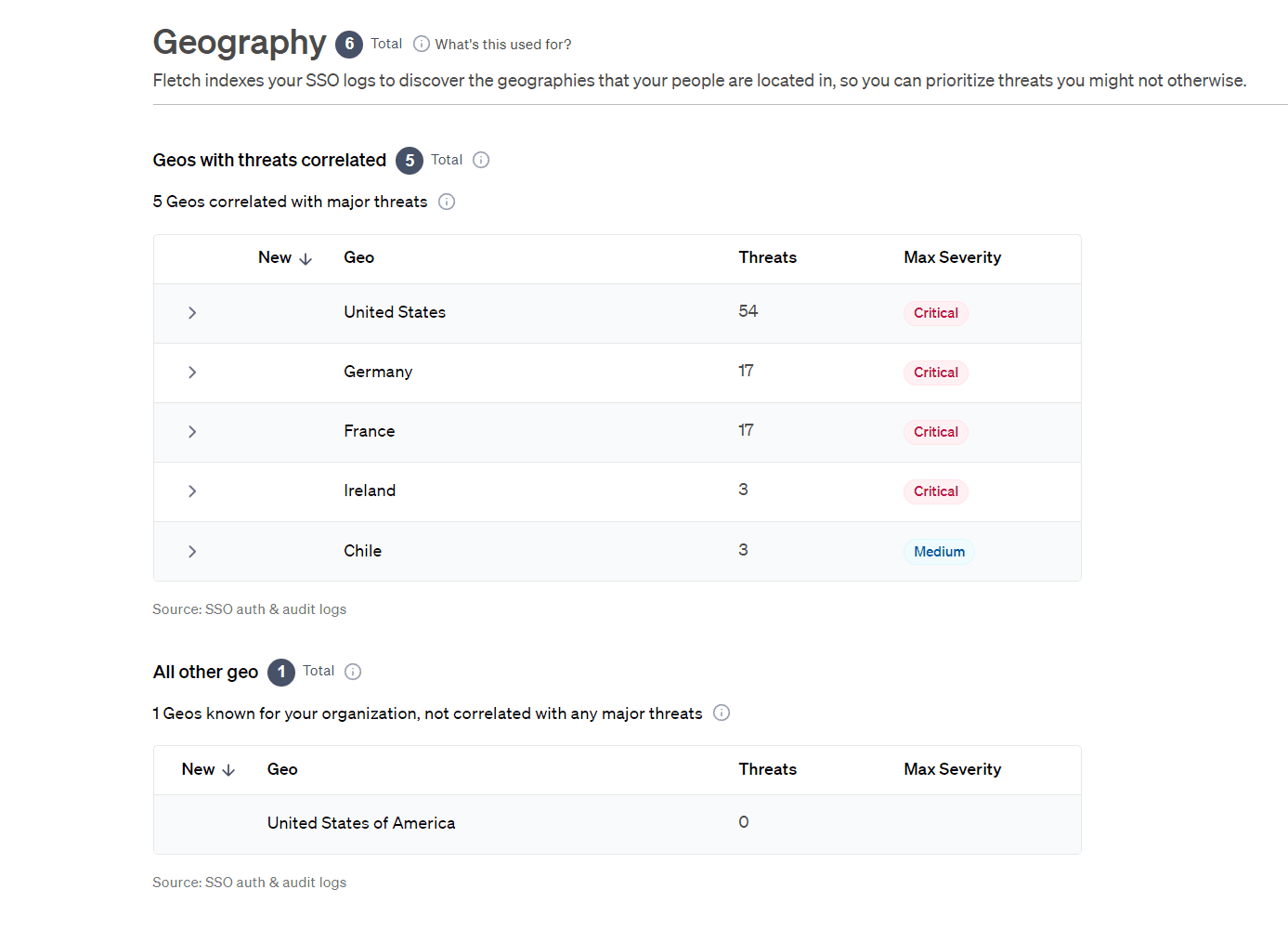
Note: Fletch prioritizes your threats for you based on what types of data correlate. You will not see all the threats targeting your industry or geography if the key correlation is a malware, vulnerability, SaaS software, or External Tech. It will appear under that set in your Correlated Threats feed.
To see all the threats targeting your people, navigate to the ‘All Major Threats’ tab in the global navigation bar and filter by ‘Geo’ or ‘Industry’.
Sign up for the Fletch waitlist to start living ahead of threats.


