Product

Jake Trujillo
Jul 26, 2024
Latest Headline
In 2024, the FIN7 ransomware group has been observed enhancing their attack strategies and broadening their criminal activities. Recent activities have included distributing malware via malicious Google Ads and collaborating with other ransomware groups such as Black Basta and Clop.
Key Points:
Emerged in 2012
Collaborates with Ransomware-as-a-Service (RaaS) groups like REvil, Conti, and more
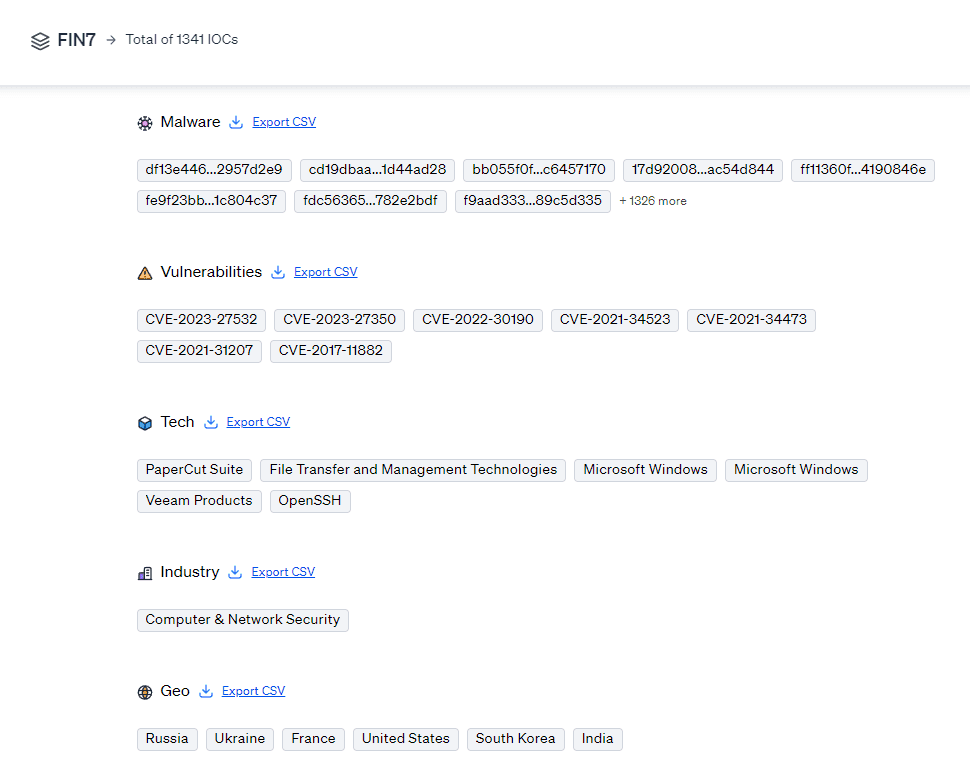
1341 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out FIN7’s Threat Board for any updates or join Fletch to be in the know for every threat.
FIN7 Summary
FIN7, also known as Carbanak, Navigator Group, and Carbon Spider, is a Russian cybercriminal group that initially focused on malware targeting point-of-sale terminals, but since 2020 has shifted towards ransomware operations linked to other high-profile operations. Despite the arrests of some members, the group continues to evolve, employing advanced techniques and sophisticated evasion tools. They are known for their ability to create fake cybersecurity companies to facilitate their operations and sell sophisticated tools on criminal forums.
Emerged: 2012
Severity: High
Maturity: Mainstream
IOCs: 1334 malware hashes and 7 vulnerabilities
Targets: 6 tech targets, 1 industry target, and 6 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
FIN7 Victims & Motivations
FIN7 primarily targets technologies like Microsoft Exchange servers, POS systems, and endpoint security solutions. Their victims span various industries, including manufacturing, legal, government, and critical infrastructure sectors, with a significant focus on U.S. companies. The group’s motivations are predominantly financial, seeking to gain through ransomware attacks and by selling tools on underground forums. Their tactics demonstrate a high level of adaptability and technical sophistication, posing a persistent threat to global cybersecurity.
FIN7 Tactics
FIN7 employs a variety of sophisticated methodologies, including the use of fake companies, exploitation of vulnerabilities like ProxyShell, and automated SQL injection attacks. They have developed several advanced tools such as AvNeutralizer and Checkmarks, and they have leveraged legitimate Windows drivers to bypass security. Their use of malvertising tactics to distribute malware via Google Ads exemplifies their innovative approach to cyber attacks.
Mitigation Advice
At the time of publication this was the mitigation advice against FIN7:
Update and patch Veeam Backup & Replication software to address the CVE-2023-27532 vulnerability.
Restrict the use of OpenSSH and Impacket to only authorized personnel and systems.
Configure web browsers to block or alert on downloads of MSIX files, if possible, to prevent accidental installation of malicious packages.
Block known malicious IP addresses associated with FIN7, especially those related to Stark Industries hosting.
At the time of publication these were the right compliance controls to focus on for FIN7:
Limit the use of PowerShell to only administrators and restrict what commands can be executed.
Limit the use of PowerShell to only administrators and restrict what commands can be executed.
Require employees to use a username and password along with a physical smart card or token generator to access the system.
Install and regularly update antivirus software on all company devices.
Limit the number of user accounts that can access the system via SSH.
You can check out the most recent mitigation measures when you create an account with Fletch.
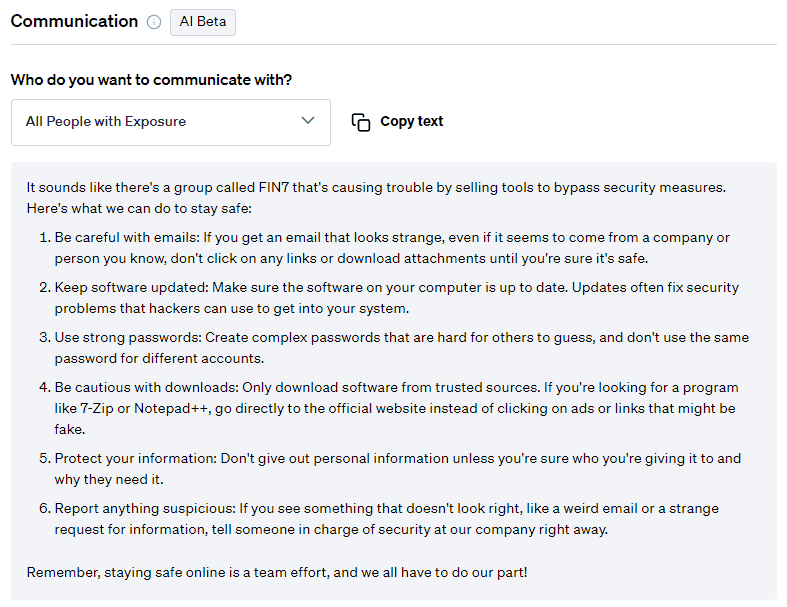
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
For customers:

For more templates for your different stakeholders, create an account with Fletch.
Takeaway
FIN7 continues to be a significant threat due to its ability to adapt and evolve its tactics to stay ahead of security measures. Their operations highlight the critical need for robust cybersecurity measures and vigilance, particularly in industries that are frequent targets. Their collaboration with other ransomware groups and use of sophisticated evasion techniques pose ongoing risks to global cybersecurity.
FIN7 is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.

1. [Krebs on Security](https://krebsonsecurity.com/2024/07/the-stark-truth-behind-the-resurgence-of-russias-fin7/)
2. [The Hacker News](https://thehackernews.com/2024/07/fin7-group-advertises-security-bypassing.html)
3. [Bleeping Computer](https://www.bleepingcomputer.com/news/security/black-basta-ransomware-gang-linked-to-the-fin7-hacking-group/)
4. [Black Hat News](https://www.blackhat.news/fin7-hacker-group-utilizes-malicious-google-ads-to-distribute-netsupport-rat)
5. [Cybersecurity News](https://cybersecuritynews.com/fin7-hackers-abuse-sponsored-google-ads-to-deliver-msix-payloads/)

