Product

Jake Trujillo
Sep 17, 2024
Latest Headline
Two critical vulnerabilities in Ivanti’s software surfaced in September 2024, raising immediate concern for users of Ivanti Endpoint Manager (EPM) and Ivanti Cloud Services Appliance (CSA). These vulnerabilities, CVE-2024-29847 and CVE-2024-8190, enable remote code execution (RCE) and command injection, respectively. While Ivanti has issued patches for both, CVE-2024-8190 is already being actively exploited in the wild, urging security teams to act quickly.
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out CVE-2024-8190’s Threat Board to see how likely you are to be affected and for any updates, or join Fletch to be in the know for every threat.
Summary
CVE-2024-29847, discovered in the AgentPortal.exe of Ivanti Endpoint Manager, is a critical vulnerability rooted in the deserialization of untrusted data. This flaw allows remote attackers to execute arbitrary code without requiring authentication, making it an especially severe threat. The vulnerability affects versions prior to 2022 SU6 and EPM 2024, and the public release of a proof-of-concept (PoC) exploit significantly increases the risk of it being weaponized in upcoming attacks.
Similarly, CVE-2024-8190 targets Ivanti CSA (versions 4.6 and earlier) and allows authenticated attackers with admin privileges to exploit a command injection flaw via the /datetime.php endpoint. Despite requiring administrative access for exploitation, this vulnerability has already been used in real-world attacks just days after its disclosure. CSA 4.6 has reached its end of life (EOL), and the last patch (4.6 Patch 519) will be its final update, urging users to upgrade to CSA 5.0 for continued security.
Emerged: September 2024
Severity: Critical
Maturity: Mainstream
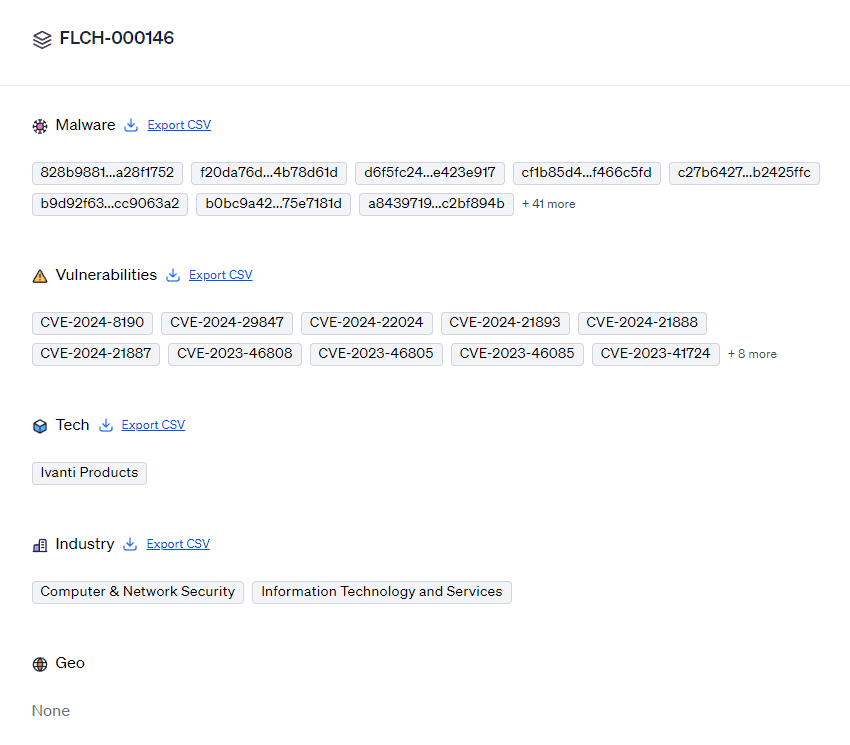
IOCs: 49 malware hashes and 18 vulnerabilities
Targets: 1 tech target, 2 industry targets, and 0 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
Victims & Motivations
Organizations across various sectors, especially those relying on Ivanti for IT management and enterprise infrastructure, are at risk. Over 1,200 instances of Ivanti CSA are publicly exposed online, with a significant number located in the United States. Industries such as healthcare, finance, and government are particularly vulnerable, as Ivanti products are often used to manage large-scale operations and sensitive data.
The motivations behind these attacks appear to be gaining unauthorized access to critical systems. Attackers exploiting these vulnerabilities can install backdoors, escalate privileges, or exfiltrate sensitive data, making them attractive targets for espionage, financial fraud, and service disruption. The active exploitation of CVE-2024-8190 underscores the urgent need for organizations to upgrade to supported software versions and apply security patches immediately.
Tactics & Exploits
The tactics employed by attackers vary between the two vulnerabilities. For CVE-2024-29847, attackers exploit the insecure deserialization of objects within AgentPortal.exe, enabling them to inject malicious payloads that are executed upon deserialization. This can include executing commands such as installing web shells or gaining remote control of the system. The use of .NET Remoting, an outdated framework, exacerbates the risk, as attackers can bypass low-level filters designed to prevent such deserialization.
In contrast, CVE-2024-8190 is exploited through an OS command injection within CSA. Although admin privileges are required, the risk lies in weakly configured administrative interfaces or easily guessed passwords, which allow attackers to remotely execute commands that compromise the system. The vulnerability was patched in CSA 4.6 Patch 519, but the EOL status of CSA 4.6 means users must migrate to CSA 5.0 for long-term protection.
Mitigation Advice
At the time of publication this was the mitigation advice against CVE-2024-8190:
Review and apply updates for Ivanti Workspace Control (IWC) and Ivanti Cloud Service Appliance (CSA) to mitigate high-severity shortcomings.
Temporarily disable the AgentPortal service if patching is not immediately possible and if it does not critically impact business operations.
Immediately apply security patches released by Ivanti for affected ZTA and Connect Secure versions; Update Ivanti Connect Secure and Policy Secure systems to the latest versions immediately; Update all Ivanti Pulse Secure VPN appliances to the latest firmware version; Ensure that all Ivanti Pulse Secure appliances are running the latest available versions.
Conduct a security audit of current Ivanti installations to ensure no version is left unpatched.
Run Ivanti's External Integrity Checker Tool on all Ivanti VPN appliances and take additional steps if indications of compromise are detected.
At the time of publication these were the right compliance controls to focus on for CVE-2024-8190:
Limit the use of PowerShell to only administrators and restrict what commands can be executed.
Install and regularly update antivirus software on all company devices.
Install script blocking extensions and adblockers on all company computers.
Enable Attack Surface Reduction rules on Windows 10 to prevent potentially harmful scripts from running.
Implement application control, such as PowerShell Constrained Language mode, to restrict access to sensitive commands.
You can check out the most recent mitigation measures when you create an account with Fletch.
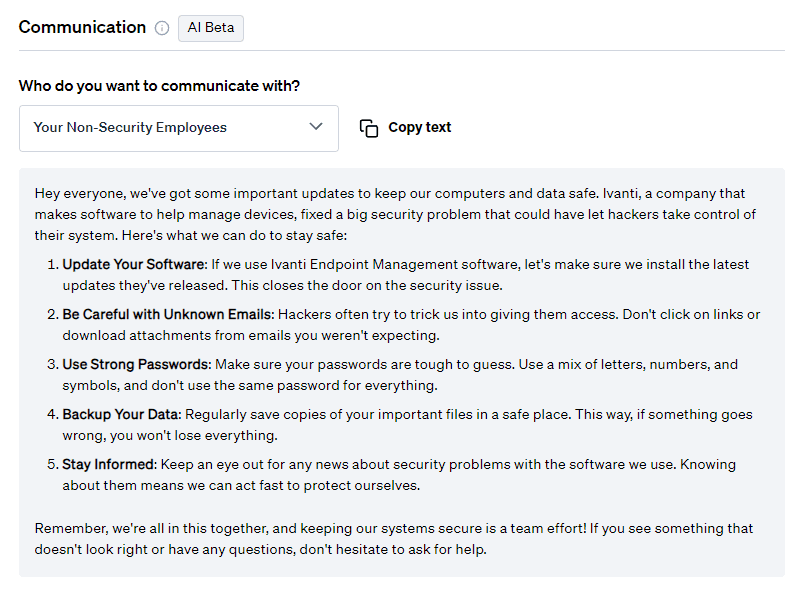
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
For customers:

For more templates for your different stakeholders, create an account with Fletch.
Takeaway
The discovery and immediate exploitation of these Ivanti vulnerabilities underscore the growing risk posed by unpatched enterprise software. CVE-2024-29847 and CVE-2024-8190 provide attackers with potent avenues for remote code execution, leaving organizations vulnerable to data breaches, ransomware, and other cyberattacks. Patching and upgrading to the latest versions of EPM and CSA is the only mitigation available, as no workarounds exist. Given the active exploitation of CVE-2024-8190, organizations are under pressure to act swiftly, especially with CISA's October 4, 2024, deadline for remediating these vulnerabilities. Failure to do so puts critical infrastructure and sensitive data at significant risk.
CVE-2024-8190 is just one example of an ever evolving threat that Fletch helps you forecast and defend yourself from.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and get daily advice on what to do.
Join Fletch and try it for yourself.

1. [SecurityWeek](https://www.securityweek.com/ivanti-csa-vulnerability-exploited-attacks-days-after-disclosure)
2. [Help Net Security](https://www.helpnetsecurity.com/2024/09/11/ivanti-cve-2024-29847/)
3. [BleepingComputer](https://www.bleepingcomputer.com/news/security/exploit-code-released-for-critical-ivanti-rce-flaw-patch-now/)

