Product

Jake Trujillo
Oct 8, 2024
Latest Headline
Apple has urgently released iOS 18.0.1 and iPadOS 18.0.1 to address two critical security vulnerabilities. The more concerning of the two issues, CVE-2024-44204, involved Apple's VoiceOver feature, which could read aloud saved passwords stored in the new Passwords app.
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out CVE-2024-44204’s Threat Board to see how likely you are to be affected and for any updates, or join Fletch to be in the know for every threat.
Summary
The first vulnerability, CVE-2024-44204, allowed the VoiceOver feature to bypass typical privacy settings by exposing users’ saved credentials. This vulnerability arose from a logic flaw in the application. Apple acted quickly after the bug was discovered by security researcher Bistrit Daha, releasing an update that affected a range of devices, including iPhone XS and later models, iPads, and the iPhone Pro series. Given the widespread use of VoiceOver among users with accessibility needs, this flaw presented a significant risk to a vulnerable user base. The fix implemented improved validation processes to ensure credentials are no longer exposed.
The second vulnerability, CVE-2024-44207, was related to iMessage audio messages on iPhone 16 models. This bug allowed audio to be recorded for a few seconds before the microphone indicator was visible, violating user expectations of privacy. Apple resolved the issue by enhancing checks that prevent premature audio capture.
This marks a notably proactive response to the security challenges posed by the rapid rollout of new features in iOS 18, which notably includes Apple’s first native password manager app.
Emerged: October 2024
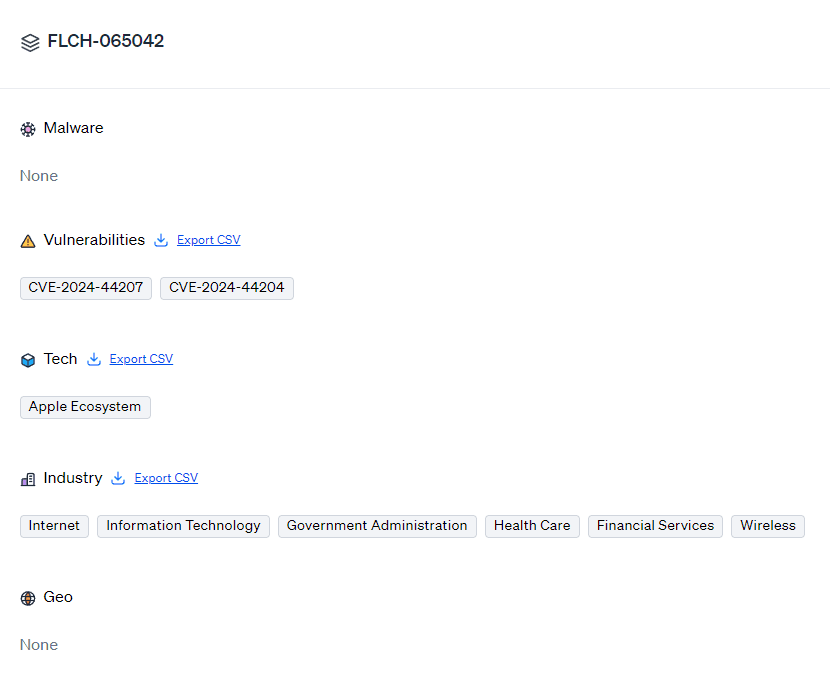
Severity: Critical
Maturity: Mainstream
IOCs: 0 malware hashes and 2 vulnerabilities
Targets: 1 tech target, 6 industry targets, and 0 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
Victims & Motivations
While no evidence has surfaced suggesting these vulnerabilities were exploited in the wild, they present serious privacy risks. The main victims of these flaws are everyday users, particularly those who rely on accessibility features like VoiceOver or frequently use audio messaging in iMessage. The scope of these vulnerabilities makes all Apple users across the globe potential victims, with the motivation for exploitation rooted primarily in unauthorized access to private information such as passwords or personal conversations.
Tactics & Tools
These vulnerabilities were notable not because of external malware or complex exploits, but because they exploited inherent flaws in Apple's new features, highlighting the importance of internal validation. The Passwords app’s logic flaw and the premature audio capture in iMessage demonstrate how even trusted system functionalities can pose risks without thorough testing.
Mitigation Advice
At the time of publication this was the mitigation advice against CVE-2024-44204:
Immediately update all Apple devices to the latest iOS and iPadOS versions to patch the identified vulnerabilities (CVE-2024-44204 and CVE-2024-44207).
Disable VoiceOver on devices where it is not needed to minimize the risk of the password vulnerability being exploited.
At the time of publication these were the right compliance controls to focus on for CVE-2024-44204:
Keep your mobile devices updated to the latest operating system version; prevent devices running outdated operating systems from accessing your data.
Educate users to be cautious when granting app permissions, especially for microphone or audio access.
Make sure to regularly backup all important data and keep these backups separate from the main network.
Enable cloud-delivered protection and Attack Surface Reduction rules on Windows 10.
You can check out the most recent mitigation measures when you create an account with Fletch.
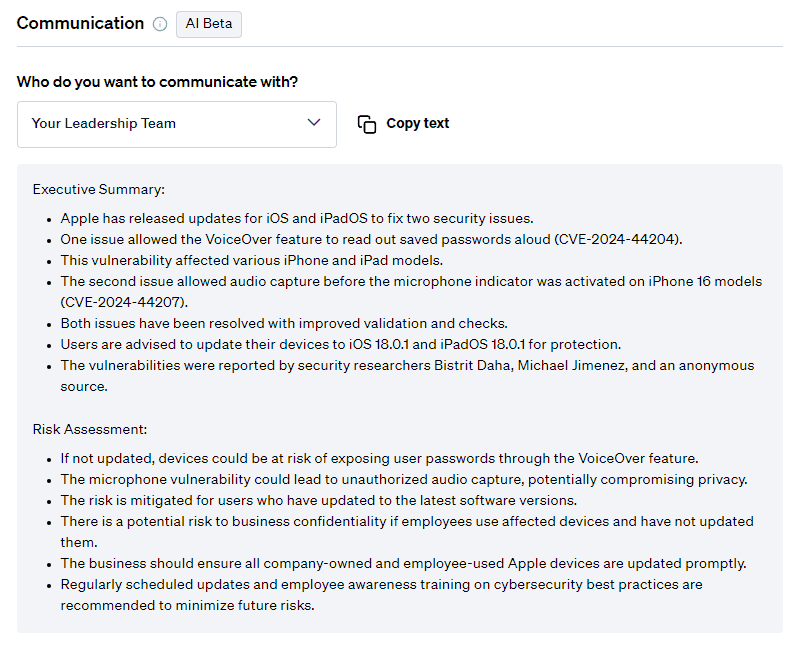
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:

For leadership:
For more templates for your different stakeholders, create an account with Fletch.
Takeaway
The vulnerabilities patched in iOS 18.0.1 and iPadOS 18.0.1 serve as a reminder of the importance of timely software updates, especially when new features like Apple’s password manager and VoiceOver’s accessibility functionalities are involved. Apple’s quick response reinforces the need for continuous improvement in privacy controls and internal validation processes. Users are urged to update their devices to the latest version to avoid potential breaches of sensitive information.
CVE-2024-44204 is just one example of an ever evolving threat that Fletch helps you forecast and defend yourself from.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and get daily advice on what to do.
Join Fletch and try it for yourself.

1. [Techworm](https://www.techworm.net/2024/10/apple-critical-update-ios-ipad-fix-voiceover-password.html)
2. [The Hacker News](https://thehackernews.com/2024/10/apple-releases-critical-ios-and-ipados.html)
3. [SecurityWeek](https://www.securityweek.com/apple-ios-18-0-1-patches-password-exposure-and-audio-snippet-bugs)

