Product

Finn Callaghan
Jul 31, 2024
Latest Headline
The SonicWall Capture Labs threat research team has identified a critical remote code execution vulnerability in GeoServer, designated as CVE-2024-36401. This vulnerability affects versions of GeoServer. Due to active exploitation in the wild, this vulnerability has been included in CISA’s Known Exploited Vulnerabilities Catalog.
Key Points:
Active since at least July 2024
Affects GeoServer, an open-source server that allows users to share and edit geospatial data.
No specific threat groups have been attributed to this vulnerability
2 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out CVE-2024-36401’s Threat Board for any updates or create an account with Fletch to be in the know for every threat.
CVE-2024-36401 Group Summary
While no specific threat groups have been attributed to this vulnerability, its exploitation in the wild signifies a considerable risk to any organization using affected GeoServer versions.
Severity: Critical
Maturity: Mainstream
IOCs: 2
Targets: 1 tech targets, 1 industry targets, and 6 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
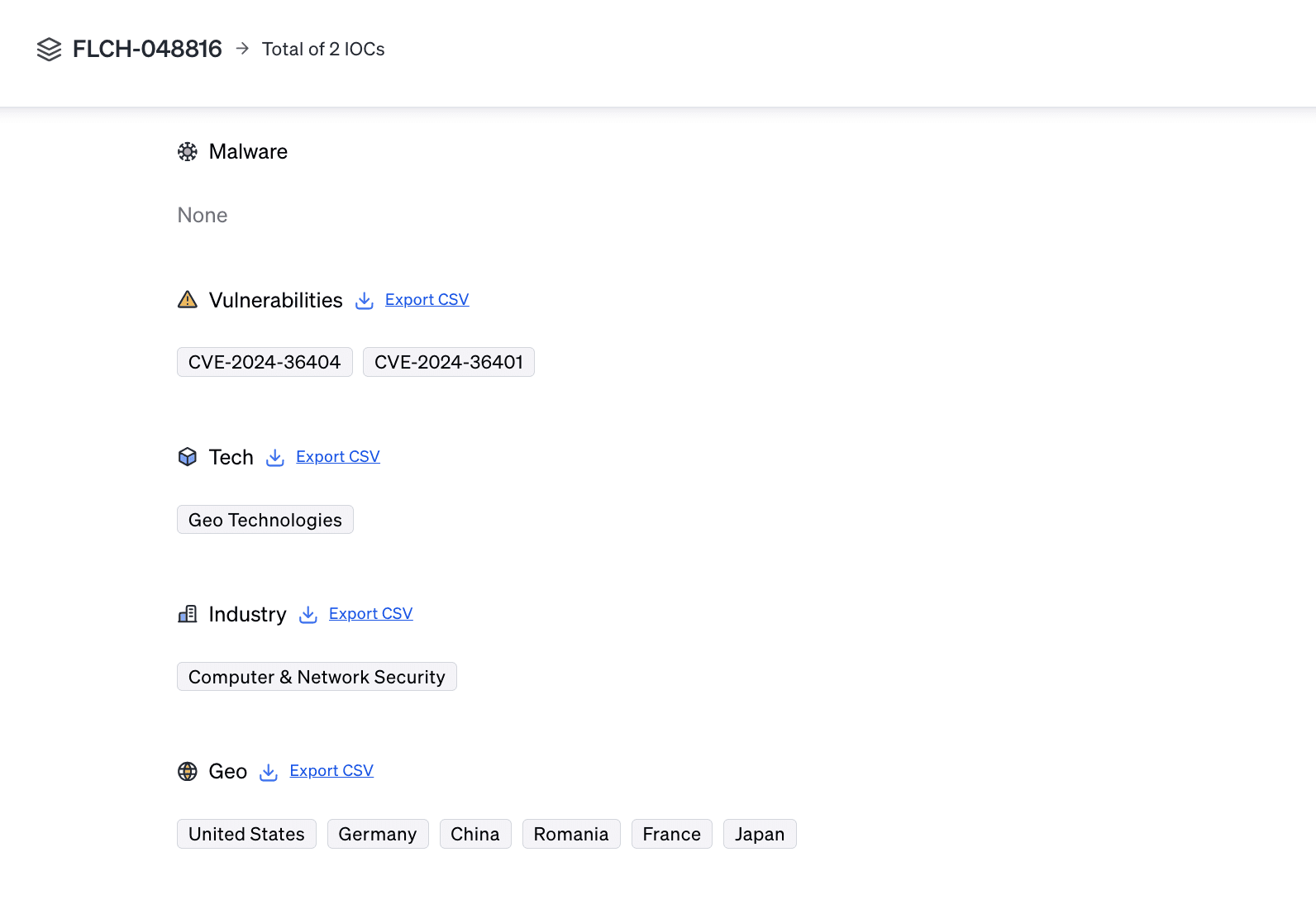
CVE-2024-36401 Victims & Motivations
The victims of this vulnerability are users of GeoServer, including government agencies, academic institutions, and private sector organizations that utilize geospatial data services. The vulnerability poses a global threat, with exploitation potentially leading to unauthorized remote code execution, data theft, or disruption of services. The motivations behind exploiting this vulnerability likely include unauthorized access and control over geospatial data and infrastructure.
CVE-2024-36401 Tactics
The methodology for exploiting this vulnerability involves sending malicious POST requests with specially crafted XPath expressions. Proof-of-concept exploits have demonstrated the potential to open reverse shells, make outbound connections, or create files on the server. These exploits highlight the severe risk posed by the vulnerability and the necessity for immediate mitigation measures.
Mitigation Advice
At the time of publication these were the right compliance controls to focus on for CVE-2024-36401:
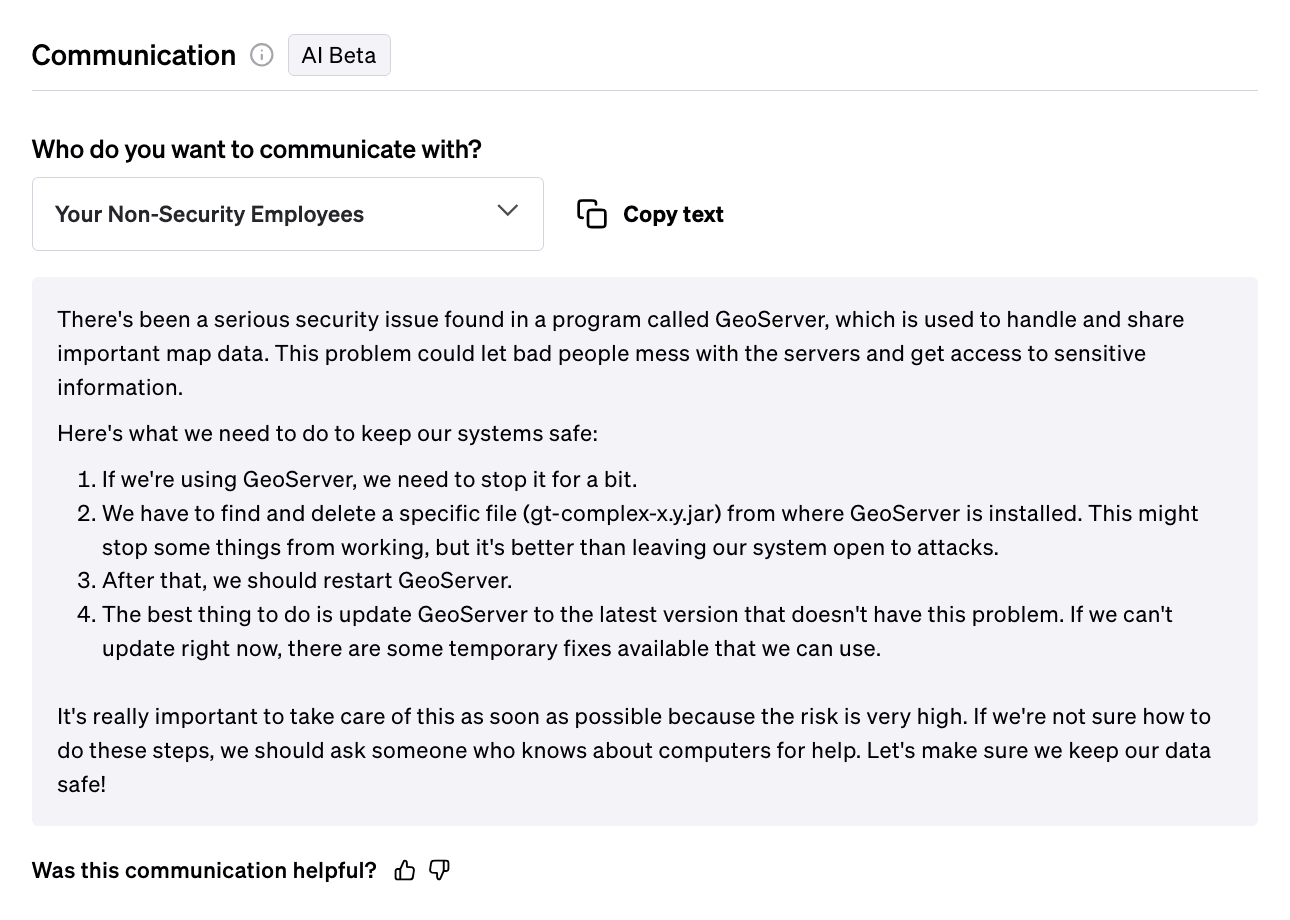
Patch Systems Immediately: Apply the official patches released for GeoServer and GeoTools without delay. Use the provided links to download the latest versions or security patches.
Immediately apply the workaround: For GeoServer .war deployment: Stop the application server. Unzip geoserver.war into a directory. Locate and remove WEB-INF/lib/gt-complex-x.y.jar. Rezip the directory into a new geoserver.war. Restart the application server. For GeoServer binary deployment: Stop Jetty. Locate and remove webapps/geoserver/WEB-INF/lib/gt-complex-x.y.jar. Restart Jetty.
Remove Vulnerable Code Temporarily: If immediate patching is not feasible, consider temporarily removing the gt-complex-x.y.jar file from GeoServer to mitigate the risk, keeping in mind this may affect GeoServer functionality.
You can check out the most recent mitigation measures when you create an account with Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees with exposure:
For Customers

For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The CVE-2024-36401 vulnerability in GeoServer is a critical threat due to its potential for unauthenticated remote code execution via unsafe XPath expression evaluations. Organizations using affected GeoServer versions must urgently upgrade to the latest versions or apply temporary mitigations, such as removing the vulnerable gt-complex-x.y.jar file, despite potential impacts on functionality. CISA has mandated that federal agencies patch this vulnerability by August 5, 2024, emphasizing the need for prompt action across all sectors to prevent exploitation and secure systems.
CVE-2024-36401 is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join Fletch and try it for yourself.

1. Sonic Wall [GeoServer RCE Vulnerability (CVE-2024-36401) Being Exploited In the Wild(https://blog.sonicwall.com/en-us/2024/07/geoserver-rce-vulnerability-cve-2024-36401-being-exploited-in-the-wild/)
2. SC Media [CISA: Urgent remediation of critical GeoServer flaw needed](https://www.scmagazine.com/brief/cisa-urgent-remediation-of-critical-geoserver-flaw-needed)
3. Infosecurity Magazine [CISA: Patch Critical GeoServer GeoTools Bug Now](https://www.infosecurity-magazine.com/news/cisa-patch-critical-geoserver/)

