Product

Kenisha Liu
Jul 24, 2023
One of the top responsibilities of any security team is threat exposure management. Keeping up with every new and evolving threat as they come out, and doing the manual labor to correlate it to your company is literally an impossible task today. Most companies end up never truly knowing their exposure because the work is too narrow and reactive. Or because they get bogged down with busy work.
When you’re in the business of threat exposure management you’re racing against the clock. It’s time to start living ahead of your threats with your data on Fletch.
Your data is at the core of how Fletch determines the threats that matter to your organization daily. We use 6 categories designed to give you the simplest glance you’ve ever had into your organization — one that takes you outside of the lines and beyond vulnerability and malware triage so you can finally get full coverage and understanding of your exposure.
Your data (and why do we need it)?
Your data enables you to quickly understand what’s changed, who’s where, and who’s using what technology.
The second you create a Fletch account, without connecting any data, you’ll get a comprehensive exposure report of your external tech and industry. The more data you connect, the richer the profile gets and the more threat visibility coverage you’ll have.
In just 10 minutes, you can connect your data so we can go to work for you daily (see how to get started)

How does it work
Fletch continuously captures, cleans, and classifies data so you know your latest potential exposure without having to do the data plumbing.
These include:
Technology. See the apps your people use to run your business, so you are never surprised by shadow apps again. Someone in marketing downloads an app that correlates with a major threat, you’ll know right away.
Industry. All of the verticals and sub-verticals that we’ve identified for your business. Easy to miss, but Fletch makes it cost effective and simple to live ahead of industry threats.
Geo. All of the regions your people are in right now. It’s hard to keep track of where everyone is and the threats that correlate to them. Never be surprised by geo threats that fly under your radar again.
Vulnerability scanners & malware tools. All the vulnerabilities and malware indicated by your scanner and/or EDR tool. Fletch helps you prioritize the plethora of alerts and gives you advice on how to mitigate the threats.
We look at your data in a holistic way to cover the holes in your company threats can enter from.
Each type of correlation gives you unique capabilities based on the information you’ll uncover. You can click into each type of correlation to get a breakdown of the # of tech, industries, locations, etc. in your organization. Or you can check to see if there are any threats that are targeting you based on that correlation.
If there are, we got you covered. Use our mitigation advice in your Threat Boards to remediate the threat and get ahead.

What's in it for me?
Let’s break down the exposure types and how you can utilize them efficiently:
What are the benefits to tech data?
Your tech is your ticket to understanding and organizing your technology infrastructure and the risks that come with it. Fletch’s AI engine will match your tech to Major Threats so you know what’s on the horizon.
With technology:
The IT team can see every application that people are logging into. Get visibility into your software supply chain, hardware, or app inventory for enhanced coverage of your tech data. With one click you can see exactly who is using what app and investigate suspicious activity quickly and efficiently.
Discover the apps you weren’t even aware of or “shadow IT”. According to Cisco, 80% of company employees use shadow IT because it is convenient. Fletch can help you purge shadow IT.
The CFO can see all the apps your business is spending money on. You can consolidate tech to operate leaner.
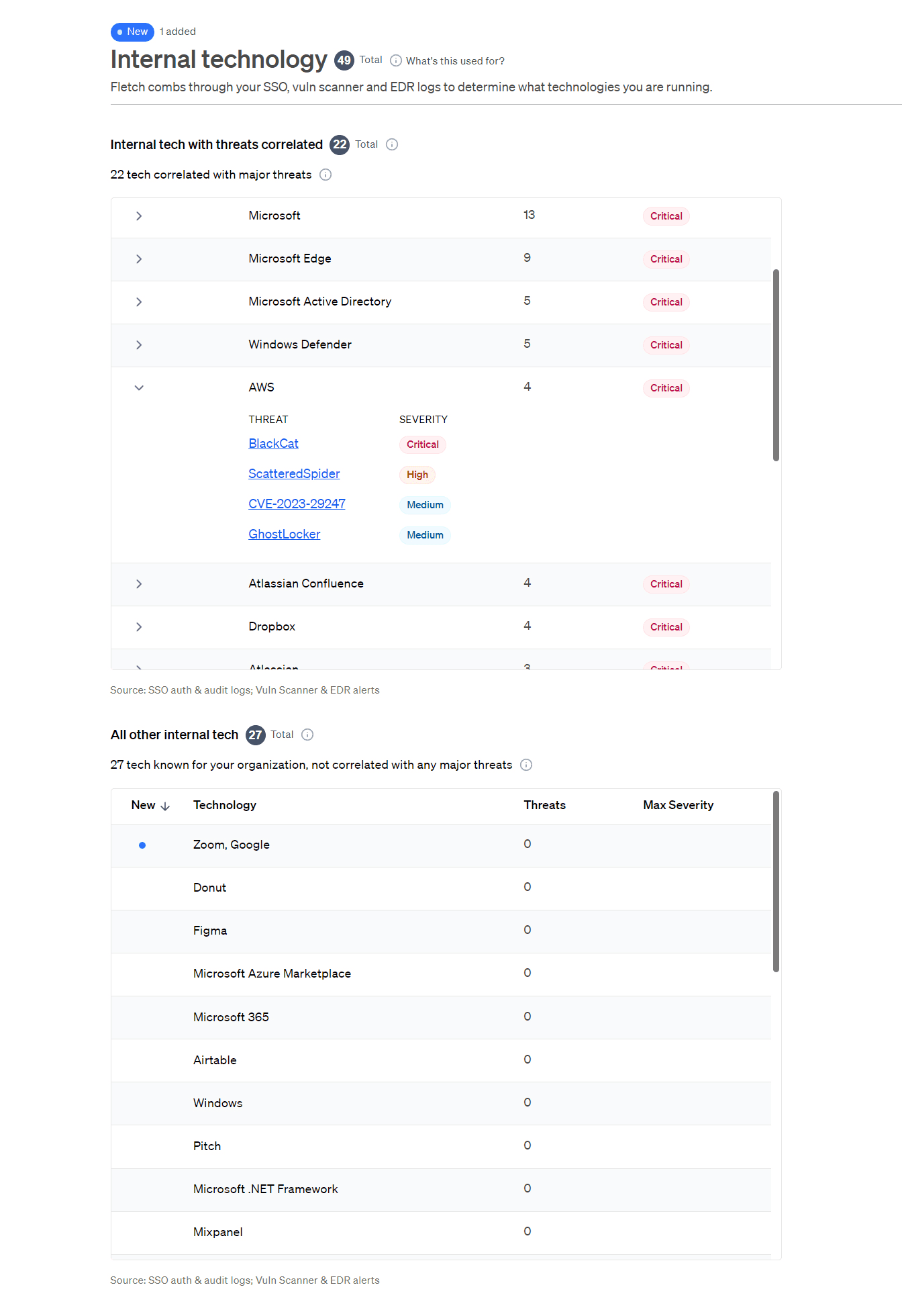
How to get it: Connect your SSO data to get your internal tech data. Your external tech data is pulled from public sources the second you sign up for a Fletch account, so you get instant value.
What are the benefits to industry?

Industry covers every threat targeting your sector or subsector.
Industry threats are often bad actors targeting your people with phishing campaigns and ransomware. They are easy to miss because they rarely show up in day-to-day vulnerability and malware alerting — especially when just emerging. Meaning you likely won’t know about them until there is an issue.
The most sophisticated teams spend exorbitant amounts of time and money on industry trade groups and specialized threat intel to get ahead of this problem
Fletch makes it simple and affordable for all to live ahead of industry threats the second you create your Fletch account
How to get it: We collected your industry information from public data sources meaning you’ll get access to this exposure instantly when you sign up for Fletch.
What are the benefits to geo?

Geo exposure gives you access to insights you never could before.
The world is increasingly remote. People are traveling and working wherever they go. An employee’s impromptu vacation to Mexico can make the whole company a target for threats that IT isn’t even aware of. As a security person, you never want to be surprised.
This is a type of exposure that gets overlooked because it is hard to do and oftentimes the threats don't directly correlate with your tech stack like traditional vulnerabilities and malware. However it's this kind of human behavior that leaves the most holes in your security strategy.
With geo, you’ll always have quick visibility to where your people are at any given moment and the threats that match their location. That way, you can protect your business even as a work-from-anywhere company. Just another way to stay ahead of threats.
How to get it: Fletch identifies the regions that you do business in or where your people are, based on your headquarters, Auth logs, and your SSO data.
What are the benefits to vulnerability scanner and malware?

This provides you a complete list of all your vulnerability and malware indicators that correlate with major threats.
We do the data plumbing work to tell you any resources that may be impacted by a given threat.
These tools often clog up your agenda with endless alerts that aren’t always relevant to you. We help you increase efficiency and prioritize effectively.
We comb through the countless alerts to show you what you need to focus on. And we extract detailed information on each threat so you can move quickly through your busy day.
How to get this: Connect your security technologies to Fletch to make the most out of your tools.
How to get started
You can get instant value when you sign up for Fletch. No data connection required. For an even richer exposure profile take as little as 10 minutes to connect your data sources. Here’s how:
Sign up for Fletch.
Set up your Fletch account
Add tech, industry and geo tags
Connect your productivity suite or SSO provider (Google Workspace, M365, or Okta) to start building your internal tech and geo visibility.
Note: Fletch just uses the metadata in your auth and audit logs. Not the sensitive information in your files. Token creation instructions for Google (~30 mins), Entra ID (3 mins), and Okta (~10 mins).Connect security products - you can connect your application vulnerability scanners, end point detection products, and code vulnerability scanners. Fletch will correlate threats with these data sources and provide you with advice on what to do and communication language you can use with your teams.
Note: The complete list of applications include Carbon Black, Crowdstrike, Microsoft Defender for Endpoint, Qualys, Sentinel One, Tenable, Snyk, GitHub.
Takeaway
Your data in Fletch will give you robust organizational details you don’t have access to today, so that you can live ahead of threats at the fraction of the work and cost. These are threats that are right around the corner that you might not have noticed until it's in the news or it’s too late. We’re just at the beginning, with new correlation types planned in the future.
Login to Fletch to see your data.


