Product

Finn Callaghan
Jul 5, 2024
Latest Headline
Progress Software has released critical patches for a severe authentication bypass vulnerability in its MOVEit managed file transfer solution, identified as CVE-2024-5806. This vulnerability affects the SFTP module and can potentially allow unauthorized access to sensitive data. With a CVSS score of 9.1, the flaw underscores the urgent need for users to update their systems to the latest versions to mitigate the risks.
Key Points:
First detected in June 2024
MOVEit Transfer vulnerabilities exploited by CI0p ransomware group
2 total IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out CI0p’s Threat Board for any updates or join Fletch to be in the know for every threat.
Cl0p Group Summary
The Cl0p ransomware group, also known as TA505, has been linked to exploiting CVE-2024-5806. Predominantly associated with Russian cyber actors, Cl0p is notorious for targeting file transfer solutions with ransomware. Their tactics involve bypassing authentication to gain unauthorized access, emphasizing the sophisticated nature of their attacks.
Severity: High
Maturity: Mainstream
IOCs: 0 Malware hashes and 2 vulnerabilities
Targets: 1 tech target, 1 industry target, and 10 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.

CI0p Victims & Motivations
The affected technologies primarily include the MOVEit Transfer SFTP module, widely used in enterprise environments for secure file transfers. CVE-2024-5806's impact is most notable in the US, UK, Germany, Canada, and the Netherlands, affecting various industries that rely on these file transfer solutions. The motivations behind exploiting this vulnerability include financial gain through data theft and ransomware, as well as espionage and disruption.
CI0p Tactics
Attackers exploit improper authentication mechanisms to gain unauthorized access, employing tools like Cl0p (Linux variant) ransomware. This method of attack demonstrates the critical need for robust cybersecurity measures and timely application of patches to defend against such threats.
Mitigation Advice
At the time of publication this was the mitigation advice against Cl0p:
Patch Immediately: Apply the patch (MOVEit Gateway 2024.0.1) released by Progress Software without delay to address the vulnerability.
At the time of publication, these were the right compliance controls to focus on for CI0p:
Remove the local Administrators group from the list of groups allowed to log in through RDP.
Require employees to use a username and password along with a physical smart card or token generator to access the system.
Limit the permissions of remote users accessing the system.
Limit the access to your company's network resources.
Limit the accounts that can use remote services and restrict their permissions.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
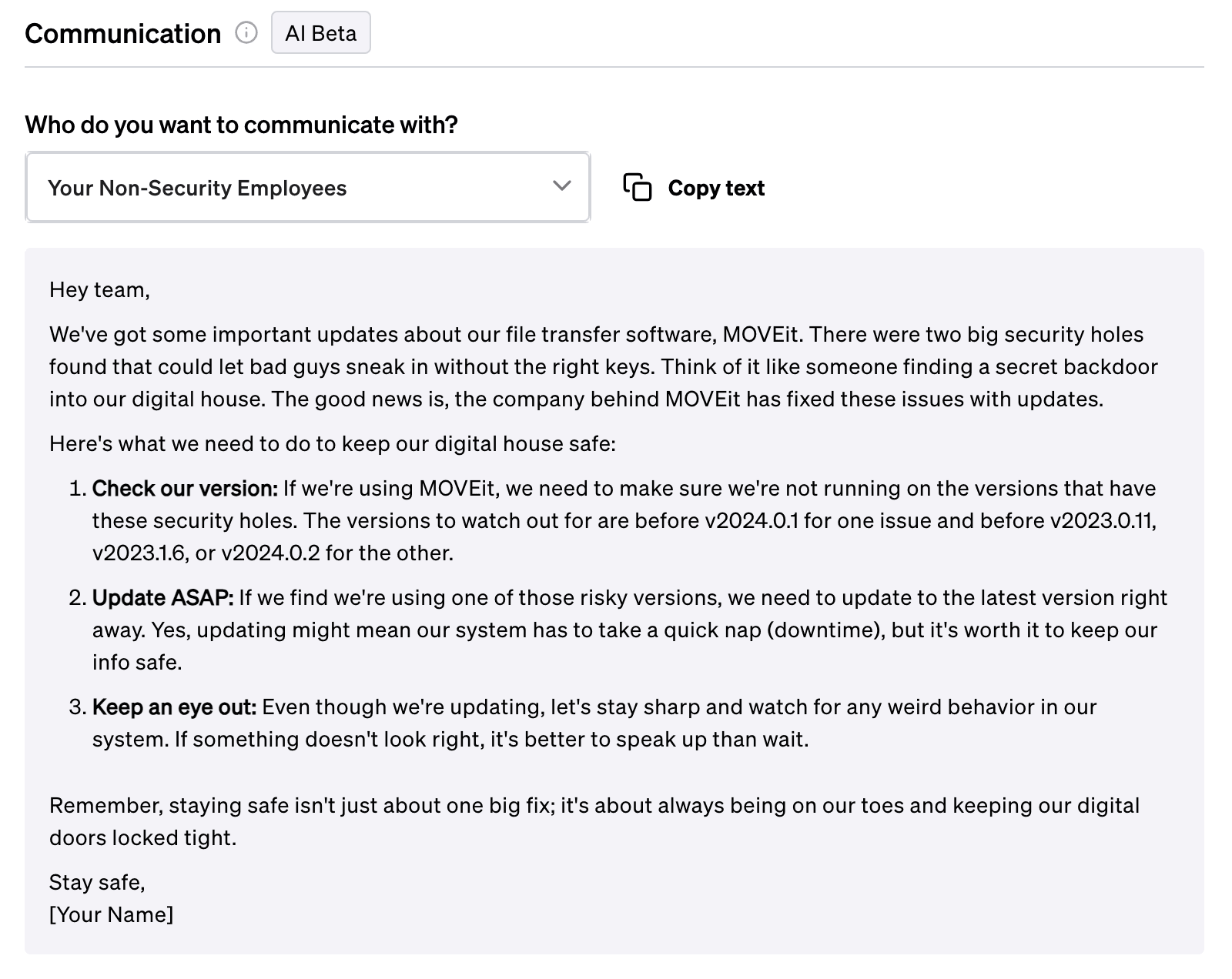
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:
For customers:

For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The MOVEit Transfer vulnerability CVE-2024-5806 highlights the importance of prompt security updates and robust cybersecurity strategies. Organizations using affected versions should update their systems immediately and implement additional mitigation measures, such as restricting RDP access and monitoring for indicators of compromise (IOCs). This proactive approach is essential to protect against the significant risks posed by this vulnerability.
CI0p is just one example of an ever-evolving threat that Fletch helps you keep track of and prioritize.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join the Fletch waitlist and try it for yourself.

1. Heimdal [New MOVEit Transfer Critical Vulnerability Targeted by Threat Actors] (https://heimdalsecurity.com/blog/moveit-transfer-critical-vulnerability)
2. Global Security Mag [New 2024 MOVEit Transfer Vulnerability: What We Know So Far] (https://www.globalsecuritymag.fr/new-2024-moveit-transfer-vulnerability-what-we-know-so-far.html)
3. Esentire [Securing Passkeys: Thwarting Authentication Method Redaction Attacks] (https://www.esentire.com/blog/securing-passkeys-thwarting-authentication-method-redaction-attacks)

