Product

Finn Callaghan
Jul 12, 2024
Latest Headline
A critical vulnerability named "BlastRADIUS" (CVE-2024-3596) has been discovered in the RADIUS protocol, which has been a cornerstone of network authentication since the 1990s. Rated with a CVSS score of 9, this vulnerability exploits a protocol flaw and an MD5 collision attack, enabling attackers to manipulate server responses and gain administrative privileges on RADIUS devices without needing to brute force or steal credentials. The vulnerability primarily affects RADIUS/UDP implementations using non-EAP authentication methods.
Key Points:
First emerged in July 2024
Impacts systems using non-EAP RADIUS over UDP
1 total IOC as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up-to-date as of publication. Check out BlastRADIUS’s Threat Board for any updates or join Fletch to be in the know for every threat.
BlastRADIUS Summary
A vulnerability in the RADIUS protocol, which has been widely used since 1991 for network authentication, has been identified due to its reliance on outdated encryption techniques. BlastRADIUS could allow hackers to execute a man-in-the-middle attack by sending an approval signal following a denied authentication request, exploiting MD5 collision weaknesses.
Severity: Critical
Maturity: Mainstream
IOCs: 0 Malware hashes and 1 vulnerability
Targets: 9 tech targets, 1 industry target, and 4 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.
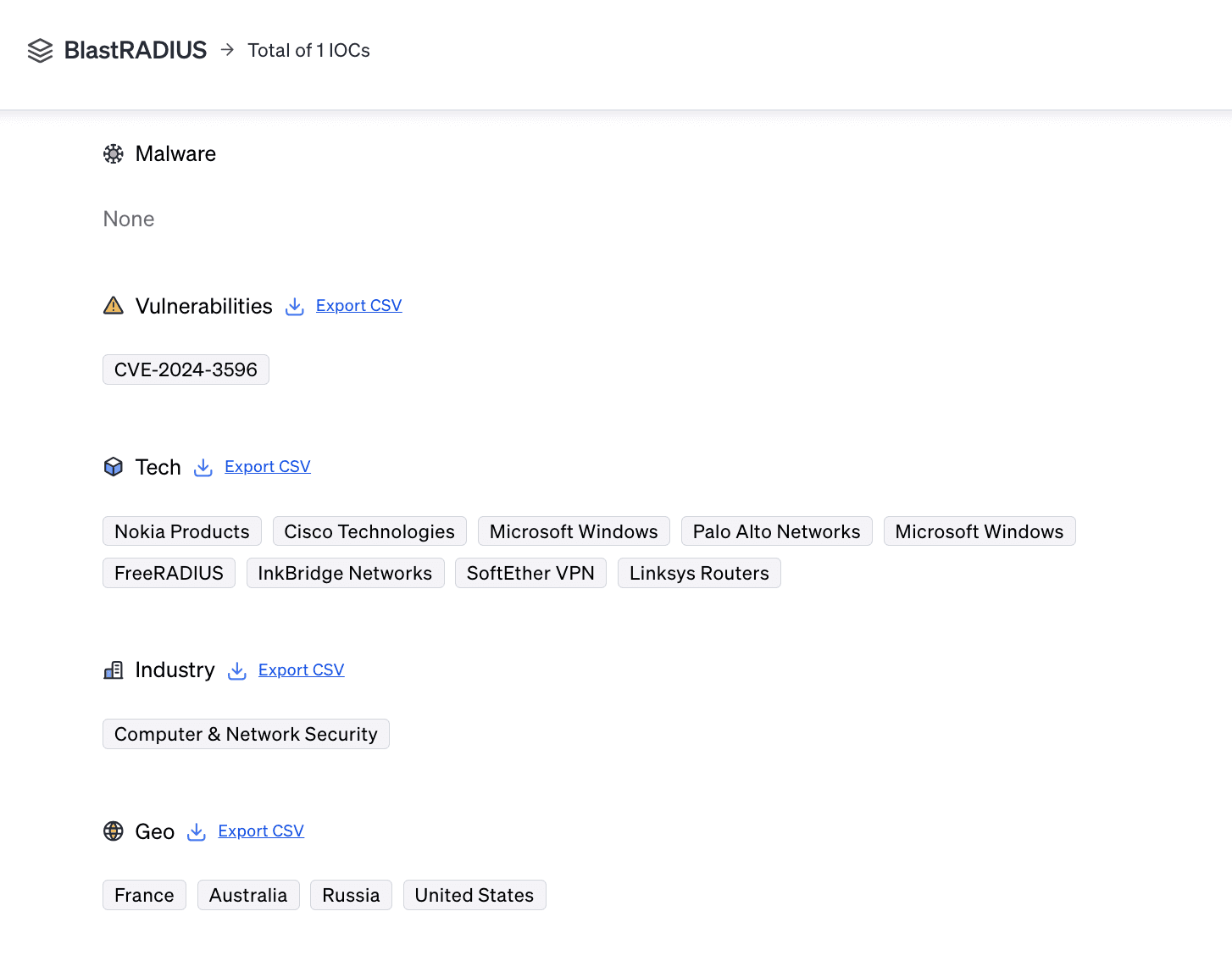
BlastRADIUS Victims & Motivations
The BlastRADIUS vulnerability affects a wide range of technologies and industries that use RADIUS for network authentication, including corporate networks, ISPs, and telecom providers. Given its global reach, organizations worldwide are potentially at risk.
The motivations behind exploiting this vulnerability include gaining administrative access to critical network infrastructure for purposes such as data theft, espionage, or further malicious activities.
BlastRADIUS Tactics
Attackers exploit MD5 collision vulnerabilities and protocol flaws in RADIUS. Utilizing Man-in-the-Middle (MiTM) techniques and custom tools, they can automate the exploitation process, making it easier to manipulate server responses and gain unauthorized access.
Mitigation Advice
At the time of publication, this was the mitigation advice against BlastRADIUS:
Temporarily disable vulnerable authentication methods such as PAP, CHAP, and MS-CHAPv2 until the vulnerability is addressed.
Run the provided detection script to identify if your RADIUS servers are vulnerable to MD5 collision attacks.
Immediately patch systems affected by CVE-2024-3596 if a patch is available from the vendor.
At the time of publication, these were the right compliance controls to focus on for BlastRADIUS:
Make sure all important information is kept safe at rest and in motion by using strong encryption.
Restrict access to network resources and infrastructure to prevent unauthorized traffic manipulation.
Train employees to be cautious of certificate errors when browsing the internet.
Separate your network into smaller sections to limit access between them.
Install a network intrusion prevention system to block suspicious traffic.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees with exposure:

For Customers:
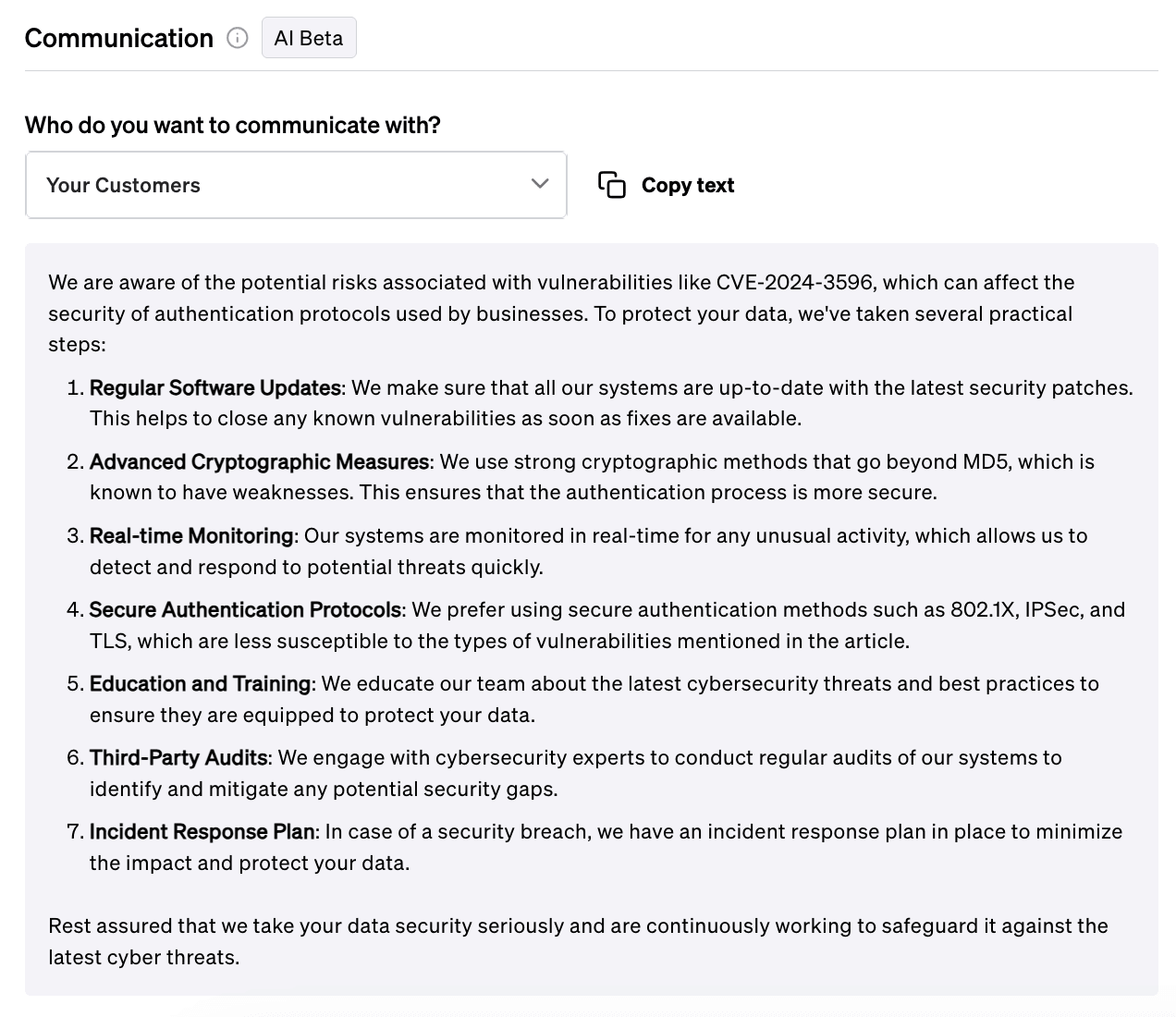
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The discovery of the BlastRADIUS vulnerability underscores the critical importance of updating cryptographic methods in network protocols. The extensive use of RADIUS for network authentication means that this vulnerability could have far-reaching consequences. Therefore, it is crucial for organizations to promptly adopt the recommended mitigations to protect their network infrastructure.
BlastRADIUS is just one example of an ever-evolving threat that Fletch helps you track and prioritize.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join the Fletch waitlist and try it for yourself.

1. Tenable Blog [Sealing Off Your Cloud’s Blast Radius] (https://www.tenable.com/blog/sealing-off-your-clouds-BlastRADIUS)
2. Threatpost [Reducing BlastRADIUS Cyberattacks] (https://threatpost.com/reducing-BlastRADIUS-cyberattacks/177412/)
3. DeployHub [Security Vulnerability Assessment for the Software Supply Chain] (https://www.deployhub.com/security-vulnerability-assessment/)
4. TrendMicro [Leveraging Data Science to Minimize BlastRADIUS Ransomware Attacks] (https://www.trendmicro.com/en_us/research/2023/leveraging-data-science-minimize-BlastRADIUS-ransomware-attacks.html)
5. Entitle [What is BlastRADIUS] (https://www.entitle.io/blog/what-is-BlastRADIUS)

