Product

Jake Trujilo
May 22, 2024
Latest Headline
Since its identification in April 2022, Black Basta has established itself as a formidable threat, impacting over 500 organizations globally, including critical infrastructure sectors such as healthcare, defense, and technology. Black Basta has been linked to significant financial damages and operational disruptions.
Key Points:
First identified in April 2022
Suspected to have originated from the now defunct Conti ransomware group
Suspected to have ties to the FIN7 cybercriminal group
11579 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Black Basta’s Threat Board for any updates or join Fletch to be in the know for every threat.
Black Basta Summary
Operating under a Ransomware-as-a-Service (RaaS) model, Black Basta is known for its rapid spread and sophisticated attack techniques. Black Basta primarily targets critical infrastructure sectors, including healthcare, defense, and technology, across the U.S., Canada, Japan, U.K., Australia, and New Zealand.
Despite speculation that Black Basta originates from the Conti ransomware group, no direct code overlap has been found. Black Basta is believed to currently be associated with the FIN7 group. Black Basta is likely linked to Eastern European cybercriminal organizations and their RaaS model indicates a structured and well-resourced operation.
Severity: Critical
Maturity: Mainstream
IOCs: 11569 Malware hashes and 10 vulnerabilities
Targets: 12 tech targets, 8 industry targets, and 34 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.

Black Basta Victims & Motivations
Black Basta targets technologies such as VMware ESXi virtual machines, Windows, and Linux systems. It has significantly impacted industries including public health, defense, and technology. Recent advisories from CISA, the FBI, and Health-ISAC emphasize that Black Basta is especially targeting the healthcare sector. Geographically, it has primarily affected organizations in the U.S., Canada, Japan, U.K., Australia, and New Zealand.
The main motivation behind their attacks is financial gain through ransom payments, but the disruption of critical services and data theft are also significant drivers. By November 2023, Black Basta had extorted at least $100 million from over 90 victims.
Notable victims of Black Basta include Rheinmetall, a German defense company, ABB, a Swiss robotics company, and Capita, a British technology outsourcing firm. These advisories highlight the urgency for healthcare organizations to implement recommended cybersecurity measures to prevent disruptions and data breaches.
Black Basta Tactics
Black Basta employs a variety of methodologies for its attacks. Initial access is often gained through spear-phishing campaigns or the use of QakBot malware. Additional tools and techniques include network scanning, remote access tools, and advanced encryption schemes using ChaCha20 and RSA-4096.
Black Basta exploits multiple vulnerabilities, including CVE-2024-1709 and CVE-2020-1472, and uses tools for lateral movement and privilege escalation. They employ double extortion tactics, encrypting and exfiltrating data before demanding a ransom.
Mitigation Advice
At the time of publication this was the mitigation advice against Black Basta:
Short-Term:
Implement strict access controls and require verification before granting any remote access to systems.
Disable or uninstall Quick Assist and other remote assistance tools if they are not necessary for business operations.
Perform a comprehensive security audit to identify and remediate potential vulnerabilities that could be exploited by ransomware.
Review and update incident response and disaster recovery plans to include scenarios specific to ransomware attacks.
Implement Network Segmentation: Isolate critical systems and data from the rest of the network to limit the spread of ransomware.
Long-Term:
Make sure all local administrator accounts have different, complex passwords.
Change default usernames and passwords after installation, and avoid reusing passwords between different accounts.
Limit who can access important folders on your computer, like C:\Windows\System32.
Limit the number of administrator accounts and only give access to necessary individuals.
Set proper permissions on files and directories to prevent unauthorized changes to the system firewall.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:

For Customers:
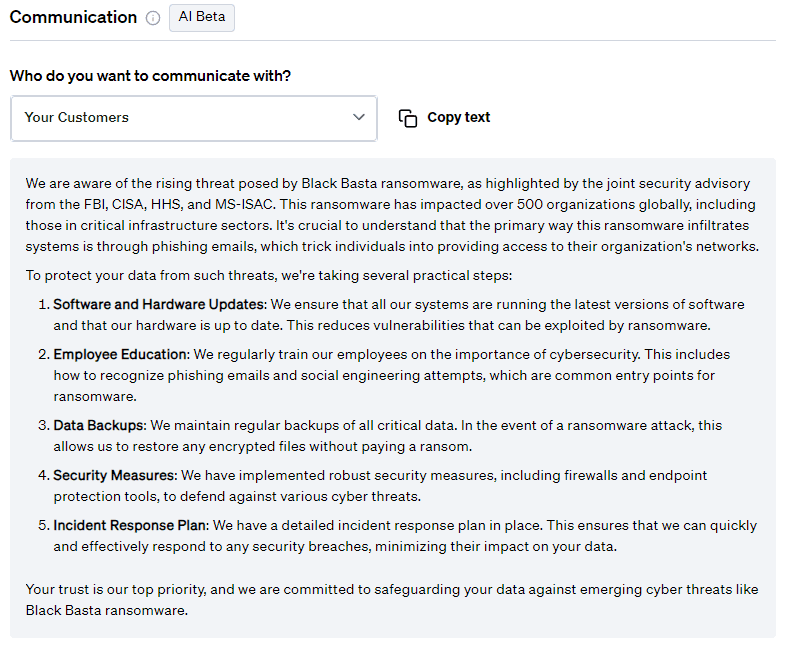
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
Black Basta poses a significant threat to global cybersecurity, particularly for critical infrastructure. Its sophisticated tactics, including double extortion and the use of advanced malware, underline the need for robust cybersecurity measures.
Organizations must prioritize updates, enforce multi-factor authentication, secure remote access, and maintain regular backups to mitigate the risk. Enhanced threat detection and response strategies are crucial in defending against such persistent and evolving threats.
Black Basta is just one example of an ever evolving threat that requires in-depth cyber intelligence to stay on top of. Fletch helps you keep track of, and prioritizes, them all.
As the de facto record on the threat landscape, our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, detect threats to your tech and people early, or simply to become an instant expert on any threat at any time.
Join Fletch and try it for yourself.

1. CISA [CISA Advisory on Black Basta](https://www.cisa.gov/news-events/cybersecurity-advisories/cisa-and-partners-release-advisory-black-basta-ransomware)
2. AttackIQ [Response to CISA Advisory (AA24-131A): #StopRansomware: Black Basta](https://www.attackiq.com/2024/05/17/response-to-cisa-advisory-aa24-131a/)
3. American Hospital Association [AHA Bulletin on Black Basta](https://www.aha.org/news/headline/2024-05-10-agencies-issue-advisory-ransomware-group-accelerates-attacks-health-care)
4. HivePro [Black Basta Ransomware Impacts Over 500 Organizations Worldwide](https://www.hivepro.com/threat-advisory/black-basta-ransomware-impacts-over-500-organizations-worldwide/)

