Product

Jake Trujillo
Jun 12, 2024
Latest Headline
As of early 2024, the Akira ransomware group has been responsible for data breaches affecting over 250 organizations globally, amassing approximately $42 million in ransom payments. Recent high-profile breaches include Excel Security Corp, DreamWall, Faultless Brands, and MagicLand, underscoring the ongoing threat posed by Akira to various sectors.
Key Points:
Emerged in March 2023
Initially targeted Windows systems, added a Linux variant by June 2023, and a Rust-based variant by August 2023
95 IOCs as of publication
Fletch is constantly monitoring the threat landscape. The data in this guide is most up to date as of publication. Check out Akira’s Threat Board for any updates or join Fletch to be in the know for every threat.
Akira Summary
Akira is linked to the now-defunct Conti ransomware group, sharing significant code similarities. The operational tactics suggest links to Eastern European cybercriminal groups, although no specific country has been attributed. The group operates under a Ransomware-as-a-Service (RaaS) model and uses double extortion tactics, demanding ransom for both decryption of files and non-disclosure of stolen data.
Severity: Medium
Maturity: Mainstream
IOCs: 88 Malware hashes and 7 vulnerabilities
Targets: 14 tech targets, 3 industry targets, and 21 geo targets
Learn more about Fletch’s metrics in the Fletch Help Center.

Akira Victims & Motivations
Akira primarily targets small and medium-sized enterprises (SMEs) but has also affected critical infrastructure, from critical infrastructure to healthcare, finance, and education. Geographic regions impacted include North America, Europe, and Australia.
The primary motivation for Akira's attacks is financial gain, achieved through ransom payments. The ransomware targets both Windows systems and VMware ESXi virtual machines, leveraging known vulnerabilities to gain initial access and spread within networks.
Akira Tactics
Akira employs sophisticated methods to infiltrate networks, including exploiting VPN vulnerabilities, particularly those lacking multi-factor authentication (MFA), as well as using compromised credentials, spear-phishing, and remote code execution vulnerabilities such as CVE-2021-21972 and CVE-2023-20269.
The group maintains persistence by creating new domain accounts and conducts thorough reconnaissance with network scanning tools. Data exfiltration is performed using tools like FileZilla and WinSCP, while encryption methods combine ChaCha20 and RSA algorithms to secure the compromised data.
Migration Advice
At the time of publication this was the mitigation advice against Akira:
Verify the integrity of backup solutions and ensure they are not using legacy or unsupported versions.
Create backups of important data and store at least one copy outside the network.
Review and update access controls, ensuring that the principle of least privilege is applied.
At the time of publication these were the right compliance controls to focus on for Akira:
Make sure to connect your security data to your Fletch workspace, so that Fletch is able to correlate and prioritize threats like this effectively in the future.
Create strong and unique passwords for all local administrator accounts.
Create strong, unique passwords for all local administrator accounts on the network.
Enable pass the hash mitigations to apply User Account Control restrictions to local accounts on network logon.
Regularly update all software on company devices; make sure all auto-update mechanisms are enabled and working correctly.
You can check out the most recent mitigation measures by creating an account when you join Fletch.
Communication
On top of mitigation advice, Fletch also provides Beta AI generated communications so you can educate your different company stakeholders. At the time of publication, this was what was recommended for the following:
For employees:

For customers:
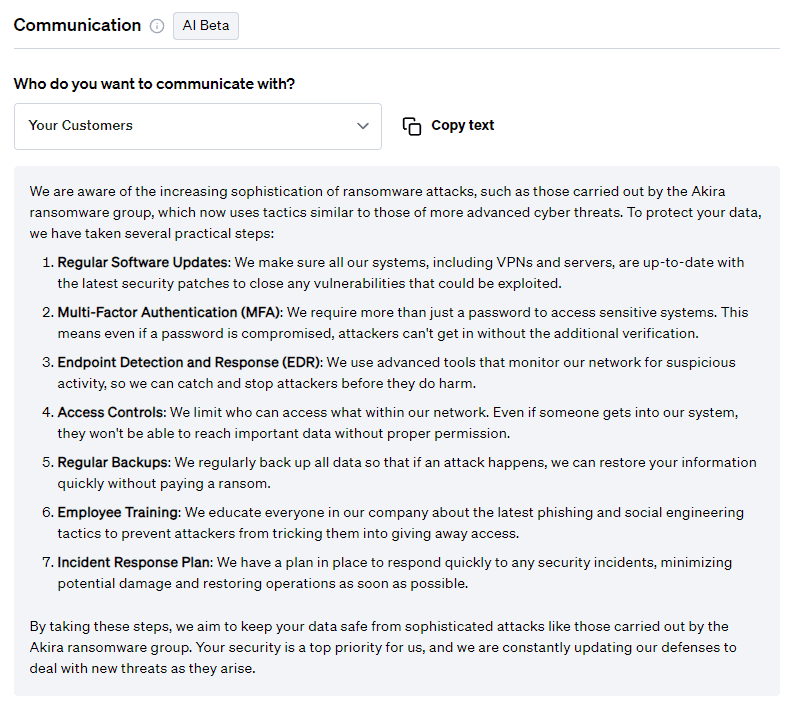
For more templates for your different stakeholders, create a workspace when you join Fletch.
Takeaway
The Akira ransomware represents a significant and evolving threat to various industries and regions. Organizations must enhance their cybersecurity measures to mitigate the risk of such advanced ransomware attacks. This includes prioritizing robust patch management, enforcing multi-factor authentication, and conducting comprehensive security assessments.
Akira is just one example of an ever evolving threat that Fletch helps you keep track of, and prioritizes.
Our AI engine is constantly scanning and indexing the threat landscape for you so you can plug the gaps in your security. You can use Fletch to prioritize your alerts, forecast threats on your horizon, and give you daily advice on what to do.
Join the Fletch waitlist and try it for yourself.


