
Proactive cyber threat AI
Proactive cyber threat AI
Proactive cyber threat AI
Prioritize
Prioritize
your daily cybersecurity work
your daily cybersecurity work with the world's first
with the world's first
Cyber Threat AI
Cyber Threat AI
95% of your team's time is wasted working on non-priority work. Fletch generates your short list of what to prioritize daily. And, best of all, it fits right into your existing workflows.
Sign up for the waitlist
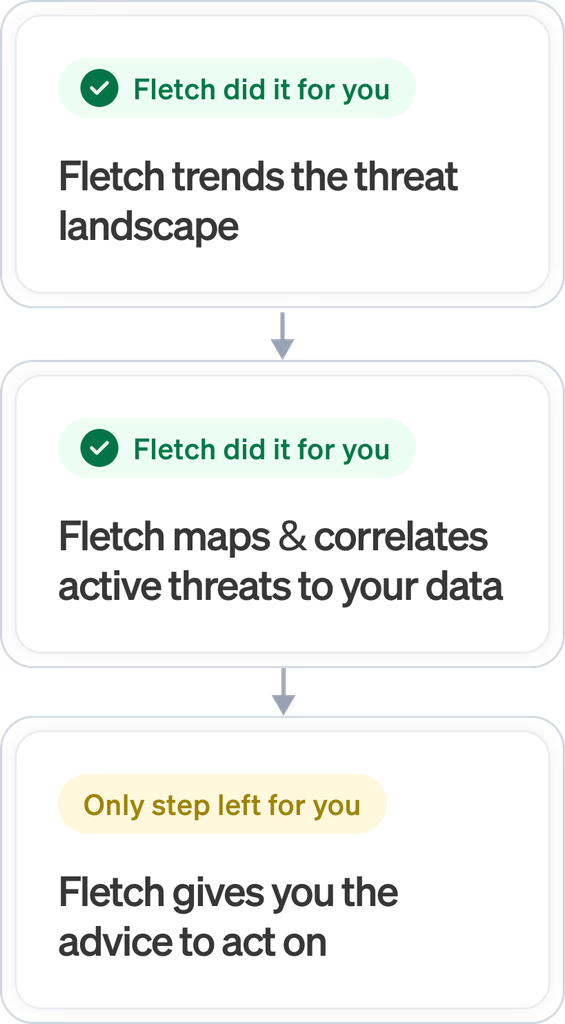
Fletch's Trending Engine
Trends the threat landscape
Fletch's Correlation Engine
Maps and correlates active threats to your data
Fletch's Advisor Engine
Act on the advice Fletch gives you
Fletch's Trending Engine
Trends the threat landscape
Fletch's Correlation Engine
Maps and correlates active threats to your data
Fletch's Advisor Engine
Act on the advice Fletch gives you
Fletch's Trending Engine
Trends the threat landscape
Fletch's Correlation Engine
Maps and correlates active threats to your data
Fletch's Advisor Engine
Act on the advice Fletch gives you
Your specialized cyber threat AI
Proactive cyber threat AI
Trends threats, providing info anchored to vetted cybersecurity sources as news breaks
Correlates your data with the latest threats
Generates actionable advice on how to defend, remediate, and mitigate
Checks multiple security compliance boxes - most importantly threat intel
Sign up for the waitlist
Generic wiki definitions
Out of date info on some threats without vetting, and most asks just trigger best practice lists
Doesn’t know anything about you or your data
Requires heavy prompting to get basic advice and refuses to answer if it mistakes you for a hacker
Doesn't check any security compliance boxes






Fletch's Trending Engine
Anyone can tell you what’s exploitable.
Only Fletch can tell you what’s most likely to be exploited right now.
Anyone can tell you what’s exploitable.
Only Fletch can tell you what’s most likely to be exploited right now.
Fletch trends and tracks the cyber threat landscape
Fletch trends and tracks the cyber threat landscape
Fletch trends and tracks the cyber threat landscape
Know what’s active now. If you don’t know about it right away, the damage is done.
Know what’s active now. If you don’t know about it right away, the damage is done.
Know what’s active now. If you don’t know about it right away, the damage is done.
Be 3-5 days ahead of legacy threat intel
Be 3-5 days ahead of legacy threat intel
Jump on the 7 day attack window (most threats go inactive after 7 days)
Jump on the 7 day attack window (most threats go inactive after 7 days)
50% of threats evolve
50% of threats evolve
50% of threats evolve.
*data shown was last updated 22nd January 2025
*data shown was last updated 13/1/2025
*data shown was last updated 22nd January 2025
re-emerged
PLAY
re-emerged
RedCurl
inactive
FARGO
active
Flaxtyphoon
inactive
CrowdStroke
re-emerged
NonEuclid
active
SafePay
active
Codefinger
re-emerged
BansheeStealer
inactive
CVE-2024-3094
active
Skuld
re-emerged
APT10
inactive
CVE-2024-36401
active
Firescam
active
HellCat
re-emerged
SafePay
active
ArmyPlus
inactive
Cl0p
re-emerged
Kimsuky
inactive
BlastRADIUS
active
SwaetRAT
Fletch trends and tracks the cyber threat landscape
Fletch trends and tracks the cyber threat landscape
Know what’s active now. If you don’t know about it right away, the damage is done.
Be 3-5 days ahead of legacy threat intel
Jump on the 7 day attack window (most threats go inactive after 7 days)
50% of threats evolve
Fletch's Correlation Engine
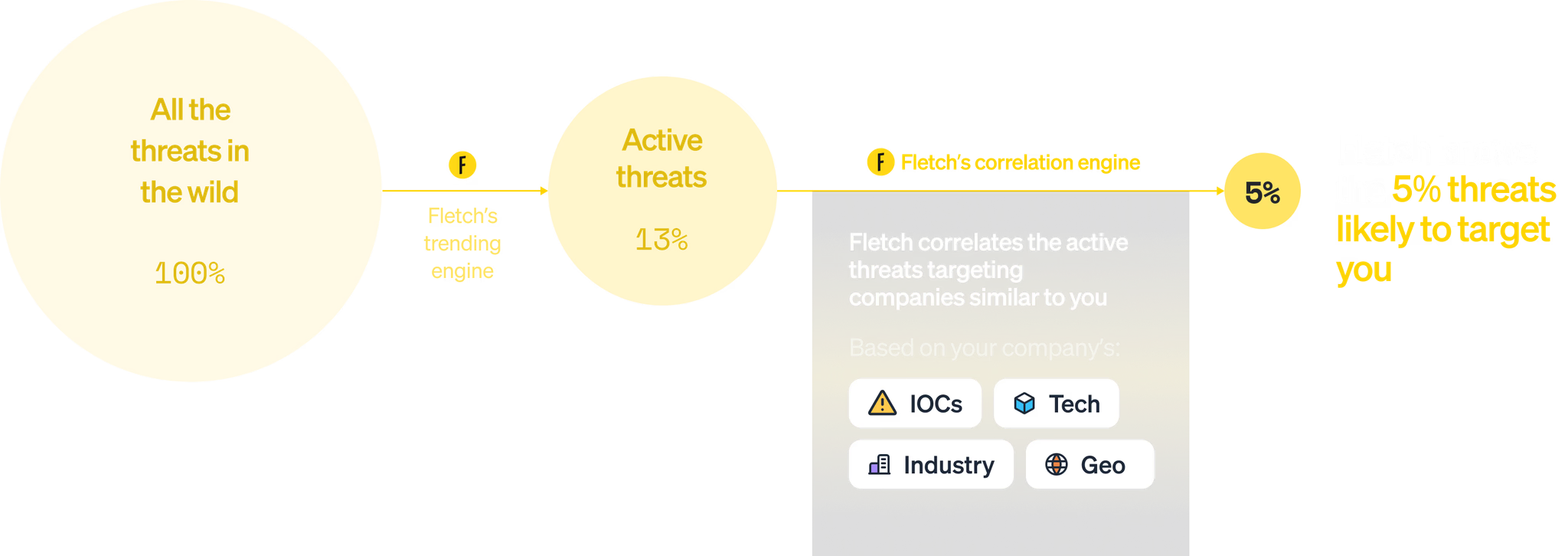
Only 5% of threats are likely to impact you right now. The question is: which 5%?
Fletch knows.
*Source: Fletch 2024 Report


Fletch's Advisor Engine
Reduce the busy work.
Focus on the critical.
Reduce the busy work.
Focus on the critical.
Give me a list of the threats most likely to impact me
Fletch generates a list of threats impacting companies that are similar to you, so you aren't next.

Give me a list of the threats most likely to impact me
Fletch generates a list of threats impacting companies that are similar to you, so you aren't next.

Give me a list of the threats most likely to impact me
Fletch generates a list of threats impacting companies that are similar to you, so you aren't next.

Give me a list of the threats most likely to impact me
Fletch generates a list of threats impacting companies that are similar to you, so you aren't next.

Give me a list of priority alerts
Fletch correlates your alerts with it's threat landscape trends to give you your short list

Give me a list of priority alerts
Fletch correlates your alerts with it's threat landscape trends to give you your short list

Give me a list of priority alerts
Fletch correlates your alerts with it's threat landscape trends to give you your short list

Give me a list of priority alerts
Fletch correlates your alerts with it's threat landscape trends to give you your short list

And so much more….

Generate a list of to-dos for me
Fletch generates a personalized to-do list of active threats correlated to your data.

Generate a list of to-dos for me
Fletch generates a personalized to-do list of active threats correlated to your data.

Generate a list of to-dos for me
Fletch generates a personalized to-do list of active threats correlated to your data.

Generate a list of to-dos for me
Fletch generates a personalized to-do list of active threats correlated to your data.
Give me advice to tackle threats
Fletch generates personalized advice for you to act on.

Give me advice to tackle threats
Fletch generates personalized advice for you to act on.

Give me advice to tackle threats
Fletch generates personalized advice for you to act on.

Give me advice to tackle threats
Fletch generates personalized advice for you to act on.

Send me an email every day
Fletch generates your personalized daily threat report.

Send me an email every day
Fletch generates your personalized daily threat report.

Send me an email every day
Fletch generates your personalized daily threat report.

Send me an email every day
Fletch generates your personalized daily threat report.

Give me details on a threat
Fletch generates a detailed analysis and summary on each threat.

Give me details on a threat
Fletch generates a detailed analysis and summary on each threat.

Give me details on a threat
Fletch generates a detailed analysis and summary on each threat.

Give me details on a threat
Fletch generates a detailed analysis and summary on each threat.

Tell me how a threat impacts me
Fletch highlights exactly how a threat is impacting, or will likely impact you.

Tell me how a threat impacts me
Fletch highlights exactly how a threat is impacting, or will likely impact you.

Tell me how a threat impacts me
Fletch highlights exactly how a threat is impacting, or will likely impact you.

Tell me how a threat impacts me
Fletch highlights exactly how a threat is impacting, or will likely impact you.

Generate communication for my leadership
Fletch generates tailored communications.

Generate communication for Leadership
Fletch generates tailored communications.

Generate communication for my leadership
Fletch generates tailored communications.

Generate communication for my leadership
Fletch generates tailored communications.

Easily add Fletch to your workflows
Easily add Fletch to your workflows
No new UI. Minutes to setup. Countless hours saved daily.
No new UI. Minutes to setup. Countless hours saved daily.
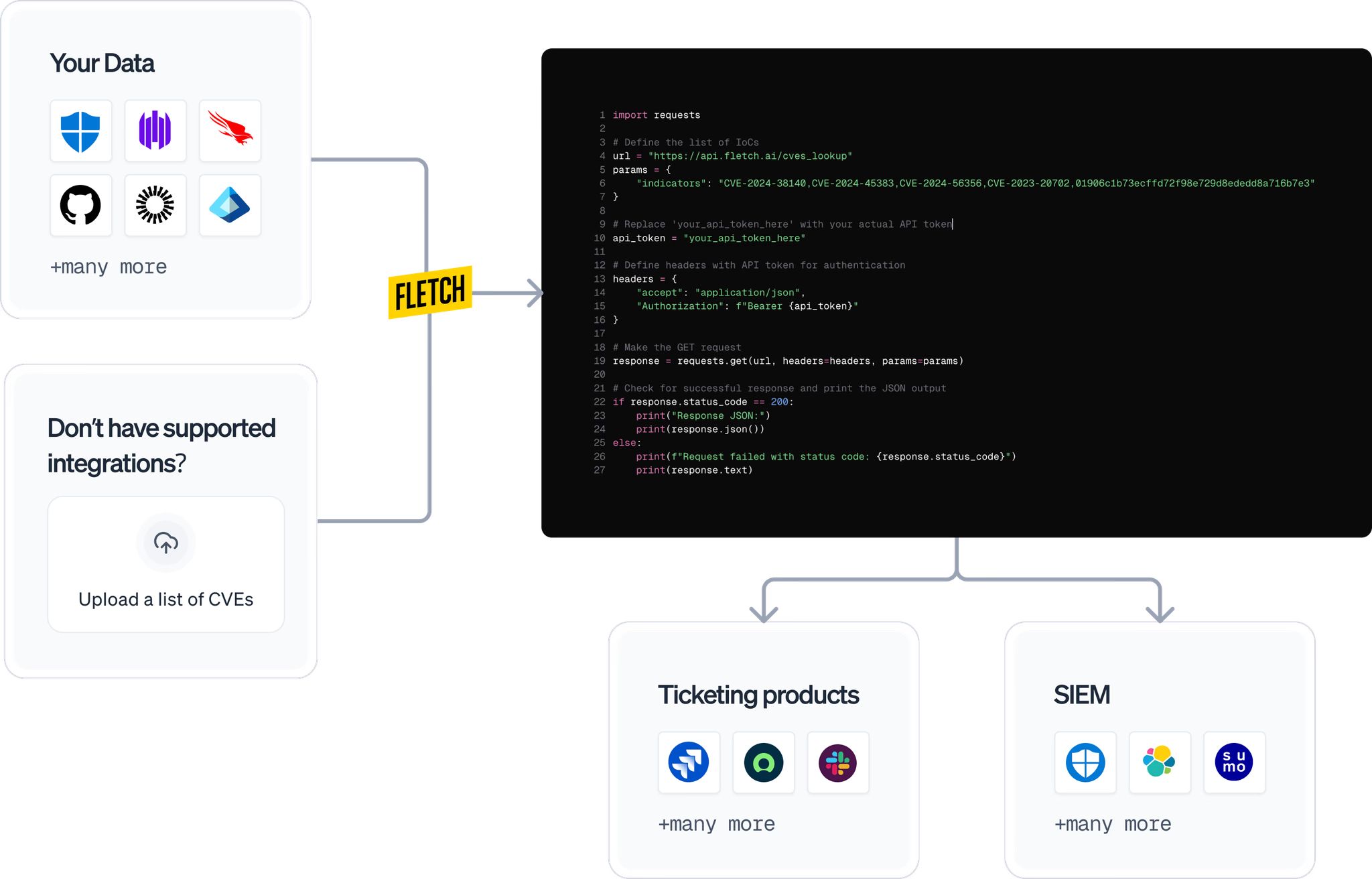




Easily add Fletch to your workflows
No new UI. Minutes to setup. Countless hours saved daily.



What our customers are saying...
What our customers are saying...
What our customers are saying...
David Johnston
Director of Information Technology at Mendocino College
Fletch has saved me time because I’m looking at stuff that actually matters. The reality is, I wouldn’t have spent enough of the time that I probably needed to spend before, just because it wasn’t doable.
Kevin Kanji
Chief Security Officer at Xplor
Threat intelligence is a fire hose of information. And it's some poor person's job to try to filter it. It's a waste of time. Fletch is the first I've seen to provide threats in context in a way that makes sense.
Kory Chan
Senior System Administrator at Evergreen Investment Advisors
We switched to Fletch from Lumen. In Fletch, it’s simple to get insights, and the threat boards are really good! The fact that we can integrate with Tenable and CrowdStrike is a plus, we’re always looking to pair down the number of tools.
Eric Quinn
CIO at C&S Companies
I love the advice in Fletch - more comprehensive and it’s things you can actually do, plus it’s very easy to find in the interface.
Your specialized cyber threat AI
Proactive cyber threat AI
Trends threats, providing info anchored to vetted cybersecurity sources as news breaks
Correlates your data with the latest threats
Generates actionable advice on how to defend, remediate, and mitigate
Checks multiple security compliance boxes - most importantly threat intel
Sign up for the waitlist
Generic wiki definitions
Out of date info on some threats without vetting, and most asks just trigger best practice lists
Doesn’t know anything about you or your data
Requires heavy prompting to get basic advice and refuses to answer if it mistakes you for a hacker
Doesn't check any security compliance boxes



Proactive cyber threat AI
Trends threats, providing info anchored to vetted cybersecurity sources as news breaks
Correlates your data with the latest threats
Generates actionable advice on how to defend, remediate, and mitigate
Checks multiple security compliance boxes - most importantly threat intel
Sign up for the waitlist
Generic wiki definitions
Out of date info on some threats without vetting, and most asks just trigger best practice lists
Doesn’t know anything about you or your data
Requires heavy prompting to get basic advice and refuses to answer if it mistakes you for a hacker
Doesn't check any security compliance boxes



See how much time you can save
Fletch surfaces the 5% of threats most likely to impact you right now. You’ll have every detail about the threat, what to do about it and what to say.
Sign up for the waitlist
Learn
How Fletch’s AI engine works
Customer stories
Use cases
See how much time you can save
Fletch surfaces the 5% of threats most likely to impact you right now. You’ll have every detail about the threat, what to do about it and what to say.
Sign up for the waitlist
Learn
How Fletch’s AI engine works
Customer stories
Use cases
See how much time you can save
Fletch surfaces the 5% of threats most likely to impact you right now. You’ll have every detail about the threat, what to do about it and what to say.
Sign up for the waitlist
Learn
How Fletch’s AI engine works
Customer stories
Use cases
See how much time you can save
Fletch surfaces the 5% of threats most likely to impact you right now. You’ll have every detail about the threat, what to do about it and what to say.
Sign up for the waitlist
Learn
How Fletch’s AI engine works
Customer stories
Use cases
Your specialized cyber threat AI
Your specialized cyber threat AI
Proactive cyber threat AI
Trends threats, providing info anchored to vetted cybersecurity sources as news breaks
Correlates your data with the latest threats
Generates actionable advice on how to defend, remediate, and mitigate
Checks multiple security compliance boxes - most importantly threat intel
Sign up for the waitlist






Generic wiki definitions
Out of date info on some threats without vetting, and most asks just trigger best practice lists
Doesn’t know anything about you or your data
Requires heavy prompting to get basic advice and refuses to answer if it mistakes you for a hacker
Doesn't check any security compliance boxes
Proactive cyber threat AI
95% of your teams’ time is wasted working on non-priority work. Fletch generates your short list of what to prioritize daily. And, best of all, it fits right into your existing workflows.
Prioritize
your daily cybersecurity work
with the world's first
Cyber Threat AI
Sign up for the waitlist
Fletch's Trending Engine
Trends the threat landscape
Fletch's Correlation Engine
Maps and correlates active threats to your data
Fletch's Advisor Engine
Act on the advice Fletch gives you
Fletch's Trending Engine
Trends the threat landscape
Fletch's Correlation Engine
Maps and correlates active threats to your data
Fletch's Advisor Engine
Act on the advice Fletch gives you
Fletch's Correlation Engine
Only 5% of threats are likely to impact you right now. The question is: which 5%.
Fletch knows.
Only 5% of threats are likely to impact you right now. The question is: which 5%.
Fletch knows.
*Source: Fletch 2024 Report



